If you invest one dollar in cybersecurity and do not perform “Penetration Testing”, you are doing something wrong. To limit the danger of cyberattacks nowadays, contemporary firms must do extensive and regular pen testing.
Facts, numbers, forecasts, and data assist CISOs and cybersecurity professionals comprehend industry dynamics. Here are some additional stats you should know about:
- According to Cybersecurity Ventures, the worldwide pen testing product and service industry will approach $5 billion per year by 2031.
- This year, 92 percent of firms in the United States and Europe boosted their overall IT security spending, with 85 percent increasing their pen testing budgets.
- According to certain predictions, the worldwide pen testing industry will expand by more than 24 percent by 2026.
This blog will shed light on everything you need to know about pen testing. We’ll cover what pen-testing is, how it works, why you need it, and tips to choose the best company. Continue reading to learn more.
What is Cyber Security Penetration Testing?
Cyber security penetration testing is analyzing an application’s security and exploiting discovered vulnerabilities and security risks inside an asset such as a website, server, database, network, or mobile application to determine the degree of the threat to security.
Furthermore, during a pen test, a tester discovers security flaws in an application, network, or system and assists you in addressing them before attackers find and exploit them. Pen testing is an essential step for every application or business owner.
What is the Objective of Performing a Penetration Test?
A penetration test’s purpose is to determine by the sort of allowed activity and your compliance requirements. Organizations can benefit from pentesting in the following ways:
- Determine the viability of specific assault pathways.
- Identify high-risk vulnerabilities that come from lower-risk vulnerabilities exploited in a certain way.
- Highlight flaws in automated network or application vulnerability screening software that go unnoticed.
- Test your network’s defenses and your organization’s capacity to identify, respond to, and halt attacks.
- Contextualize increasing investment in information security policies, processes, personnel, or technology.
- Comply with compliance standards. Regular pen testing is also required by the Payment Card Industry Data Security Standard (PCI DSS).
- Validate the new security procedures put in place to prevent similar attacks.
Why is Penetration Testing Important?
Here are a few reasons why companies should do a penetration test on themselves:
-
Maintains Confidentiality
A security breach can compromise accounting data, reducing the organization’s income. Cyber security penetration testing as a service not only helps corporations discover the length of time it takes an attacker to penetrate the system but also confirms the companies’ readiness to prepare security teams to re-mediate the danger.
-
Ensures Secured Settings
If an organization’s security staff is doing a good job and is confident in their efforts and ultimate outcomes, penetration reports will confirm that. Additionally, having an outside party operate as a confirming agent of whether the system’s security gives a view that does not reflect internal preferences. It aids in the identification of system deficiencies.
-
Retains Reputation and Customer
The importance of reputation cannot be overstated. It keeps the world turning and is the primary focus of most enterprises. A company’s reputation may either make or break it. A one news story about a company’s data leak may demolish all the reputations you’ve created over time.
-
Evaluates Risk
The concept of risk assessment discloses the risks and their consequences. You may do it yourself or hire an expert for an impartial risk assessment. Furthermore, the risk assessment should produce a set of priority objectives that you must achieve to safeguard your firm.
What are the Methods of Penetration Testing?
Let’s get into a thorough understanding of the techniques of pen testing:
-
White Box Testing
The primary goal of White Box testing is to validate the code and internal structure of the product being tested. A tester is inspecting the input-output processes here, emphasizing the product’s inner workings.
-
Black Box Testing
Behavioral testing, often known as Black Box testing, is a process in which the tester is unaware of what they are testing. These tests are typically functional, and websites are examined with a browser, some data is entered, and testers evaluate the results.
-
Grey Box Testing
Grey Box testing is an amalgamation of White Box and Black Box testing. The tester hopes to identify all potential code and functionality flaws using this strategy. At this point, a professional can test the end-to-end functions.
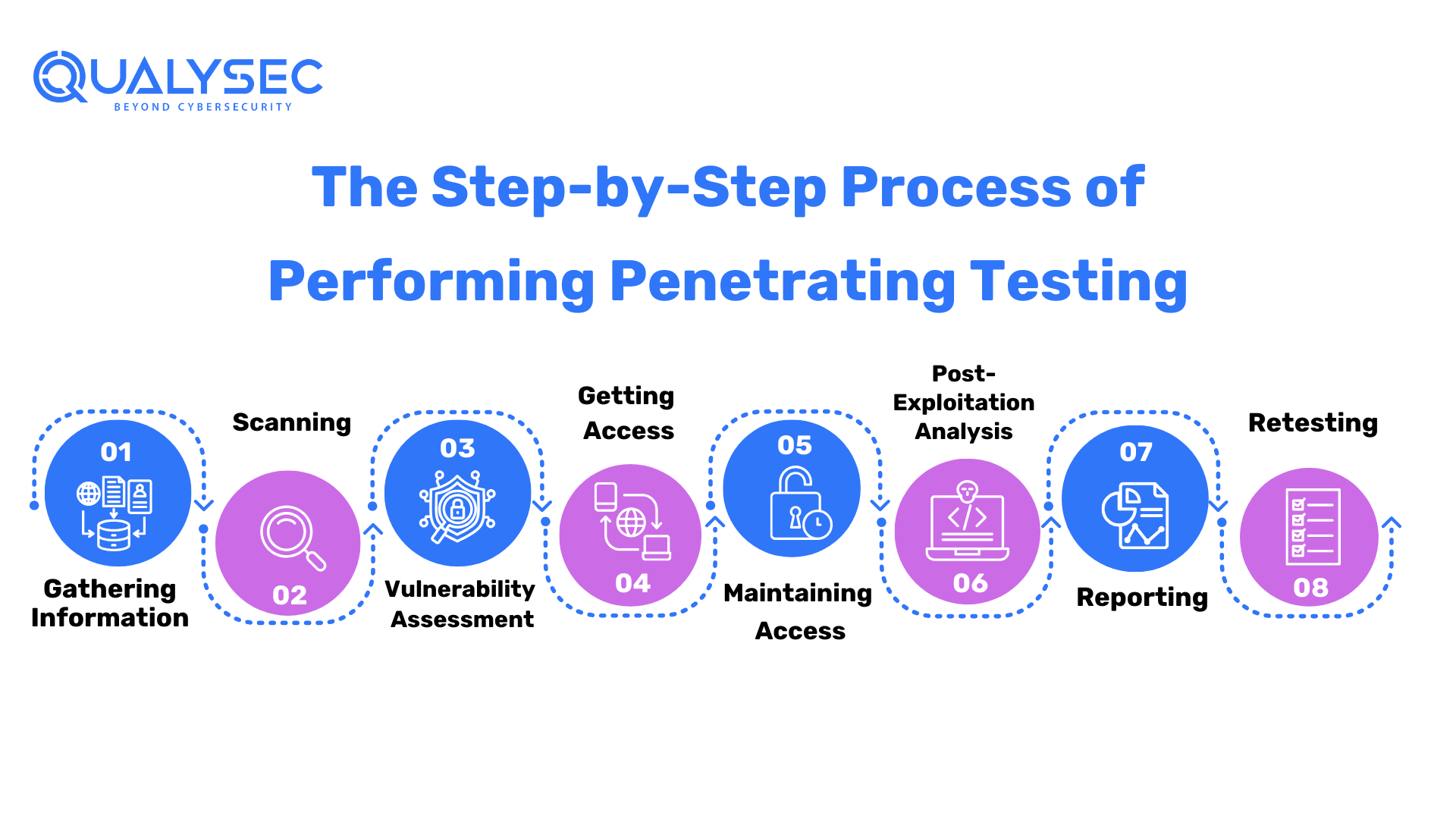
The Step-by-Step Process of Performing Penetrating Testing
-
Gathering Information
Gathering reconnaissance or Open Source Intelligence (OSINT) is a critical initial step in pen testing. A pen tester’s job is to obtain as much information as possible about your business and prospective targets for exploitation. Furthermore, depending on the sort of pen test you choose, your penetration tester may have varied degrees of knowledge about your business to expose vulnerabilities and entry points in your environment.
-
Scanning
The following stage determines how the target application will react to intrusion attempts. This is usually done with:
- Static analysis: Inspecting an application’s code to estimate how it will behave while operating.
- Dynamic analysis: The process of inspecting an application’s code while executing. This method gives a real-time picture of an application’s performance.
-
Vulnerability Assessment
A vulnerability assessment is performed to obtain preliminary knowledge and discover potential security flaws that might allow an outside attacker to access the environment or technology to be examined. In contrast, a vulnerability assessment should never be used in place of a penetration test.
-
Getting Access
The goals of attackers range from stealing, modifying, or destroying data to shifting cash or hurting a company’s reputation. Furthermore, pen testers decide which tools and tactics to use to access the system, whether through a flaw like SQL injection or by malware, social engineering, or anything else.
-
Maintaining Access
Once pen testers have gained access to the target, their simulated attack must remain connected long enough to achieve their aims of data exfiltration, modification, or abuse of functionality. It is necessary to demonstrate the possible impact.
-
Post- Exploitation Analysis
Following the completion of the exploitation phase, the purpose is to document the tactics utilized to access your organization’s critical information. After completing the pen testing recommendations, the tester should clean up the environment, reconfigure whatever access they have to breach the environment and prevent future unwanted entry into the system by all means required.
-
Reporting
Reporting is the most important element of a pen test. It is where you will receive written suggestions from the cyber security penetration testing business and have the option to discuss the report’s findings with the ethical hacker(s). The report should include how entry points were discovered during the threat modeling phases and how to address security concerns uncovered during the exploitation phase.
-
Retesting
Once vulnerabilities have been fixed, you can choose whether to retest your systems to ensure that the patches were effective and to see whether any new vulnerabilities were introduced due to the remediation. However, successful, thorough pen tests should offer business leaders clear, intelligible, and actionable results and provide corporate technical teams with an explicit knowledge of the security threats on their targeted systems.
What are the Types of Penetration Testing?
Here are major types of cyber security pen testing you should know about:
-
Application Penetration
This security penetration test focuses on vulnerabilities in your apps, from conception and development to implementation and use. Assessors check for vulnerabilities in the apps’ security protocols, such as missing updates or exploited gaps in outwardly exposed web applications, internal network applications, and end-user devices and remote systems.
-
Wireless Networks Penetration
Wireless pen testing, also known as network security testing, is a way of determining the susceptibility of a computer network to infiltration. A fault might cause this vulnerability in a computer system or by a hostile hacker assault.
-
Social Engineering Penetration
Social engineering pen testing focuses on the organization’s people and procedures and their security risks. It is done by ethical hackers who attempt standard social engineering attacks in the workplace, such as phishing, USB dropping, and spoofing.
-
Client-Side Penetration
Client-side pen testing can reveal security flaws in client-side software such as web browsers, media players, and content production software packages. Attackers frequently compromise client-side software to get access to business infrastructure.
-
Mobile Application Penetration
The purpose of this pen testing is to identify and report flaws in mobile security to developers. Functional testing differs from security testing in scope. As the number of mobile devices and users has expanded, pen testing has developed dramatically, for example, android and iOS pen testing.
-
API Penetration
An application programming interface (API) is a collection of tools and standards that enable programs to communicate with one another. An API pen test is a method of detecting flaws in an application programming interface (API). API pen testing is a method of testing an application’s attack surface by emulating the behaviors of a malicious user.
-
Cloud Penetration
The cloud security penetration testing is a sort of security testing that looks for weaknesses in a cloud computing environment that hackers may exploit. Cloud pen-testing is an important component of a cloud security strategy since it identifies possible flaws in cloud security mechanisms.
What are the Best Practices of Penetration Testing in Cyber Security?
-
Establish Specific Goals
The first step in creating a secure test is to plan it out by defining its scope. This entails deciding on precise test goals and situations influencing the outcome. You could cover a whole network, certain apps inside that network, verify the security of your APIs, or even individual users that operate from home offices.
-
Choose an Experienced Pen Tester
At the very least, your pen testing service provider should meet the following requirements:
- Uses both automatic and manual ways to find vulnerabilities and advanced threats in your environment.
- Investigate how high-risk vulnerabilities can be exploited to assess the impact on your operating environment and the likelihood of a breach.
- Custom reports are generated that emphasize the risks of detected and exploited vulnerabilities and provide strategic mitigation, suggestions, and actionable insights.
-
Prioritize Pen Test Results
Now that we have all this information, it is time to act! Set up a team meeting with your security executives to identify which vulnerabilities require quick action. Your pen testers should provide you with the following:
- The method via which the flaws were found
- Possible effects if they are used
- The level of risk for each vulnerability
- Remediation guidance
The tester will utilize their technical knowledge to identify the most critical vulnerabilities. You should analyze their priorities and decide which ones influence your business most and address them first.
Tips to Choose the Best Penetration Testing Company
-
Assess Their Capabilities
Years of training, certification, and hands-on experience are required for pen testing. As a result, you must assess the abilities of the Pen testers you want to recruit. What you can do is as follows:
- Expertise: Cross-check their degree, certificates, and other credentials to assess their skills.
- Experience: More experience is always better. Check to see how experienced your Pen tester is.
-
Inquire About Reporting
Ensure the selected firm can present you with a thorough, easy-to-understand report. The data should also be updated as your systems change so that you always have a record of the most recent testing.
-
Look for a Strong Reputation
A good reputation is critical for any organization but extremely important for penetration testing firms. Do your homework and study feedback from previous customers. This will give you an idea of what to expect from the firm and whether or not they are a suitable fit for your organization.
-
Expertise in Compliance
A complicated set of compliance rules governs data security. A smart cyber security supplier knows and stays current with the ever-changing regulatory and legal landscape. Furthermore, they use their experience and knowledge to your organization and verify that you comply.
In Conclusion,
Penetration testing is a critical method in cyber security that finds and resolves vulnerabilities in a computer system, network, or application before malicious attackers may exploit them. It uses ethical hacking techniques to simulate real-world cyber-attacks, assisting organizations in improving their security posture and protecting sensitive data.
To protect against the increasing sophistication of cyber-attacks, businesses must prioritize comprehensive cybersecurity measures in this ever-changing digital world. When choosing a pen testing company, QualySec is a market leader.
QualySec provides a cutting-edge methodology and a team of highly skilled and certified professionals to conduct rigorous penetration tests tailored to the specific demands of businesses.
Because of their commitment to quality, client satisfaction, and an established track record, they are the #1 choice for organizations seeking proactive and effective cybersecurity solutions through pen testing. In the face of an ever-increasing cyber threat environment, businesses may strengthen their defenses and ensure a robust security architecture by collaborating with QualySec.
FAQs:
-
What is penetration testing in cyber security?
Penetration testing, often known as ethical hacking or pen testing, is a proactive and legal means of detecting computer system, network, or application faults. The goal is for ethical hackers to simulate a real-world cyberattack to find and fix vulnerabilities before malicious hackers can exploit them.
-
What is penetration testing in network security?
In network security, penetration testing analyzes the security of a computer network. This includes inspecting the network infrastructure, devices, and services for flaws that unauthorized users might exploit. Network pen testing includes scanning for open ports, checking for weak or default passwords, measuring the efficacy of firewalls, and detecting misconfigurations that may compromise network security.
-
What is web penetration testing?
Web penetration testing is a subset of penetration testing that focuses on web application security. It comprises testing both the front-end and back-end components of online applications for security flaws such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and other issues.
-
What is black box testing in cyber security?
Black box testing is a testing approach in cybersecurity in which the tester has little or no knowledge of the underlying workings of the system being reviewed. The tester investigates the system from the outside, looking for vulnerabilities, defects, and possible exploitation points. This method aids businesses in identifying the vulnerabilities of their system to real-world cyber-attacks.
-
What is website penetration testing?
Website penetration testing is concerned with determining a website’s security. This involves looking for vulnerabilities in the website’s architecture, server settings, and web application. Website penetration testing helps firms secure their online presence by fighting against threats like illegal access, data breaches, and other web-based assaults.


















































































































































































































































































































































0 Comments