A vulnerability assessment testing is a set of weaknesses in an IT system at a point in time to show the vulnerabilities to be resolved before hackers use them. Humans make mistakes, and since software is written by humans, it is always going to contain bugs.
Most of these bugs are harmless, but some can become exploitable weaknesses, compromising the security and usability of the system. This open door makes it prime territory for vulnerability assessment to come in and help organizations discover vulnerabilities like SQL injection or cross-site scripting (XSS) that hackers could exploit.
Let us discuss the step-by-step process of how to do vulnerability assessment penetration testing.
Why are Vulnerability Assessments Important?
In 2022, there were over 25,000 new software vulnerabilities discovered and disclosed publicly. To outsiders, this number seems alarming. But those communities familiar with cyber security are no longer easily shocked by such numbers. Sure, not all 25,000 will find their way into any organization’s systems. But all it takes is one for immeasurable damages to ensue.
Hackers are hounding the Internet for these vulnerabilities, and if you do not wish your company to be a victim, you, therefore, have to be the first to know about it. Be proactive in the management of your vulnerabilities: An important first step toward this proactive posture is having a vulnerability assessment.
Vulnerability Assessment vs Penetration Test
It’s not difficult to mix up vulnerability testing and penetration testing. Most security firms provide both, and it’s easy to blur the boundaries between them.
The simplest way to distinguish between these two options is to observe how the heavy lifting in the test is performed. A vulnerability assessment is an automated test, i.e., a tool does all of the heavy lifting, and the report is created at the end. Penetration testing is a manual process based upon the knowledge and expertise of a penetration tester to discover vulnerabilities within an organization’s systems.
The best practice would be to combine automated vulnerability tests with periodic manual penetration testing to provide more robust system protection. But not all companies are created equal, and of course, where security testing is required, their requirements are dissimilar. Therefore, if you’re just beginning and unsure as to whether or not you need to conduct a vulnerability assessment versus a penetration test, we have created a useful guide on security testing that responds to this dilemma.
What is the Purpose of a Vulnerability Assessment?
There is a significant difference between believing you’re at risk from a cyber attack and knowing specifically how you’re at risk, because if you don’t know how you’re at risk, then you can’t stop it. The objective of a vulnerability assessment is to bridge this gap. A vulnerability assessment scans some or all of your systems and creates a detailed vulnerability report. You can use the report to repair the issues discovered to prevent security breaches.
Also, with more and more companies relying on technology to get their daily chores done, threats in cyberspace, such as ransomware, can make your business grind to a complete halt within minutes. For instance, additional SaaS clients nowadays need regular vulnerability scans, and having evidence of security testing will also help you bring in more business.
Latest Penetration Testing Report

Vulnerability Assessment Tools
Vulnerability scanning is an automated activity that is carried out by scanners. This means it is available to everyone. Most of the scanners are targeted at cyber security professionals, but there are products suited for IT managers and developers in organisations that don’t have security teams.
The vulnerability scanner tools are of many types: some are good at network scanning, others at web applications, API security, IoT devices, or container security. Others assist with attack surface management. Small business owners will find a single scanner that scans all or the majority of their systems. Large organizations with intricate networks might rather integrate several scanners to obtain the level of security they need. See our vulnerability scanning guide to discover more regarding the process of vulnerability scanning and which scanner is best suited for your company.
Steps to Conduct a Vulnerability Assessment
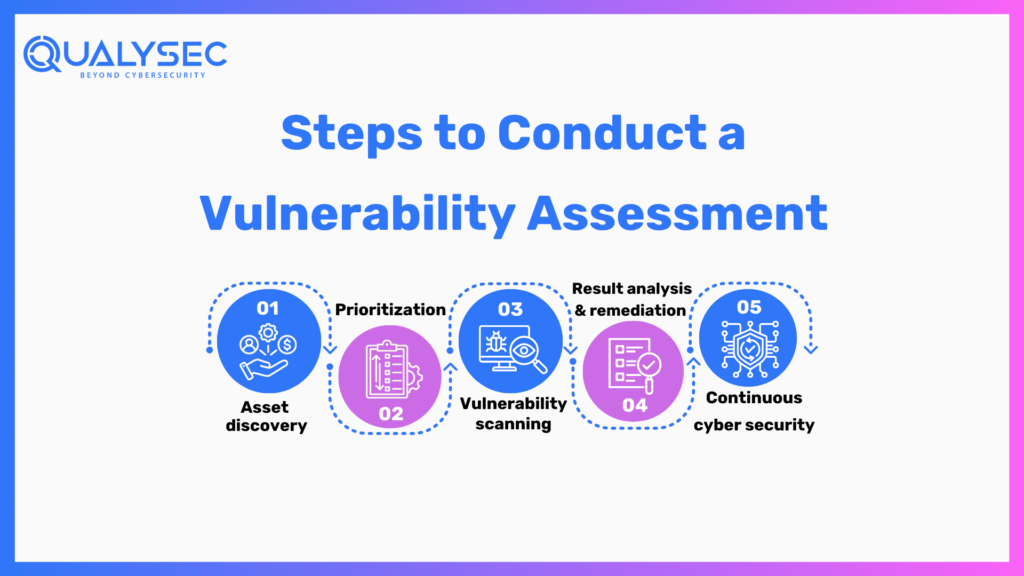
With the proper tools at your disposal, you can conduct a vulnerability assessment penetration testing by following these steps:
1. Asset discovery
You must first determine what you wish to scan, which is not always as easy as it appears. Perhaps the most prevalent cybersecurity issue that organizations encounter is a lack of insight into their digital infrastructure and the devices that are connected to it. Some of the reasons for this are:
- Mobile Devices: Smartphones, laptops, and so forth are intended to disconnect and reconnect repeatedly from the office, employees’ residences, and other remote sites.
- IoT Devices: IoT devices belong to corporate infrastructure but could be connected mainly to mobile networks.
- Cloud-Based Infrastructure: Cloud services providers simplify spinning up new servers on an as-needed basis without the need for IT.
It can be difficult just to know what various teams are posting online, or modifying, at any particular moment. This visibility problem is a problem because it’s impossible to lock down what you can’t see.
Fortunately, the discovery part of this process can be automated to a great extent. For instance, certain contemporary vulnerability scanning tools can discover public-facing systems and link directly to cloud providers to find cloud-based infrastructure. Discover more about asset discovery tools or experiment with our interactive demo below to observe it in action.
2. Prioritization
Once you know what you’ve got, the next thing is if you can afford to scan all of it for vulnerabilities. In an ideal world, you’d be scanning your vulnerability assessment regularly across all your systems. Vendors, however, tend to charge per asset, so you can use prioritization where the budget cannot pay for every asset the company holds.
Examples of where you might want to prioritize include:
- Internet-facing servers
- Customer-facing applications
- Databases holding sensitive data
It’s also interesting to note that two of the most prevalent vectors for untargeted or mass attacks are:
- Internet-facing systems
- Employee laptops (through phishing attacks)
So, if you can’t do anything else, attempt to get these addressed in the same order.
3. Vulnerability scanning
Vulnerability scanners are intended to locate known security vulnerabilities and instruct users on how to correct them. Since the vulnerabilities are generally made public, ample information can be found concerning vulnerable software. The scanners apply such information in recognizing vulnerability management software and devices in the infrastructure of an organization. The scanner sends out probes first to the systems for determining:
- Open ports & running services
- Software versions
- Configuration settings
From this data, the scanner can usually detect numerous known vulnerabilities within the system being scanned.
Moreover, the scanner fires particular probes to detect individual vulnerabilities that can be tested only by firing a safe exploit that confirms the weakness exists. Such probes can detect shared vulnerabilities like ‘Command Injection‘ or ‘cross-site scripting (XSS)‘, or default usernames and passwords used for a system.
Depending on the infrastructure that you’re scanning (and particularly how expansive any websites are), the vulnerability scan may take anywhere from a few minutes to a few hours.
4. Result analysis & remediation
Upon finishing the vulnerability scan, the scanner presents an assessment report. In reading and creating remediation plans based on this report, you must consider the following:
- Severity: A vulnerability scanner should categorize a possible vulnerability according to its severity. When making remediation plans, prioritize the most severe ones first, but don’t leave the rest in the dark forever. Hackers can string multiple mild vulnerabilities together to form an exploit. A good vulnerability scanner will provide recommendations on when to patch each one.
- Vulnerability Exposure: Remembering the prioritization above – not all vulnerabilities are on public-facing systems. Internet-facing systems are more likely to be exploited by any random attacker scanning the internet, making them a higher priority for remediation. After that, you’ll want to prioritize any employee laptops with vulnerable software installed. Additionally, any systems that host particularly sensitive data or could adversely affect your business may need to be prioritized ahead of others.
In most instances, there is a publicly available patch to address an identified vulnerability, but it oftentimes does necessitate a change in configuration or other workaround as well. Following a fix application, it is also wise to rescan the system to guarantee the fix has been applied effectively. If it has not, the system remains susceptible to being exploited. Also, if the patch introduces any new security problems, including security misconfigurations (as rare as they are), this scan can identify them and enable them to be fixed as well.
When you then look at how many vulnerabilities exist and then consider the overall complexity of the typical commercial digital infrastructure, then you can understand the potential scope for exposure and exploitation.
5. Continuous cyber security
A vulnerability scan gives you a snapshot at a point in time of the vulnerabilities within an organization’s digital footprint. New deployments, configuration updates, newly revealed vulnerabilities, and other variables can swiftly render the organization vulnerable all over again. For this reason, you should turn vulnerability management in cyber security into an ongoing process, not a one-time event. Learn more about best practices for the frequency of vulnerability scanning.
Because most vulnerabilities are introduced at the time that software is developed, the leading software development businesses incorporate automated vulnerability scanning into their continuous integration and deployment (CI/CD) pipelines. That way, they can detect and remediate vulnerabilities before the release of software, preventing its potential exploitation as well as developing and shipping fixes for vulnerable code.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
Routine vapt scanning is essential to a good cyber security stance. The volume of vulnerabilities out there and the intricacy of the typical firm’s online infrastructure mean that an organization is practically bound to have at least one unpatched vulnerability that puts it in jeopardy. Discovering these vulnerabilities before the attacker does can be the difference between a failed attack and an expensive and humiliating data breach or ransomware infection.
One of the best things about vulnerability scans is that you can do it yourself and even automate it. With the proper tools and regular vulnerability scans, you can significantly lower your cyber security risk.
Qualysec’s Vulnerability Assessment Tool
Qualysec is a cybersecurity company that offers an automated vulnerability scanner tool that can scan your infrastructure for as many as known vulnerabilities. It’s meant to free up your time by automatically performing vulnerability assessment testing scans, tracking network changes, synchronizing cloud systems, and more. Qualysec creates a report detailing the vulnerabilities and providing actionable remediation guidance – so you can identify and remediate your vulnerabilities before the hackers do.



























































































































































































































































































































0 Comments