In today’s world, where things are being developed at a fast rate, attackers have been coming up with new techniques to hack systems and steal data. It is really important to keep the systems updated and constantly checked. If an organization’s network isn’t assessed regularly then it is impossible to keep the network safe. Checking your network security is important and this has to be done in regular time intervals. A Thorough Network security assessment is essential so that the organization detects its weak points and in turn improves its security levels.
This blog aims to highlight the importance of network security assessment and also provides the ultimate guide on network security assessment.
Types of Network Security Assessment
There are two main ways to check network security: vulnerability assessment and penetration tests. These two techniques work together hand in hand.
- Vulnerability Assessments – A series of security checks of your company. They look at your network’s security from all angles. These tests are frequently done using automated tools and a report is generated indicating areas where your network can be more vulnerable. This kind of scan detects critical problems and identifies how to make the network safer. It lets you have a good perception of your business network and this can help you to direct your team’s efforts appropriately.
- Penetration Testing – This is done to give a thorough network check. It is an extended version of vulnerability assessment but it penetrates deeper into the systems network. The process of penetration is done using automated tools and more sophisticated tools to discover potential threats.
A Network security assessment involves both vulnerability assessment and penetration testing side by side. It is also termed VAPT Testing ( Vulnerability Assessment and Penetration Testing). Which discovers all the threats and issues related to one’s network. It is mandatory for firms that cannot compromise their digital assets or network. VAPT testing is done by firms with expertise in cybersecurity and penetration testing.
Different Network Security Devices
Network Security Devices are essential in providing a safe network for the organization. They minimize the risk of potential hacker attacks and these devices include:
1. Firewalls: A layer of security that acts as an initial line of defense before the data is transmitted or received on an organization’s network. There are two types of firewalls, hardware-based and software-based. The sole purpose is to block harmful data entering in the network.
2. Intrusion Detection Systems (IDS): IDS is also known for its detection of abnormal activity in the network. The process is executed by checking for logs and network packets entering the system.
3. Intrusion Prevention Systems (IPS): The main difference between IDS and IPS is the way the abnormal data packets are blocked. IPS not only blocks but also prevents harmful packets from entering into the system. IP addresses are blocked if there is a detection of abnormal activity.
4. Virtual Private Networks (VPNs): A VPNs main objective is to secure an open or a public network. VPNs enable remote users to access the internet or the network of the organization.
5. Proxy Servers: Proxy servers, secure the client-to-server connections in the given network. It filters and blocks harmful sites and ensures privacy for the user.
The above-provided network security devices act as the initial line of defense before anyone can access data from the given network. These devices help minimize the loss of data of the organizations. These also improve the network security of the organization.
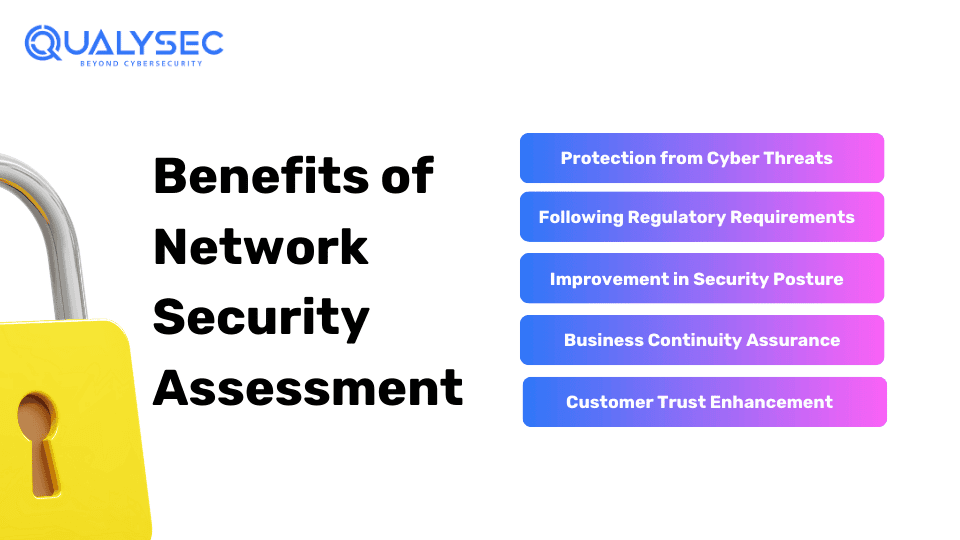
Benefits of Network Security Assessment
As there are many advantages to network security assessment, further an audit contributes to the comprehensive security and performance of a business. Here’s a look at these benefits in simpler terms:
Protection from Cyber Threats
A network security assessment will give a better understanding of some of the threats to the network such as identifying the weaknesses and risks of the network.
Following Regulatory Requirements
Several industries, such as banking and IT, have their rules in place with standard levels of security (i.e., GDPR and PCI DSS). Frequent evaluation helps them to reveal the weakest parts of the system’s network. This helps the organization to keep their user’s data safe and protected.
Improvement in Security Posture
Assessments are done to analyze the strength of the security and its current level. Thus it allows the organization to find weak spots in the existing system. These include the implementation of best security testing practices and new software updates as these are essential for the improvement of security posture.
Business Continuity Assurance
Evaluations play a crucial role, as they enable businesses to face risks and overcome challenges. Reduction of incident impact shortens downtime and prevents losses. These losses are avoided which could have resulted from an interruption in normal operations.
Customer Trust Enhancement
Regular security assessments are signs of the company’s dedication to protecting client data from any leakage which then positively impacts clients’ confidence. Without this, a business cannot experience optimum customer relationships which could be a huge disadvantage.
Feel free to look into the whole structure of a sample report. Click and download the sample right now!
Latest Penetration Testing Report

How Qualysec Pentest helps you with Network Vulnerability Assessment
Qualysec is famously known for its proficiency in discovering security problems and threats. Thus they are the leading company that provides network security assessment. They can help you with many services such as VAPT by advising on security and assisting you if there is a security issue.
Qualysec, with its primary office in India, holds international recognition as a leader in the cybersecurity industry. They possess extensive knowledge and skills in this role. When they discover a threat, the team at Qualysec develops a remedy to tackle it, thereby improving the company’s security.
At Qualysec, the pen tester team is capable enough to track and neutralize cybersecurity events that pose any kind of risk. This enables them to be the best in the provision of security solutions. They offer such services through the use of cutting-edge technologies such as:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
Qualysec has its tools, it follows the rules of the industry and gives instructions in simple words so that the clients can apply the solutions to fix their problems. They do so as well by drawing up a good plan that will be based on the knowledge gained and the results.
Qualysec’s solution is a perfect choice for firms that have to comply with strict regulations or customers who want to show their dedication to privacy and security to clients or suppliers. Regular security testing enables firms to identify those weaknesses immediately and correct them before hackers exploit them.
Qualysec offers top-of-the-line penetration testing for web applications, mobile apps, cloud, IoT devices, etc. along with source code review and AI/ML penetration testing. Contact Us Now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Some popular network security testing tools
Network security assessment tools used for testing network security are as follows:
- Nmap: Cybersecurity professionals use this Linux utility for network mapping and port scanning, two essential tasks. It serves to identify bugs and find security loopholes.
- Wireshark: Wireshark, an assessment tool, captures and displays data sent over a network. It’s an excellent tool for backtracking and troubleshooting network issues and security.
- Metasploit: We use Metasploit to detect and fix network weaknesses, which could potentially lead to a hacker breaching the network’s security. The objective is not to surpass the defenders next time (even though this might be a hidden aim) but rather to assess and use the gaps in network systems for better protection.
- Burp Suite: One of the key roles is to ensure the security of web applications. This is one of the key aspects of the tool ensuring the provision of remedies for web app security complications.
- OpenVAS: OpenVAS stands for Open Vulnerability Assessment System and it is a tool that helps to do vulnerability management and to audit your network systems. It does not let attackers take advantage of networks, thus keeping the network safe and risk-free.
Conclusion
Lastly, as the attackers are constantly developing new methods, keeping the network secure is a top priority is essential. Frequent security checks are essential as they provide a secure network. These methods allow businesses to determine and fix system loopholes that hackers could exploit. In addition, a report must be given to the organizations with the assessment outcome and also suggest how to secure the security of their networks at the ground level.
Qualysec has a good history of helping clients and giving cybersecurity services in many industries like IT. Their skills have helped clients find and fix vulnerabilities, stop data breaches, and make their overall security better.
FAQ’s
What is Network Security Testing?
Network security testing is the process of evaluating the security posture of a network infrastructure to identify vulnerabilities and assess its ability to withstand potential attacks.
Why is Network Security Testing Important?
Network security testing is crucial for several reasons:
- Identifying Vulnerabilities
- Improving Security Posture
- Compliance
- Risk Management
- Incident Response Preparedness
What is a Security Assessment in a Computer Network?
A security assessment in a computer network is a comprehensive evaluation of the network’s security posture. It involves identifying, analyzing, and prioritizing security risks and vulnerabilities in the network infrastructure, systems, and applications.
































































































































































































































































































































0 Comments