Introduction
The financial sector has witnessed an increasing reliance on digital infrastructure, not only as an opportunity but also as a big threat to cybersecurity. Cyberattacks, system failures, and third-party vulnerabilities can lead to severe disruptions, financial losses, and reputational damage. Over these issues, the European Union proposed the DORA Compliance, or Digital Operational Resilience Act, to boost the security and resilience of IT in financial institutions.
DORA installs an entire framework of digital risk management, making the EU financial sector cyber-resilient and disruption-resilient. Cybersecurity will be carried across the entire EU financial industry uniformly with the act, thus wiping out fragmenting regulations and strengthening the overall security standing.
This article walks readers through a comprehensive explication of DORA compliance, its goals, and needs, as well as its effect on financial firms.
What is the Digital Operational Resilience Act (DORA)?
The DORA rules and regulations, a new EU legislation that will enforce the standardization of financial institutions’ risk management standards to strengthen cyber resilience. It will involve banks, insurance companies, investment firms, and ICT service providers supporting the financial sector. According to this regulation, the standards of managing digital risks, responses of financial institutions to cyber incidents, and continuing their services have to be standardized.
The entire effect would be put on bodies by 17 January 2025, but it would come into force on 28 November 2022. In the event of non-compliance, this can also lead to severe regulatory penalties, financial sanctions, and reputational damage. DORA is also an integral part of a more holistic EU cybersecurity strategy as a Strengthening of the existing law relating to NIS2 Directive and GDPR.
Key DORA Goals
DORA’s main goal is to enhance the digital operational resilience of the EU financial sector through the following areas:
1. Harmonization of ICT Risk Management
DORA requires financial organizations to have an integrated risk management framework to anticipate, identify, and mitigate IT-related threats. The institutions need to develop a detailed policy, procedure, and control for cyber risks.
2. Incident Reporting Strengthening
To enhance industry-level awareness and response capabilities, DORA requires financial institutions.
- Implement real-time monitoring systems that can detect and report cyber incidents.
- Classify incidents based on their severity and potential impact.
- Submit reports to the regulatory body within stipulated timelines.
- Corrective measures must be taken to prevent future recurrences.
3. Third-Party Risk Management
The financial sector now depends much on third-party service providers for ICTs, which cover cloud computing and software. DORA imposes severe controls over third-party service providers through:
- Due diligence before partnering with service providers
- Regular security evaluations
- Contractual obligations, which essentially enforce compliance
- Exit strategies in the event of noncompliance or service failure
4. Strengthened Resilience Testing
DORA expects financial institutions to test their systems at regular intervals for security testing. This encompasses
- Penetration testing to identify vulnerabilities
- Scenario-based stress testing for testing cyberattacks
- Disaster recovery drills to assess the effectiveness of response
- Independent audits to check compliance with the cybersecurity standards
5. Harmonization of Compliance Requirements
One of the greatest impacts of DORA is its attempt to harmonize cybersecurity rules among all the member states in the EU. The financial sector was previously bound by a mishmash of national regulations, creating inconsistencies. DORA puts a single framework in place and ensures uniform requirements for compliance for all financial entities operating within the EU.
Latest Penetration Testing Report

Who Has to Obey DORA?
The category to which DORA will be applied includes;
Banks: Traditional banks, digital banks, and other financial institutions that handle customer transactions.
Investment firms: This entails organizations whose role in the marketplace lies in asset management, investment, and trading in assets.
Insurance and Reinsurance companies: Entities providing financial protection and risk management services.
Credit Institutions: An institution, firm, or corporation that primarily gives credits or provides loans, among others.
Payment Service Providers: Companies facilitating financial transactions and also including fintech and online payment services.
Crypto-Asset Service Providers: These are companies that deal with cryptocurrency exchange, wallet, and blockchain-based financial services.
ICT Service Providers Supporting Financial Institutions: Cloud service providers, cybersecurity firms, and technology vendors that provide critical ICT services.
DORA sets minimum cybersecurity and risk management standards, which all organizations operating within the EU financial sector should follow. Non-EU entities providing ICT services to EU financial firms could also be impacted since firms must operate only with vendors that satisfy the DORA standards.
By implementing tight cybersecurity measures, constant monitoring, and close supervision of third-party service providers, DORA is going to provide a more resilient financial ecosystem to keep both businesses and consumers safe against cyber threats.
Key Requirements for DORA Compliance
To comply with DORA, financial institutions must meet the five main pillars of DORA, which include:
1. ICT Risk Management
Financial institutions need to have a high-duty ICT risk management framework in place for recognizing, evaluating, and managing cybersecurity risks. This incorporates:
- Risk evaluation is to be done periodically.
- Protective mechanisms to avoid disruption.
- Clear definition of incident response and recovery plans.
- Business continuity planning during IT failures
2. Incident Reporting and Management
Firms should have an effective process for detecting and responding to incidents. Main requirements:
- Incidents can be categorized based on severity levels.
- Major ICT-related incidents are to be reported timely to the concerned regulatory authorities.
- Post-incident reviews to enhance future resilience.
- Sharing threat intelligence to prevent industry-wide disruptions.
3. Resilience Testing
Operational resilience is ensured by regular stress testing of ICT systems. This includes:
- Penetration testing to find vulnerabilities.
- Conducting crisis simulation exercises to test response capabilities.
- Ensuring effective disaster recovery strategies are in place.
4. Third-Party Risk Management
DORA mandates third-party ICT providers to be put through strict examination. The banks need to:
- Check and monitor the third party’s cybersecurity policies.
- Contractually agree with service providers regarding their responsibility for risk management.
- Have an exit plan if a service provider does not meet security requirements.
- The risk associated with suppliers has to be assessed constantly.
5. Information Sharing and Collaboration
The organizations are encouraged to collaborate and information sharing with their peers, the regulators, and the cybersecurity agencies to enhance joint resilience.
Process to Achieve DORA
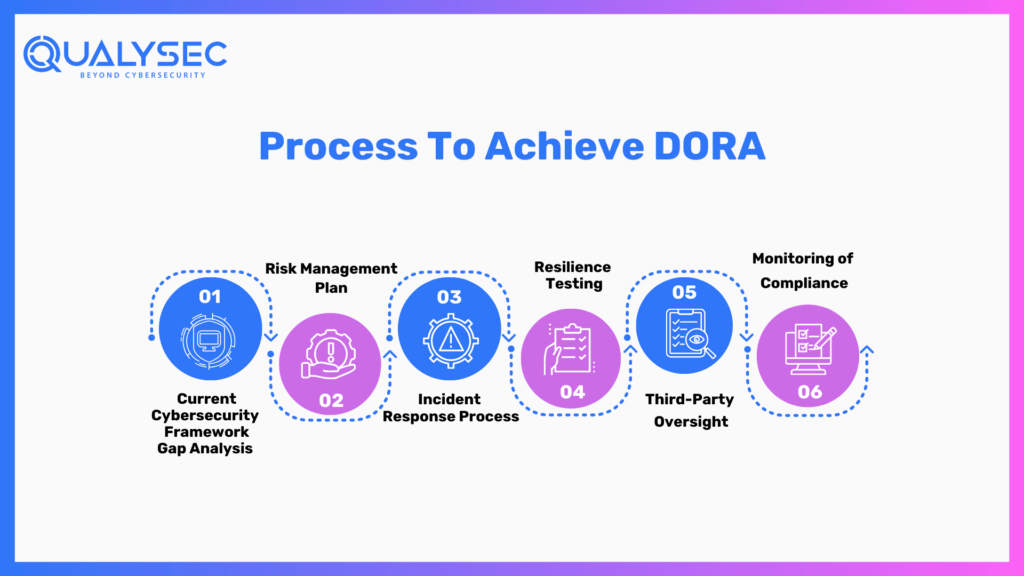
1. Current Cybersecurity Framework Gap Analysis
An organization shall conduct its gap analysis against the current cybersecurity with DORA expectations to know which area needs improvement.
2. Risk Management Plan
A comprehensive risk management framework that incorporates preventive, detective, and corrective controls needs to be designed.
3. Incident Response Process
Incident detection, reporting, and mitigation processes need to be designed, and financial institutions are required to report incidents to the regulators in due time.
4. Resilience Testing
IT infrastructure has to be periodically tested, including penetration testing and scenario-based assessments, so that vulnerabilities can be identified before exploitation.
5. Third-Party Oversight
Improve robust monitoring and contractual agreements of third-party ICT providers in compliance with DORA’s guidelines on third-party risk management.
6. Monitoring of Compliance
Organizations should make appropriate mechanisms for continuous monitoring and reporting to keep track of whether the regulations set by DORA are still being followed.
Effects of DORA on the Financial World
Improved Cybersecurity Standards
Since DORA demands higher cybersecurity standards amongst financial institutions, the chances of cyber attacks and IT failures that might disrupt financial stability are reduced.
Regulatory Oversight of ICT Providers
By compelling the critical ICT providers into the regulatory supervision fold, DORA will ensure that the outsourced services are compliant with adequate security standards.
Business Continuity and Trust
Proactive security measures will ensure business continuity and trust by customers and other stakeholders increases.
Financial/Legal Consequences of Non-Compliance
If an operator fails to comply with DORA, then severe financial penalties, reputational loss, and legal actions by the EU regulators may face them.
Challenges in implementing DORA Compliance
1. Complexity of Compliance Requirements
DORA requires such complex security controls, including risk management, testing, and third-party assurance. Financial institutions will have to implement a set of cybersecurity practices within their already existing frameworks, which can be rather resource-intensive, requiring huge investments in technology and human resources.
2. Legacy System Adaptation
Old-fashioned IT infrastructure persists in most finance firms today that may not reach the DORA standard for security and resilience. Improving this legacy will present the hardest step since a high investment usually relates to the time needed before it can take place.
3. Cross Functional Cooperation
DORA compliance requirements coordination between all departments, from IT to the legal, risk management, and operations. Where there is poor coordination among such departments, then there is always a likelihood of inefficiencies or gaps in compliance and problems arising in implementing an organization-wide security measure.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
DORA is a transformational regulation that enhances digital operational resilience in the financial sector of the EU. It also standardizes risk management in information and communication technology, reporting, testing, and oversight of third parties to ensure a financial institution withstood cyber-attacks and operational outages.
Since compliance deadlines are set for January 2025, organizations have to keep pace in front of the given schedule to meet DORA’s requirements. Implementing an overall cybersecurity framework is a critical demand for building resilience testing and improving third-party risk management.
Successful implementation and consequential Dora compliance in the banks will lead to cyber-risk mitigation along with bringing about an increased amount of trust and confidence to guarantee accurate regulatory compliance alongside achieving sustainable, long-term as well and operationally sound operations in the digitized environment going forward.
































































































































































































































































































































0 Comments