Cyber security penetration testing is a security exercise where penetration testers find and exploit vulnerabilities in applications and networks with permission. Organizations appoint a cybersecurity penetration testing company to hack their systems to look for weaknesses that they could use to enhance their security posture.
| 75% of companies perform penetration tests for security and compliance needs. |
In this blog, we are going to learn more about cyber security penetration testing, its different types, and how it helps with compliance requirements. Note that, penetration testing is an essential step in cybersecurity and businesses should conduct it regularly if they don’t want their applications to get hacked.
What is Cyber Security Penetration Testing?
The main goal of cyber security penetration testing is to find weak spots in a system’s defense systems before an attacker finds them and takes advantage of them. It is like hiring a thief to steal from your company’s vault. If the thief succeeds, you will know which areas are the weakest and how to tighten your security.
Cybersecurity pen testing is usually done on a company’s digital assets such as web apps, mobile apps, networks, cloud, APIs, etc. The end goal of doing penetration testing is to secure the business from unauthorized access, data breaches, financial loss, and overall cyberattacks.
Penetration testers (a.k.a ethical hackers) are skilled and certified professionals who try to break into your system and check whether they can break in. If they succeed, then there is a vulnerability. If not, then the defense is strong. Through this process, the organization gains valuable information on its security defenses.
Who Performs Penetration Tests?
Usually, penetration tests are conducted by cybersecurity professionals, also called “ethical hackers, ” since they are hired to hack into a system with the organization’s permission.
Typically, the task of a penetration test is given to a third-party security company, as it is best to have the test performed by someone who has little to no prior information about the target system. This is because, the testers will behave like actual attackers, following the same steps they would take. Additionally, they may expose weak spots missed by the developers who built the system.
Many penetration testers or pen testers are experienced developers with advanced degrees and certifications for ethical hacking. Additionally, some testers are reformed criminal hackers who now use their skills to help fix security issues rather than exploit them. The best team to carry out a pen test is to hire a specialized penetration testing company.
How Does Cyber Penetration Testing Work?
In cyber security penetration testing, ethical hackers use their skills to find and exploit vulnerabilities in the organization’s systems before real hackers do. They educate themselves on the latest technologies and their potential weaknesses. They mimic cybercriminals by copying their tactics, techniques, and procedures to penetrate systems, to root out IT vulnerabilities effectively.
The idea behind cybersecurity pen testing is to find and patch vulnerabilities before attackers find and use them for their gain.
Sometimes the pen testers use automated tools that expose the weaknesses in the operating systems, networks, applications, and clouds. But mostly, they use a more manual approach to conduct an in-depth analysis and find vulnerabilities missed by the tools.
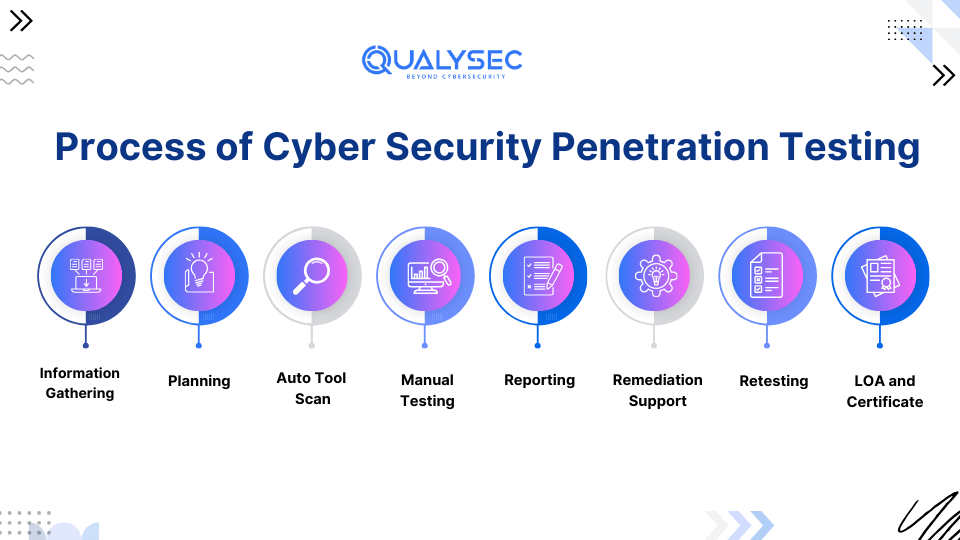
Penetration Testing Steps:
- Information Gathering: The testers gather as much information about the target application as possible, through the client or publicly available web pages.
- Planning: Then they plan the test, along with the scope, tools they would use, and vulnerabilities they would target.
- Automated Testing: 1st they use automated tools to find as many vulnerabilities as possible.
- Manual Penetration Testing: Then they use manual techniques to find all those vulnerabilities missed by the tools.
- Reporting: The report of the pen test will have vulnerabilities found, their impact level, and fixing methods.
- Remediation: The development team will use the report’s information to patch the found vulnerabilities.
- Retesting: The pen testers will retest the application to check whether all the patching is successfully done or not.
- LOA and Certification: Finally, the testing company will provide a letter of attestation (LOA) and a security certificate, proving that they have conducted cyber penetration testing.
Curious to see what a real cyber penetration test report looks like? Well, here’s your chance. Click the link below and download a sample report in seconds!
Latest Penetration Testing Report

How Often Should You Pen Test?
Penetration testing in cyber security should be conducted regularly – at least once a year – for better security and consistent IT operations. Conducting penetration testing once or even twice a year can help organizations keep their applications and networks safe from changing cyber threats. In addition, penetration testing is also done when the business needs to comply with industry regulations like GDPR, ISO 27001, SOC 2, HIPAA, etc.
Additionally, businesses should conduct penetration testing when:
- Adding new network infrastructure or applications
- Applying significant upgrades or modifications to infrastructure or applications
- Establishing new office locations
- Implementing security patches
- Modifying end-user policies
What Should You Do After a Pen Test?
Simply conducting a pen test to check it off the list is not enough for the betterment of your security. You also need to spend appropriate time and effort to use the results of the cyber security Penetration Testing. Here are 3 essential things you need to do after a pen test:
1. Review the Details of the Pen Test Report
A pen test report generally consists of three things – vulnerabilities detected, the impact of those vulnerabilities, and remediation methods. Additionally, the report shows how the infrastructure was exploited, helping organizations understand and address the root causes of security issues.
2. Create a Remediation Plan and Confirm with Retest
The initial pen test report will highlight the security issues along with their remediation measures. Organizations should create a plan to follow those remediation orders based on the severity of the vulnerabilities. When the remediation is over, organizations should validate it by asking the testing team to retest the application.
3. Use the Pen Test Findings in your Long-term Security Strategy
Pen tests often reveal the root causes of security issues that may require changes to your overall security strategy. Penetration testing is not a one-time thing, the true value of security pen testing is to perform it regularly to reduce the risk of changing cyber threats.
What Is the Difference Between Vulnerability Scans and Pen Tests?
A vulnerability scan uses automated tools to find weaknesses in a system, but a pen test uses manual techniques to find weaknesses and attempts to exploit them.
Here’s a comparison of vulnerability scans and penetration testing.
| Aspect | Vulnerability Scans | Pen Tests |
| Purpose | Identify and report known vulnerabilities | Simulate real-world attacks to find and exploit security weaknesses |
| Analysis Depth | Surface-level identification of vulnerabilities | In-depth analysis and exploitation of vulnerabilities |
| Tools Used | Mostly uses automated tools | Uses both automated tools and manual techniques |
| Frequency | Can be done regularly – once or twice a month | Usually done once or twice a year |
| Skill Required | Requires high-level development and testing skills | Requires high level development and testing skills |
| Result | Generates a list of potential vulnerabilities | Provides a detailed report of vulnerabilities identified, their impact, and remediation recommendations |
| Cost | Generally lower cost due to automation | Higher cost due to manual testing and expertise |
What Are the Different Types of Cyber Penetration Testing?
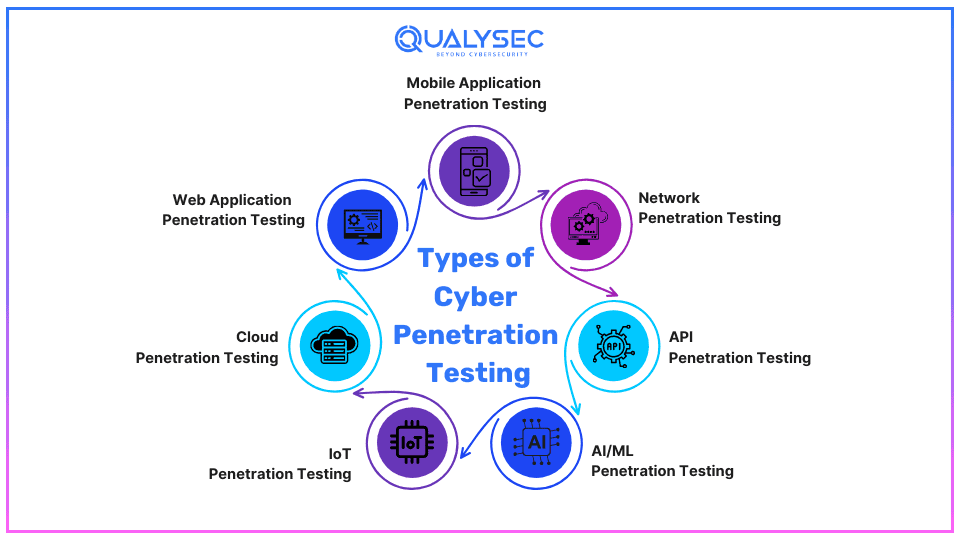
While pen tests can be classified into a wide variety, the common types of cyber security penetration testing services include:
- Web Application Penetration Testing: This involves assessing the security of web-based applications to identify and address vulnerabilities that attackers could exploit.
- Mobile Application Penetration Testing: It evaluates the security of mobile apps (both Android and iOS) to uncover potential weaknesses and ensure protection against unauthorized access and data breaches.
- Network Penetration Testing: Cybersecurity testing companies assess the security of computer networks to detect vulnerabilities and potential entry points that hackers could exploit to gain unauthorized access.
- Cloud Penetration Testing: This examines the security of cloud-based systems and services to identify vulnerabilities and assess the effectiveness of security measures in protecting sensitive data and resources.
- API Penetration Testing: This evaluates the security of application programming interfaces (APIs) to identify vulnerabilities and weaknesses that could be exploited to steal sensitive data.
- IoT Penetration Testing: The latest addition to pentesting, it assesses the security of Internet of Things (IoT) devices and networks to identify vulnerabilities and ensure the security of connected devices and systems.
- AI/ML Penetration Testing: This near future of pentesting service evaluates the security of artificial intelligence (AI) and machine learning (ML) systems/applications to identify potential vulnerabilities and ensure the reliability of AI-based applications and algorithms.
Want to conduct any of these penetration testing services for your company? Qualysec Technologies offers process-based pen testing services for all the above-mentioned categories. Tap on the link below and discuss your security needs with our expert!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
How Does Cyber Security Penetration Testing Help with Compliance?
Each region (USA, Europe, etc.) and industry (e-commerce, healthcare, etc.) has a different set of data privacy and security regulations that should be met. These rules are in place to protect sensitive user data. Not complying with these regulations will result in legal problems and fines.
These industry regulations often require organizations to conduct security testing for their applications and systems. This is where cyber Security penetration testing helps businesses with compliance. Security testing like pen testing helps organizations discover vulnerabilities that could be exploited by hackers for data theft.
As a result, by conducting regular penetration testing, organizations can prove their application and networks are safe for customers and their confidential information.
Compliance needs met by cyber security penetration testing include:
- International Organization for Standardization/ International Electrotechnical Commission (ISO/IEC 27001)
- Service Organization Control Type 2 (SOC 2)
- Health Insurance Portability and Accountability Act (HIPAA)
- Payment Card Industry Data Security Standard (PCI DSS)
- General Data Protection Regulation (GDPR)
How to Choose a Penetration Testing Provider?
Now we all know what penetration testing is and why it is important. But how do you choose a top penetration testing company that is right for your business? What should you consider before hiring a third-party provider and how to trust this provider to meet your expectations?
Here are 10 best practices that will help you choose the right pen testing company:
- Define the type of penetration tests you need (application, network, cloud, etc.)
- Evaluate the skills and certifications of the pentesting team
- Ask for relevant references
- Find out how they will help secure your data
- Ask for liability insurance
- Verify project management capabilities and communication channels
- Get a sample report
- Evaluate their methodology and process
- Ask about retesting options
- Get to know more about them and their achievements
Conclusion
By simulating real-world attacks, penetration testers help organizations identify and remediate vulnerabilities before malicious actors can exploit them. Cyber security penetration Testing is crucial for protecting sensitive data, preventing financial losses, and maintaining the trust of customers and stakeholders.
Regular penetration testing not only strengthens an organization’s security posture but also helps in complying with regulatory requirements such as ISO/IEC 27001, SOC 2, HIPAA, PCI DSS, and GDPR. If you want to protect your business from cybercriminals, regular penetration testing is the best way to go.
FAQs
Q: What is cybersecurity testing?
A: Cybersecurity testing focuses on examining an organization’s applications, networks, and other systems for vulnerabilities.
Q: What is a penetration test example?
A: Penetration test is conducted on the digital assets of a company, such as:
- Web applications pen test
- Mobile applications pen test
- Cloud pen test
- Network pen test
- API pen test
Q: Who requires penetration testing?
A: Businesses or individuals that store sensitive user data or conduct financial transactions should conduct penetration testing for their systems.
Q: Is penetration testing a tool?
A: Some tools are used as a part of penetration tests to automate certain tasks. However, penetration testing is a combination of both automated tool scanning and manual security testing.





















































































































































































































































































































































0 Comments