Mobile applications and services are critical components of our daily life, both at home and at work. As a result, they are attractive targets for hostile actors looking for sensitive information. Mobile application penetration testing helps identify vulnerabilities and enhance security. Cyberattacks increased by 38% in 2022 compared to the previous year, while the number of new mobile malware types increased by 54% in 2019.
A test report indicates that 84% of applications could not determine if their source code had been tainted with malicious code, leaving them open to a wide range of assaults. Only 15.7% of programs had any type of repackaging detection in place, making them the exception rather than the rule. With these, we know how vulnerable a mobile can be to cyberattacks, and how it can impact the privacy of individuals.
In this blog, we will dive into the dept of mobile app pentesting as it secures the application with robust techniques. Keep reading and learning!
What is Mobile Application Penetration Testing?
Mobile application Penetration testing is used to identify security flaws in mobile applications to defend them from attack. The Apple App Store and Google Play both have approximately 6 million mobile apps. Organizations require tested mobile security across all app components.
Decades of experience, exceptional customer service, flexible scheduling, and lightning-fast return time are all prerequisites for successful mobile app pen testing. These important components enable a threat-based approach, extensive testing with numerous analysis kinds, and support in resolving and validating any issues uncovered.
What are the Perks of Performing Pen Testing for Mobile Applications?
Mobile app security testing is an ongoing activity that benefits both the app development company and the app user. We’ll look at the top benefits of mobile security testing here:
1. Avoid Future Assaults
Running your app through a simulated assault is the greatest approach to assess its security strength. With an expert-level pen test, you can foresee potential future scenarios and prevent risks, as well as discover and fix code problems before hackers exploit them. Conducting frequent mobile pen testing will aid in the long-term safety and longevity of your app.
2. Prevent Monetary Loss
A data breach may cause considerable financial harm to a company in a variety of ways. If hackers get your personal information, they may demand payment in the form of ransomware. This may be prevented if the mobile app is subject to vulnerability and penetration testing before release. As a result, investing in security is better than falling victim to hackers or attacks.
3. Increased ROI on IT investments
It is critical first to protect the asset to ensure data security. Mobile app pen testing searches and addresses underlying dangers in the asset. With timely vulnerability assessments, an organization may prioritize which vulnerabilities to target first depending on the damage they might do to a system. This may also assist a company in gaining new clients and consumers.
What Should You Test in a Mobile Application?
Below are the things a penetration testing company checks to secure a mobile application:
1. Authorization and Authentication
- Examine the techniques for authenticating users, such as password security, biometrics, and two-factor authentication (2FA).
- Verify that users can only access the areas of the app that they are permitted to by testing role-based access control.
- Investigate how sessions are maintained and secured, searching for flaws such as session fixation, hijacking, and timeout difficulties.
2. Data Protection:
- Examine how sensitive data is stored on the device and communicated to backend systems. Avoid, insecure data storage, such as plaintext storage or inadequate encryption.
- Look for input validation flaws that might lead to data injection attacks such as SQL injection or remote code execution.
- Examine the program to ensure that it does not mistakenly reveal sensitive information to unauthorized users via logs, error messages, or other unintended routes.
3. Communication and Networking:
- Use proper encryption methods (e.g., TLS/SSL) to ensure that data is delivered securely between the mobile app and the server.
- Examine APIs for common web vulnerabilities such as Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), and unsecured API endpoints.
- Examine your network for potential network-based attacks such as DNS spoofing, network spy, and unsecured Wi-Fi connections.
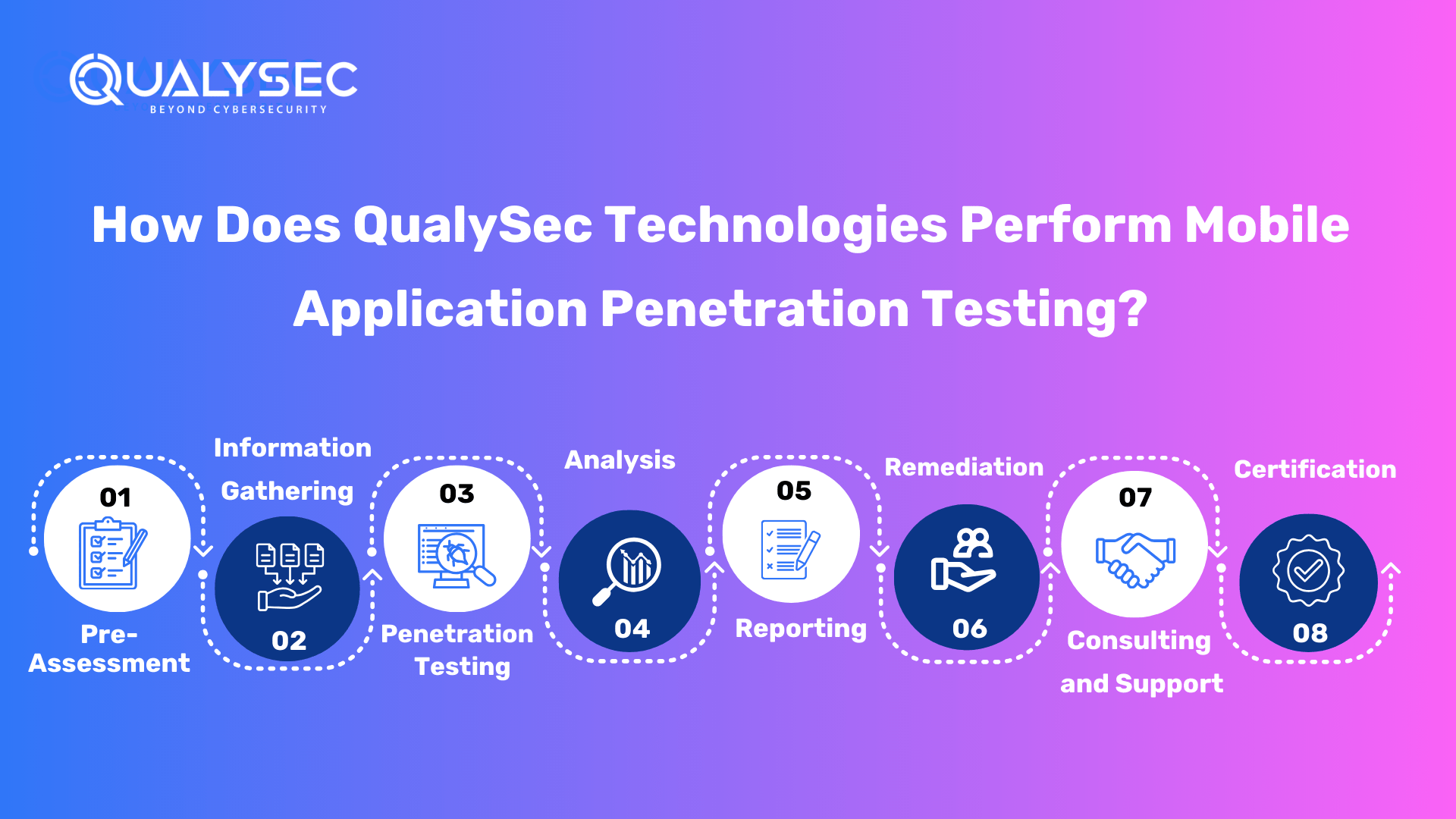
How to Perform Mobile Application Penetration Testing?
Pre-Assessment
The testing team specifies the scope and objectives of the penetration test during the pre-assessment phase. They collaborate with the app’s owner or developer to understand the app’s goals, functions, and possible dangers. This step involves preparation and logistics, such as defining the testing environment, establishing rules of engagement, and getting any necessary approvals and credentials to execute the test.
Information Gathering
The testing company advocates taking a simplified method to begin the mobile app penetration testing procedure. Begin by using the supplied link to submit an inquiry, which will put you in touch with knowledgeable cybersecurity specialists.
They will walk you through the process of completing a pre-assessment questionnaire, which covers both technical and non-technical elements of your desired mobile application. Testers arrange a virtual presentation meeting to explain the evaluation approach, tools, timing, and expected expenses.
Following that, they set up the signing of a nondisclosure agreement (NDA) and service agreement to ensure strict data protection. Once all necessary information has been gathered, the penetration testing will begin, ensuring the security of your mobile app.
Penetration Testing
The testing team actively seeks to attack vulnerabilities and security flaws in the mobile app during the penetration testing process. This phase consists of a series of simulated assaults and evaluations to detect flaws. Testers can rate the app’s authentication procedures, data storage, data transport, session management, and connection with external services. Source code analysis, dynamic analysis, reverse engineering, manual testing, and automation testing are all common penetration testing methodologies a tester uses.
Analysis
Each finding’s severity is assessed individually, and those with higher ratings have a greater technical and commercial effect with fewer dependencies.
1. Likelihood Determination:
The assessment team rates the likelihood of exploitation for each vulnerability based on the following factors:
- The prospective danger source’s motive and capabilities
- The vulnerability’s features
- Countermeasures’ existence and effectiveness
- If physical access to a device and/or a jailbreak are required.
2. Impact Analysis:
The assessment team studies and assesses the impact of the exploit on the company and its customers in terms of confidentiality, integrity, and availability for each vulnerability that may be effectively exploited.
3. Severity Determination:
The pen testing company gives severity ratings based on internal knowledge as well as widely used rating systems such as the Open Web Application Security Project (OWASP) and the Common Vulnerability Scoring System (CVSS). The severity of each discovery is determined independently of the severity of other findings. Vulnerabilities with a higher severity rating have a bigger technical and business effect and are less reliant on other flaws.
Reporting
Only if the security tester’s findings are properly recorded will they be useful to the customer. A good pentest report should include, but is not limited to, the following information:
- A concise description
- A scope and context description (e.g., targeted systems)
- Techniques employed information sources (either supplied by the customer or uncovered during the pentest)
- Prioritized results (for example, vulnerabilities organized using the DREAD categorization)
- Comprehensive results tips for repairing each flaw
There are several pentest report templates accessible on the Internet: Click below to find the best one!
Latest Penetration Testing Report

Remediation
The last stage is dealing with the identified vulnerabilities and shortcomings. The mobile app developer or owner implements the report’s recommendations and works on remediation measures to improve the app’s security. This step may also include retesting to ensure that the discovered vulnerabilities are resolved and the app is more secure. The objective is to make the app less vulnerable to security risks while still protecting user data.
Consulting & Support
The testing team frequently gives a consultation call to ensure that found vulnerabilities are successfully remedied. During this session, the security specialists review the results and offer advice on how to address and resolve the issues. This hands-on support is crucial for your development team to implement the necessary modifications as quickly as possible.
Certification
Penetration testing companies provide a letter of attestation as well as a security certificate to ensure the security measures used. These documents confirm that your application has been thoroughly tested and that all relevant security measures are in place.
What are the Security Threats in a Mobile Application?
Understand the below-given issues and their solutions to create a secure pathway for a mobile application:
Invalid Input Validations:
Without authenticating the data submitted by users, your application becomes an easy target for hackers. Hackers can submit malicious instructions or dangerous codes that might severely affect your app if sufficient validations are not performed.
Solution: Validate each input field as thoroughly as feasible. Here are some things to think about:
- Data Structure
- Permissible Characters for Data Length
- Values at the Lowest and Highest Levels
- As a result, the app will only take the data you desire, boosting security
Client-Side Injections:
SQL injection is just one type of client-side injection. Another kind is Local File Inclusion, in which the attacker uploads an executable file that your app reads and runs, potentially causing your app to crash or exposing sensitive data.
Solution: Proper input validations, i.e. validating all incoming data to ensure it’s within the parameters of what anticipates, are one of the most effective techniques to avoid client-side injections. Input validation can be defined as:
- Using a minimum and maximum value range check for data and string length.
- If the input data options are fixed, ask for an exact match.
- Only allows input data from an array of authorized values.
Unsafe Data Storage:
Insecure data storage can occur in a variety of locations inside your mobile app, including binary data stores, SQL databases, cookie stores, and others. If an attacker obtains access to a database or device, they can change the legitimate software to extract data for their systems.
Solution: For IPC files, avoid the mode “Readable” or “Writable” since they do not allow you to define data format or limit data access. Also, consider utilizing the security library to encrypt local files containing sensitive data. Reduce the amount of permissions your program requires as well.
Phishing Attacks:
Because mobile devices are always on, they are the first line of defense against most phishing attacks. Mobile users, according to CSO, are especially exposed since they frequently check their email in real-time, opening and reading emails as they arrive. Email apps on mobile devices are even more vulnerable since they offer less information to match the smaller screen sizes.
Solution: Even when opened, an email may only display the sender’s name until the header information bar expands. Never click on unknown email links. If the situation isn’t urgent, leave the response or action items until you get to your computer.
Inadequate Source Code Security:
If you don’t safeguard your source code, you’re effectively giving your competitive advantage—your intellectual protocol—away for free. Furthermore, source code frequently coexists with API or encryption keys, authentication tokens, user passwords, and other sensitive data that you do not want to be abused.
Solution: You may avoid risky source code by using mobile app security testing tools that examine your source code for vulnerabilities on a regular or even continuous basis. Although human code reviews should still be performed to check for vulnerabilities, this may handle the majority of the code review effort.
Who Needs Mobile Application Penetration Testing?
Any business or individual that develops, delivers, or utilizes mobile apps must do mobile application penetration testing. This includes businesses, government entities, mobile app developers, and even consumers.
Businesses must secure the security of their mobile applications since they frequently handle sensitive client data and transactions. Penetration testing helps mobile app developers detect and fix vulnerabilities before launching their products.
How Often Should You Conduct Mobile App Pen Testing?
The frequency with which mobile app penetration testing executes might vary based on factors such as the app’s sophistication, user base, and the developing threat landscape. Penetration testing for mobile applications is advised at least once in 6 months or if there are substantial upgrades or changes to the application.
High-risk applications or those dealing with sensitive data, on the other hand, may need more regular testing, such as quarterly or even monthly assessments, to address developing vulnerabilities and security risks. Regular testing aids in the maintenance of the app’s security and guards against any breaches and data leaks.
Mobile Penetration Testing: 4 Best Practices
- Prioritize vulnerabilities: Not all vulnerabilities are equally dangerous. Sort and prioritize them according to variables including ease of exploitation, potential effect, and chance of recurrence.
- Keep up with the newest tools and techniques: Mobile security is an ever-changing field. stay your knowledge and abilities up to date to stay up with new threats and developing technology.
- Recruit professionals: While internal penetration testing is useful, it is critical to employ external security professionals who can give an unbiased, third-party assessment.
- Reassess security regularly: Conduct frequent evaluations to discover new vulnerabilities and check the effectiveness of existing security measures.
What are the Common Tools for Mobile App Penetration Testing?
Burp Suite:
Burp Suite is a platform with integrated tools that assist the full testing process, from mapping to analysis. All features are available with the enterprise edition, including the following:
- Web vulnerability examination
- Scheduled Scanners
- Re-Scanning
- Tools for manual and sophisticated use
Nikto:
Nikto is a free and open-source vulnerability scanner that looks for things like insecure directories, out-of-date server software, and possibly harmful programs:
- Examines many ports or web servers
- Validates host authentication
- Guesses permission realm credentials
- Replays of Positive requests
MobSF
Mobile Security Framework, or MobSF, is a mobile application testing framework for Windows, iOS, and Android:
- Analysis, both static and dynamic
- Malware examination
- API testing on the web
- Zipper source code with APK, IPA, and APPX support
If you’d like to learn more about mobile security testing and the capabilities of these and other tools and services for mobile app penetration testing, please contact us.
Why Choose QualySec for Mobile Security Testing?
QualySec Technologies stands as a reliable partner for complete security solutions when it comes to mobile app penetration testing. We provide incomparable value to our clients with a dedication to quality and a unique method of testing that avoids false positives while finding true concerns. Our services include:
QualySec is the top choice for organizations of all sizes because of our reasonable pricing, commitment to on-time delivery, and long-term relationship philosophy. We recognize the significance of confidentiality and treat your information with the utmost care.
We protect your mobile app from possible attacks by utilizing a skilled team of certified cybersecurity specialists, powerful tools, and daily status updates. When you pick QualySec Technologies, you’re not just getting a security partner; you’re also getting a piece of mind, dependability, and a dedication to the safety of your mobile app. For more details, reach us today!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
QualySec’s mobile application penetration testing solution is a one-stop shop for all of your requirements. QualySec’s pen testing professionals assist enterprises in identifying vulnerabilities and securing their apps before they are vulnerable to harmful assaults.
FAQs
1. Is OWASP applicable to mobile apps?
The industry standard for mobile app security is the OWASP Mobile Application Security Verification Standard (MASVS). It is used by mobile software architects and developers to create safe mobile apps, as well as security testers to guarantee test findings are full and consistent.
2. Are mobile apps vulnerable to cross-site scripting (XSS)?
Programming languages and frameworks used by mobile app developers are numerous. As a result, typical vulnerabilities such as SQL injection, buffer overflows, and cross-site scripting (XSS) can appear in apps when safe programming techniques are not followed.
3. Why a mobile app rather than a web app?
Mobile applications tend to lead faster and provide consumers with a more complex browsing experience. They also consume less internet and work as follows: The software is downloaded via the app store for iPhones or the Google Play store for Android phones.
Watch our webinar now, to get advice and suggestions from our cybersecurity experts!








































































































































































































































































































































0 Comments