Wireless networks have become the backbone of our increasingly connected world. Yet, as our reliance on Wi-Fi grows, so too does the potential for cyberattacks to exploit these vulnerabilities. Research shows that wireless networks remain one of the most targeted entry points for hackers globally. This has made Wireless Penetration Testing essential for busiesses in 2025, especially with the rise of remote work, IoT devices, and emerging wireless standards.
This comprehensive guide will help you understand the importance of Wi-Fi pentesting, its methodologies, the tools you need, and best practices to ensure your networks are secure against emerging cyber threats. Whether you are a cybersecurity professional, IT enthusiast, or a business owner hoping to secure your network, this guide is just right for you to increase your knowledge and understanding about Wireless Penetration Testing. So, let’s get started!
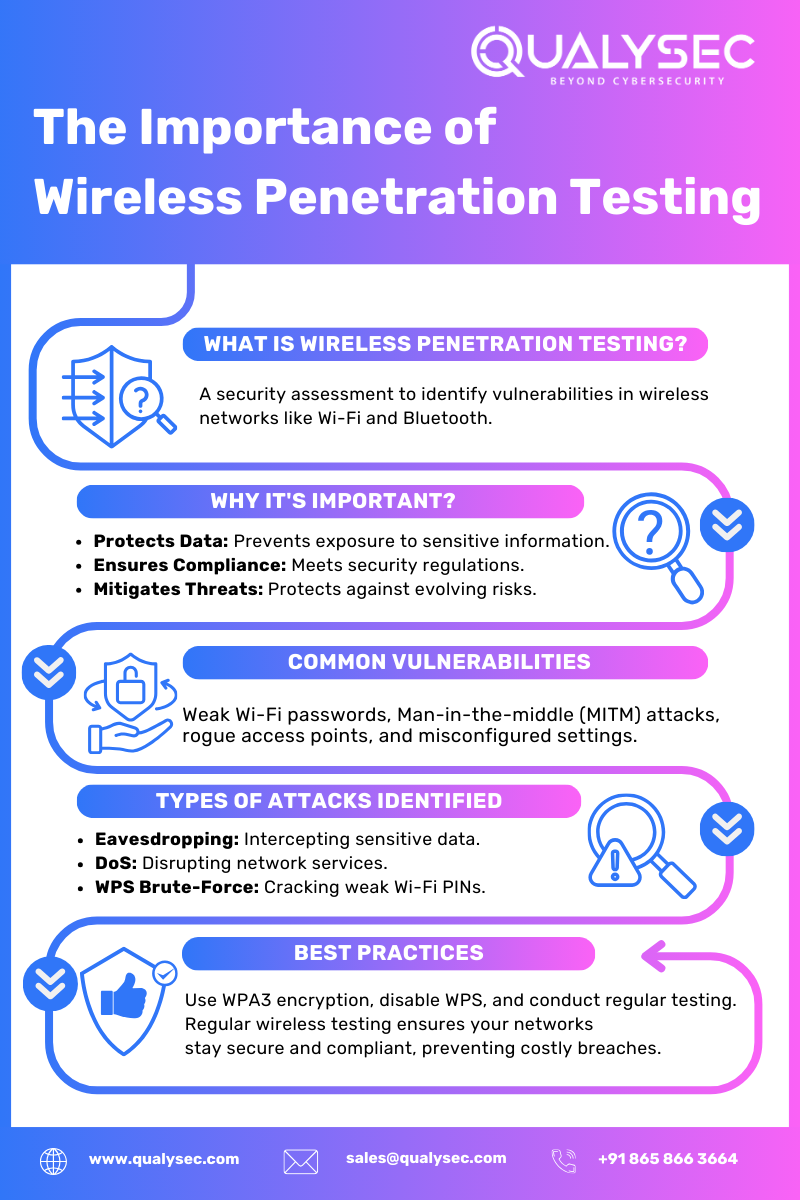
What Is Wireless Penetration Testing?
Wireless penetration testing, often referred to as Wi-Fi pentesting, is a cybersecurity practice that simulates attacks on an organization’s wireless network to uncover its vulnerabilities. The goal is to identify access flaws, unauthorized device connections, encryption weaknesses, and other security lapses that could leave the network exposed to attackers.
By analyzing these vulnerabilities, organizations can proactively address weaknesses before they are exploited by strengthening their network security strategy.
Some Examples of Wireless Vulnerabilities
- Weak Wi-Fi passwords can be cracked with brute-force tools, enabling unauthorized access.
- Man-in-the-middle (MITM) attacks on open or poorly encrypted networks allow hackers to intercept sensitive data.
- Rogue access points can pose as legitimate networks, tricking users into connecting and exposing their devices.
The threats of wireless insecurity are real, and the consequences of breaches can be devastating, from data theft to prolonged network downtime.
Why Wireless Penetration Testing Matters in 2025
With the continued evolution of Cybersecurity in 2025, Wi-Fi penetration testing has become more critical than ever. The growing reliance on wireless networks, powered by IoT devices, cloud services, and remote working environments, has created new attack surfaces for cybercriminals to exploit. Some of the key reasons why wireless penetration testing is essential are:
- Growing attack surface: IoT-connected environments increase the number of wireless endpoints vulnerable to attack.
- High-profile cyber incidents: Recent attacks on major corporations highlight the importance of proactive security measures.
- Regulatory compliance: Standards like GDPR, HIPAA, and PCI-DSS require organizations to secure their wireless infrastructure.
Weak wireless security can lead to breaches and cyberattacks, which could lead to significant data loss or reputational damage.
Some key benefits of wireless penetration testing are:
- Safeguards Sensitive Data: Identifying and fixing vulnerabilities early prevents hackers from intercepting confidential information.
- Ensures Compliance: Testing can help businesses adhere to global regulations like GDPR, PCI DSS, and HIPAA, which mandate strong cybersecurity measures.
- Reduces Breach Costs: The average data breach cost exceeded $4 million in 2023. Staying ahead of threats is the only way to save both resources and reputation.
Last year, a global retail chain was compromised via a poorly configured Wi-Fi network, which allowed hackers to access customer payment details. Incidents like these highlight the significance of Wi-Fi pentesting and role it plays in protecting important security systems.
Importance of Wireless Pen Testing
Key Methodologies in Wireless Penetration Testing
Penetration testing typically follows a structured methodology to imitate real-world cyberattacks effectively. Below is an overview of the key steps involved in wireless penetration testing:
1. Information Gathering
Understanding the network is the foundation of pentesting. This includes identifying wireless access points (APs), SSIDs, connected devices, and network architecture.
2. Scanning and Enumeration
Identify vulnerabilities like insecure protocols, outdated firmware, weak passwords, or DEFAULT settings through scanning and enumeration tools.
3. Exploitation
Simulate actual cyberattacks such as:
- Password cracking for weak Wi-Fi security keys.
- Deauthentication attacks to disrupt connected devices.
- Packet sniffing to intercept data transmitted over networks.
4. Reporting
Document findings with actionable recommendations, such as upgrading encryption protocols or disabling vulnerable access points. Testing makes sure reports comply with applicable cybersecurity regulations.
It can be better understood through an example – a penetration test on a corporate Wi-Fi network can reveal weak WPA2 encryption, which can be easily cracked and allow unauthorized access to sensitive business data.
Latest Penetration Testing Report

Must-Have Tools for Wireless Penetration Testing in 2025
To execute effective wireless penetration testing, professionals rely on a series of advanced tools. Here are the top tools every pentester should have in 2025:
- Kali Linux: A popular penetration testing operating system that includes pre-installed tools for Wi-Fi testing.
- Aircrack-ng Suite: Specialized for capturing and cracking Wi-Fi passwords in WEP, WPA, and WPA2 protocols.
- Wireshark: Used for packet analysis and identifying vulnerabilities in network traffic.
- Kismet: A wireless network monitoring tool that can detect rogue access points and unauthorized connections.
- Metasploit Wireless Exploitation Module: Allows deeper exploitation into wireless network vulnerabilities.
Using these tools for wireless penetration testing, cybersecurity teams can copy real-world attack scenarios with accuracy.
Best Practices in Wireless Penetration Testing
To maximize the effectiveness of your efforts, follow these best practices in wireless penetration testing:

- Test Regularly: Regular wireless penetration testing is necessary as new vulnerabilities emerge with advancements in technology. Cyber threats are constantly evolving, making it essential to conduct tests at least quarterly to avoid potential risks. Frequent assessments help identify weaknesses early and ensure that security measures are up-to-date with the latest threats and compliance requirements.
- Secure Your Test Environment: Before conducting penetration tests, it is vital to obtain proper authorization and isolate testing activities from the production environment. Unauthorized or poorly managed testing can cause disruptions, which leads to service outages or data leaks. By securing the test environment, businesses can minimize the impact on daily operations.
- Prioritize Encryption: Encryption is a critical component of wireless security, and penetration testers must focus on identifying weak encryption protocols that could expose sensitive data. Evaluating outdated WEP or vulnerable WPA2 configurations can help businesses strengthen their defenses.
- Partner with IT Teams: Effective collaboration with IT teams is key to addressing vulnerabilities identified during wireless penetration testing. This partnership builds a proactive security culture and allows quick remediation of weaknesses.
- Document Every Step: Thorough documentation is essential in wireless penetration testing to provide clear insights into identified vulnerabilities, attack vectors, and recommended fixes. Detailed reports help stakeholders understand security risks and also serves as a valuable reference for future security planning and compliance audits.
Thus, it is recommeneded to enhance your expertise with certifications like Offensive Security Wireless Professional (OSWP) or Certified Ethical Hacker (CEH). Both provide invaluable skills for effective Wi-Fi security assessments. OR the best is to choose a cybersecurity company offering Wi-Fi Penetration Testing and have the certified team members working for them.
Challenges for Wireless Penetration Testers in 2025
The evolving wireless background also brings unique challenges for penetration testers.
- IoT Complexity – IoT devices increase attack surface but are often less secure than traditional networks.
- Advanced Encryption – Technologies like WPA3 improve security but require sophisticated cracking methods.
- Legal & Ethical Concerns – Strict regulations around data privacy can complicate Wi-Fi pentesting activities.
To overcome these hurdles, make sure you and your team always staying updated with new tools, technologies, and regulations impacting the cybersecurity of your business.
Future Trends in Wireless Penetration Testing
Looking ahead, wireless network security is set to evolve significantly, with trends such as:
- 6G Networks – Raising both speed and security opportunities but also new vulnerabilities.
- AI-Enhanced Testing – Automating vulnerability detection and streamlining pentesting processes.
- Next-Gen Encryption – Lay the strong foundation for stronger, harder-to-crack security standards.
Staying ahead of these trends makes sure penetration testers keep providing value. On the other hand, businesses needs to stay ahead by adopting advanced tools and methodologies to secure their wireless networks – either by themselves or hiring a wireless penetration testing services company.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Stay Secure with Wireless Penetration Testing
Wireless penetration testing is essential for protecting modern organizations in 2025. It is no longer a “nice-to-have”; it is a necessity to maintain data security, regulatory compliance, and organizational trust.
If you want to take your Wi-Fi security to the next level, start by scheduling a professional penetration test for your business to stay secure.
Need help? Feel free to contact Qualysec for wireless penetration testing.
































































































































































































































































































































0 Comments