As the world becomes increasingly digital, threats of cyber attacks loom over businesses and people. Be it ransomware, phishing schemes, or high-level data breaches, cybercriminals keep on coming up with new tactics to exploit weaknesses. As more organizations look for ways to secure their operations, data, and reputation, security is at the top of everyone’s list. However, building a cybersecurity infrastructure is an expensive, technically intensive, and highly maintenance-intensive project, one too expensive for most small to medium-sized businesses. SECaaS, or Security as a Service, is the game-changer, bringing security services over the cloud, and eliminating costly, on-premise setups.
Third-party experts who outsource their cybersecurity functions can provide scalable, real-time protection according to the needs of business firms. SECaaS is becoming a key part of IT strategies nowadays for the ease and efficiency it gives and has found acceptance in all types of industries.
Evolution of Cybersecurity
The field of cybersecurity has drastically changed over the decades. From the early days of computing, the focus was on protecting physical systems and standalone networks. In those days, when threats were not as sophisticated or frequent, firewalls, antivirus software, and basic password protection were enough.
The internet brought in a new wave of vulnerabilities. Business houses started connecting digitally while expanding their digital footprints with e-commerce, cloud services, and remote work models. Cyber attacks became much more complex by targeting people rather than systems. Phishing scams, social engineering, and ransomware began to pop up as challenging tasks.
Traditional cybersecurity solutions were not able to cope with the pace of change using on-premise hardware and software. Those systems were also expensive and required a lot of time in maintenance and updates. This created opportunities for cloud-based cybersecurity solutions, where businesses could avail flexible, on-demand security.
SECaaS is today the future of this evolution. Cloud technology will allow providers to offer advanced analytics and automation that enable proactive, real-time threat detection and response. This marks an important point in using SECaaS in modern, turbulent digital landscapes for meeting dynamic security needs.
Main Components of Cyber Security as a Service
A general term, SECaaS describes a broad spectrum of solutions and tools designed to safeguard businesses from cyber threats. Some of its primary components include:
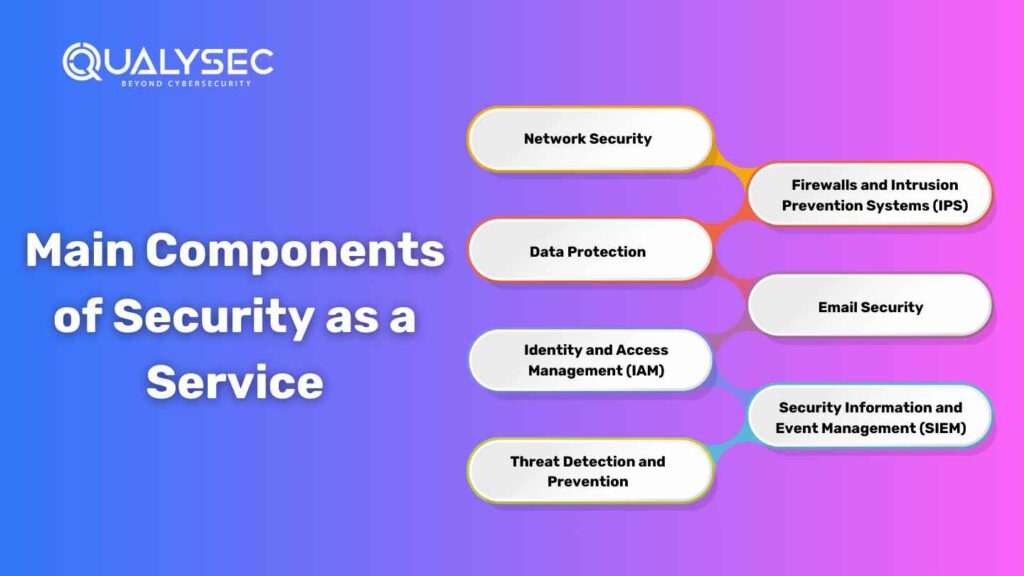
- Network Security: Prevents unauthorized access to internal networks, monitors network traffic, and blocks potential threats while ensuring the integrity and safety of the internal network. The most commonly used tools are VPNs and secure web gateways.
- Data Protection: Sensitive information is to be encrypted, ensure safe data storage, and a backup service is offered. Most often, DLP systems are integral parts of such solutions in attempts to prevent any accidental leaks or theft.
- Identity and Access Management (IAM): Useful in managing user identities and controlling access to important systems. The key feature within this is MFA. It includes SSO and RBAC within this package too.
- Threat Detection and Prevention: Machine learning and behavioral analytics for detecting anomalies and mitigating threats before they can escalate. This includes malware, zero-day attacks, and insider threats.
- Firewalls and Intrusion Prevention Systems (IPS): Acts as a shield against external attacks, protecting endpoints and other critical network components from unauthorized intrusions.
- Email Security: This prevents phishing, spam, and malware that is often used to gain entry through emails, which are still one of the most common entry points for cyberattacks.
- Security Information and Event Management (SIEM): This deals with real-time data analysis and logging to effectively monitor and respond to security incidents.
All these elements combined provide broad protection customized to the distinct nature of each organization.
Speak with an expert now to discuss your cybersecurity needs!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Advantages of Security as a Service
Due to its numerous advantages, SECaaS has gained huge popularity among organizations around the globe. These include:
- Cost Economy: SECaaS does not require expensive hardware, software, and dedicated in-house cyber security teams. Instead, it is offered to all kinds of organizations, small, medium, or large, using subscription-based pricing models.
- Scalability: Whether it is a small startup or a multinational corporation, the scaling of SECaaS solutions is beyond businesses’ needs. It helps organizations be adaptable and adapt to changes in security requirements without the necessity of reworking the systems in place.
- Access to Expertise: SECaaS providers have cybersecurity experts updated on the latest threats and technologies. The level of expertise is unaffordable for most small businesses.
- 24/7 Monitoring and Support: It ensures that all potential threats are detected and resolved in good time, hence lessening downtime and damage.
- Incident Response Faster: In the event of a breach, security as a service provider can be swift with pre-defined protocols that contain the threat before it gets out of hand.
- Compliance and Risk Management: SECaaS makes it easier to handle stringent regulatory environments. The provider guarantees adherence to industry compliances, including GDPR, HIPAA, and PCI-DSS.
Types of Security as a Service Solutions
Security as a Service (SECaaS) specializes in various types of solutions based on different security requirements:
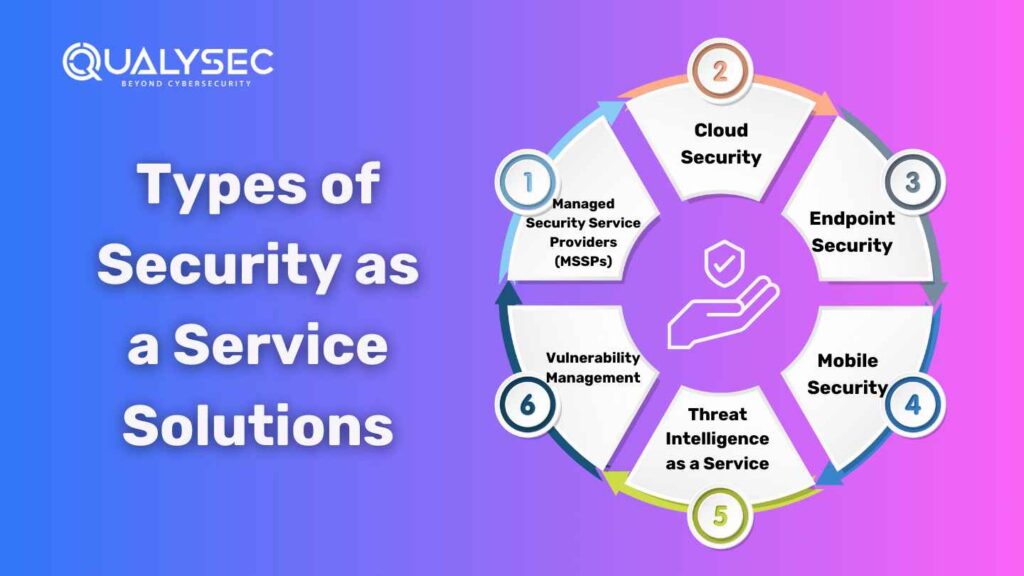
- Managed Security Service Providers (MSSPs): MSSPs provide end-to-end security management with threat detection, real-time monitoring, and incident response. Such services benefit companies that lack house skills or other infrastructure and make it possible to guard continuously.
- Cloud Security: This involves safeguarding the cloud-hosted data, applications, and infrastructures. In other words, cloud security applies to encrypt access control, and real-time monitoring processes. This makes it necessary for businesses to rely greatly on cloud computing systems.
- Endpoint Security: With remote work and increased IoT devices, it has become a pressing need for all to pay close attention to endpoint security. Such services enable the protection of laptops, smartphones, and all other single endpoints from malware and ransomware attacks.
- Mobile Security: App vulnerabilities and unsecured networks are quite common mobile dangers, and hence, mobile security comprises solutions such as secure application usage and encryption on a network.
- Threat Intelligence as a Service: This service enables companies to know the emergent cyber threats. It provides real-time analysis of data in the prediction and prevention of an attack, thereby enabling organizations to stay proactive.
- Vulnerability Management: Vulnerability management ensures that weaknesses within systems and applications are identified and prioritized for addressing critical flaws so that organizations do not get exposed to those risks.
These solutions allow organizations to implement a multi-layered approach to security and hence protect themselves from evolving cyber threats. Any organization can choose services that best align with their needs; this means the security will be strong, scalable, and easily managed.
Best Practices for Implementing Security as a Service
The benefits of Security as a Service (SECaaS) can be fully realized only by following the following best practices:
- Choose the Right Provider: Choose a good and reliable SECaaS provider. Assess experience, reputation, and their ability to meet your organization’s specific security needs. Check reviews, certifications, and compliance with industry standards like GDPR or HIPAA.
- Risk Assessment: Assess your vulnerabilities before or before implementing a SECaaS product, and figure out areas that need protection. Before that, it will be easy to select the most suitable SECaaS solutions to tackle your unique risks.
- Define Clear SLAs: Define expectations, responsibilities, and response times in SLAs. Ensure they cover critical aspects like uptime guarantees, data handling policies, and protocols for managing incidents.
- Integrate SECaaS with Existing Systems: Ensure seamless integration with your IT infrastructure to avoid disruptions. Work with the provider to ensure compatibility with existing software, hardware, and workflows.
- Regularly Update and Audit Security Measures: Cyber threats are always evolving. Review and evaluate the performance of your SECaaS solutions, updating configurations and audits, to stay current on their effectiveness and standards.
- Educate Employees: Human error is still one of the main sources of insecurity. Train your employees on security best practices to be aware of phishing attempts, for example, or the proper ways of handling sensitive data.
By adopting such practices, the organizations can effectively implement SECaaS and build an effective cyber security framework. Proper planning, collaboration with a trusted provider, and continued vigilance can ensure long-term security and resilience against cyber threats.
Limitations and Challenges of SECaaS
SECaaS has many advantages. However, business organizations should know its challenges as well:
- Dependence on a Vendor: Being dependent on a third-party vendor who faces downtime suffers data breaches or shuts down their service is very dangerous. Organizations may struggle to change their provider or retrieve their security functions.
- Data Privacy Issues: Storing sensitive data on cloud servers, especially across different jurisdictions, can expose businesses to privacy and compliance risks. Adhering to regulations like GDPR and HIPAA can become complex depending on the provider’s server locations.
- Integration Complexities: Integrating SECaaS with legacy systems may require significant technical customization, making it difficult for some organizations to seamlessly incorporate it into their existing infrastructure.
- Lack of Visibility: Outsourcing security functions can result in a loss of control and visibility, leaving organizations feeling disconnected from their cybersecurity processes.
- Cost Escalation: Although SECaaS is generally cheaper than traditional methods, the subscription costs for advanced features can increase over time, possibly exceeding the budgets of smaller organizations.
In addressing these challenges, the right vendor should be chosen, regular cyber security audits and penetration testing conducted, and a strong incident response plan created.
Latest Penetration Testing Report

Case Studies of SECaaS in Action
Real-world examples showcase the effectiveness of SECaaS:
- Small Business Overcoming Ransomware Attacks: A startup implemented SECaaS for 24/7 threat monitoring and real-time response, preventing major losses during a ransomware attack and ensuring continued operations.
- Enterprise Managing Multi-Cloud Security: A large global corporation adopted SECaaS to streamline security across its multiple cloud platforms, enhancing protection and compliance across its network.
- Healthcare Provider Achieving Compliance: A hospital applied SECaaS to meet its strict HIPAA requirements, ensuring the confidentiality and privacy of patient information but adhering to the industry standard.
Emerging Trends in SECaaS
With new technologies, SECaaS is changing shapes and shapes up the emerging cybersecurity challenges:
- AI and Machine Learning Integration: AI and machine learning are bolstering advanced threat detection and response by using analytics to detect anomalies and let the security processes be automated.
- Zero Trust Security Models: The shift toward Zero Trust, which emphasizes continuous verification and restricted access, is gaining traction, particularly with remote workforces.
- Cyber Insurance Partnerships: SECaaS providers are partnering with cyber insurance companies to offer businesses comprehensive protection, including financial coverage for breaches.
- Industry-Specific Solutions: SECaaS is becoming more tailored to industries like finance and healthcare, addressing sector-specific challenges and regulatory needs.
SECaaS Metrics and ROI Measurement
Organizations will also measure whether the SECaaS delivers value by the following:
- Incident Response Time: The faster the threats are detected, and their effects are mitigated indicates successful SECaaS.
- Downtime Reduction: Less operational disarrays due to enhanced security through SECaaS signify effectiveness.
- Cost Savings: The comparative ability to save in-house cybersecurity costs on hardware, software, and personnel between in-house and SECaaS is another factor.
- Regulatory Compliance: SECaaS keeps organizations current with necessary government and international regulations and policies regarding protection, such as GDPR, PCI-DSS, and HIPAA, and these are the foundation of avoiding punishment.
SECaaS versus Traditional Cybersecurity
SECaaS has several benefits over traditional in-house cybersecurity, including:
- Scalability: SECaaS is easy to scale; an organization’s business needs could be easily adjusted without involving expensive hardware upgrades.
- Cost-Effectiveness: SECaaS typically follows a subscription-based pricing model, which is more reasonably priced compared to what the huge investment in building infrastructure and the long-term maintenance costs mean for traditional security.
- Expertise Access: SECaaS providers provide access to specialized cybersecurity expertise that allows even smaller businesses access to high-level professionals without the need to build an internal team.
Conclusion
SECaaS has transformed the face of business by approaching cybersecurity with scalable, cost-effective, and expert-driven solutions. Organizations are now able to concentrate on their core operations while still being protected robustly against these changing cyber threats by outsourcing their critical security functions to specialized providers.
The flexibility and variety of SECaaS solutions, such as managed security, cloud security, endpoint protection, and vulnerability management, allow it to be adapted to the needs of businesses of any size. Therefore, this access opens the doors for even the smallest organizations to implement enterprise-grade cybersecurity measures.
However, like any service, SECaaS has challenges. It is vendor-dependent, and issues surrounding data privacy and integration require careful consideration. Businesses have to ensure due diligence in the choice of a provider, establishment of clear SLAs, and regular audits to overcome these limitations effectively.
SECaaS will change with technology. The inclusion of AI, machine learning, and automation will help service providers offer quicker and more precise threat detection and response. Increased demand for innovative and specialized SECaaS solutions will arise from the expansion of IoT devices, 5G networks, and multi-cloud strategies.
The best ways to achieve maximum benefits from SECaaS with the least possible risk happen to be through proper risk assessments and easy integration, as well as continuous employee training. This is because threats in cyberspace are developing and evolving at such a rate that one cannot afford to remain behind in investing in security as a service.
SECaaS, therefore, is a pioneering approach to cybersecurity that will help businesses cope and thrive with such constant challenges. With effective strategies and partnerships, organizations can utilize SECaaS to design a safer, more productive digital environment.



































































































































































































































































































































0 Comments