Cyber threats are evolving at an alarming rate, with attacks increasing by 75% year over year. The cost of cybercrime is projected to reach $15.63 trillion by 2029. To stay ahead of these threats, organizations must proactively assess their network security posture. Hackers continuously develop new methods to exploit vulnerabilities and gain unauthorized access to networks, leading to data breaches, financial losses, and reputational damage. To combat these risks, organizations must conduct regular network security audits to identify weaknesses, ensure compliance, and strengthen their cybersecurity posture.
This comprehensive guide covers everything you need to know about network security audits in 2025, including their importance, benefits, key aspects, methodologies, and industry best practices.
What is Security Audit ?
A security audit is a systematic evaluation of an organization’s IT infrastructure, policies, and security measures to assess their effectiveness in protecting against cyber threats. It helps identify vulnerabilities, assess risks, and ensure compliance with industry regulations.
A security audit involves:
- Reviewing security policies and procedures
- Assessing access controls and authentication mechanisms
- Conducting vulnerability assessments and penetration testing
- Evaluating compliance with industry standards and regulatory frameworks
- Providing actionable recommendations to enhance security
What is Network Security Audit
A network security audit is a comprehensive assessment of an organization’s network infrastructure to identify security gaps, misconfigurations, and vulnerabilities. The audit ensures that the network is secure from unauthorized access, cyberattacks, and data breaches while complying with industry security standards.
Key Components of a Network Security Audit:
- Reviewing firewall configurations and access controls
- Analyzing network segmentation and architecture
- Conducting vulnerability scans and penetration testing
- Monitoring network traffic for anomalies
- Evaluating security policies and incident response plans
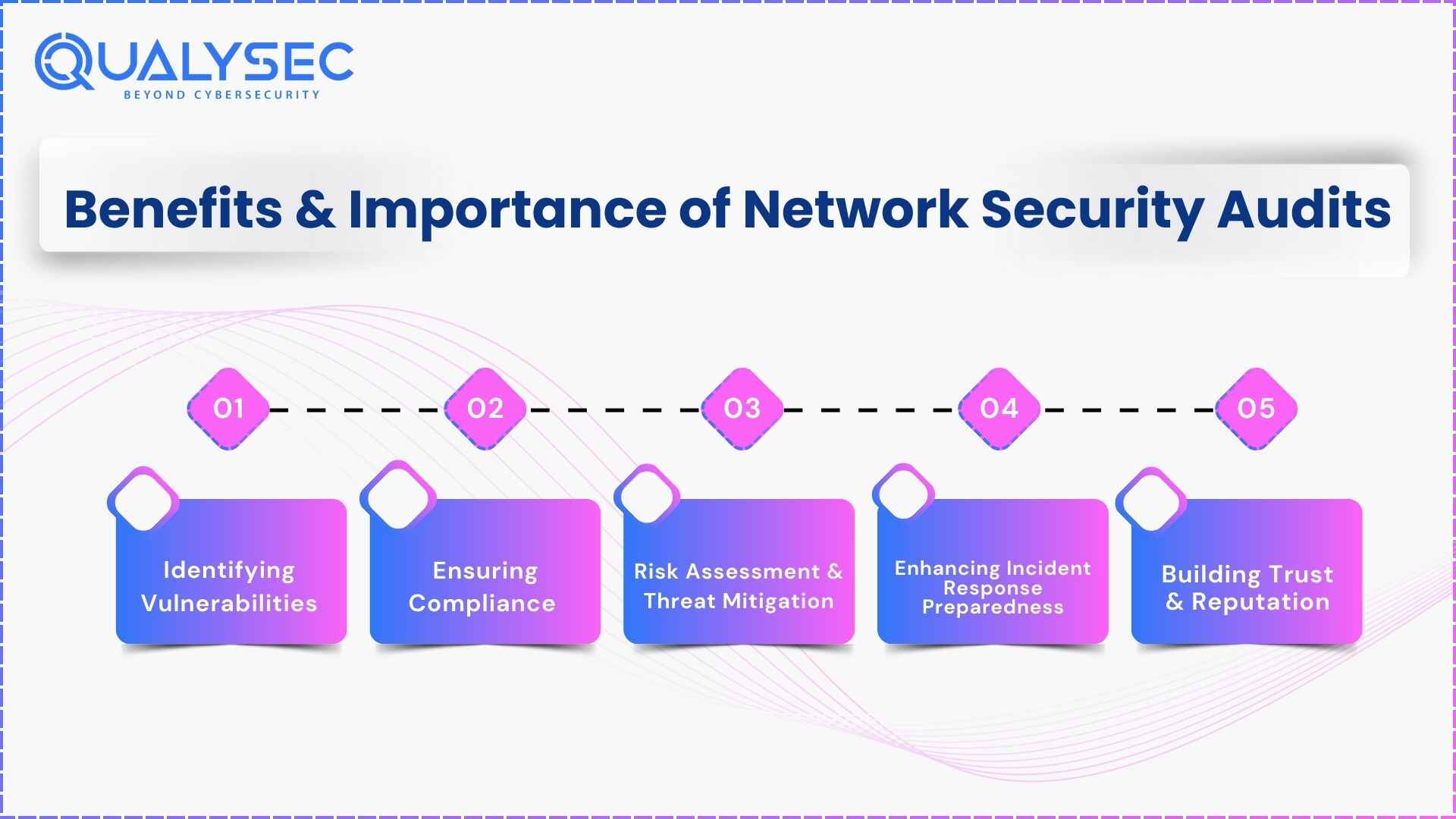
Benefits & Importance of Network Security Audits for for Businesses
The benefits and importance of network security audits are:
1. Identifying Vulnerabilities:
A network security audit helps detect potential security flaws such as outdated software, weak authentication protocols, and misconfigurations that could be exploited by cybercriminals. Addressing these vulnerabilities proactively strengthens the organization’s security posture.
2. Ensuring Compliance
Many industries must comply with regulatory frameworks such as GDPR, HIPAA, PCI-DSS, ISO 27001, and SOC 2. Regular security audits help organizations stay compliant, avoid hefty fines, and build trust with customers and stakeholders.
3. Risk Assessment & Threat Mitigation
By evaluating the security risks associated with network infrastructure, businesses can prioritize security efforts and allocate resources effectively to mitigate potential threats before they lead to cyber incidents.
4. Enhancing Incident Response Preparedness
A security audit helps organizations fine-tune their incident response and disaster recovery plans, ensuring they are well-prepared to detect, contain, and recover from cyber threats swiftly.
5. Building Trust & Reputation
Regular security audits demonstrate a commitment to cybersecurity, fostering trust among clients, partners, and regulatory bodies while protecting sensitive data from cybercriminals.
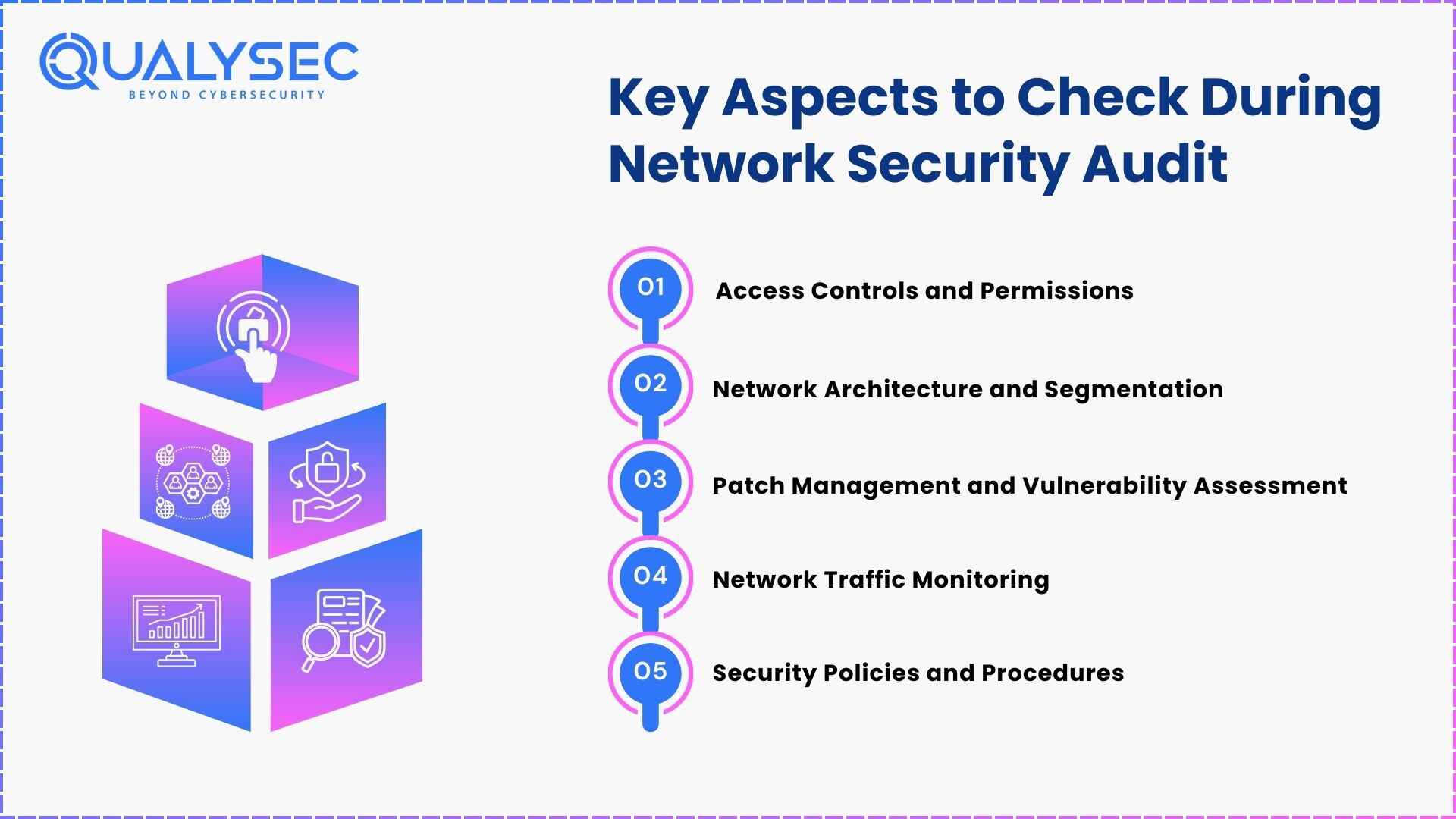
Key Aspects to Check During Network Security Audit
When you carry out a network security audit, you must explore various components to guarantee the security, confidentiality, and availability of the network. Here are key aspects to check:
1. Access Controls and Permissions:
Examine access controls and permissions configured on network devices, servers, and applications. Configure access privileges correctly by adhering to the principle of least privilege, ensuring that people or systems have only essential access permissions and avoiding overly permissive access.
2. Network Architecture and Segmentation:
Evaluate the network architecture that guarantees correct segmentation and isolation of valuable data and critical network resources. Ensure proper implementation of segmentation controls by using firewalls, VLANs, and ACLs correctly to prevent unauthorized communications and lateral movement within the network.
3. Patch Management and Vulnerability Assessment:
Measure the efficiency of the patching management structure and process for the network devices, servers, and applications endpoints. Hence, conduct vulnerability assessments to find and eliminate security vulnerabilities in network infrastructure components involving routers, switches, and firewalls.
4. Network Traffic Monitoring:
Review network traffic monitoring and intrusion detection systems to identify and respond to malicious activities and security incidents efficiently. Evaluate the network traffic logs, alerts, and anomalies for indicators of unauthorized access or uncommon activities on the network.
5. Security Policies and Procedures:
Evaluate the effectiveness of security procedures and policies covering network security practices, such as password management, encryption standards, and authorization. Make sure that security rules follow the industry standards and the rules of a regulatory body and that all employees know their roles and responsibilities concerning network security.
How to conduct a comprehensive network security audit?
A network security audit is an essential procedure that aims to improve an organization’s security posture. The following is a complete guide to an organization’s IT security audit process.
Steps involved in a network security audit process
|
Step |
Description |
|
1. Information Gathering |
Collect asset inventories, security policies, and network details. |
|
2. Planning & Scoping |
Define objectives, methodologies, and testing scope. |
|
3. Automated Vulnerability Scanning |
Use tools like Nessus, OpenVAS, and Qualys to detect weaknesses. |
|
4. Manual Penetration Testing |
Simulate real-world attacks to uncover hidden vulnerabilities. |
|
5. Security Audit Report |
Document findings, risks, and remediation strategies. |
|
6. Remediation & Patch Management |
Implement security patches and policy updates. |
|
7. Retesting & Compliance Validation |
Verify that remediated vulnerabilities are resolved. |
Want to see a real network security audit report ? Download by clicking the link below!
Latest Penetration Testing Report

Roles in Network Security Audits – Who Conducts Them?
Network security audits are performed by certified cybersecurity professionals and third-party security firms specializing in IT security. Key roles include:
- Certified Information Systems Auditors (CISA)
- Certified Information Security Managers (CISM)
- Certified Ethical Hackers (CEH)
- Network Security Engineers
These experts work closely with IT teams to perform audits, analyze results, and implement security enhancements based on industry standards.
Costs Associated with Network Security Audits
The cost of network security audit varies depending on factors such as:
- Scope and complexity of the audit
- Size of the organization’s network
- Compliance requirements
- Security tools and software licenses
Investing in a security audit can save businesses from the financial and reputational damage caused by cyberattacks.
Tools For Performing Effective Network Security Audits
Security testing, which includes tasks like vulnerability scanning, code analysis, penetration testing, and security audits, employs a variety of tools. Therefore, here’s a list of frequently used tools to help you better understand the technologies used in network security audits:
- Metasploit: This tool helps testers find and exploit vulnerabilities in a network. It has a large database of known exploits that can be used to see if a network can be hacked.
- Nessus: This tool scans networks and systems to find security weaknesses. It provides detailed reports on vulnerabilities that need to be fixed to improve network security.
- Nmap: Nmap is an open-source network administration program that primarily monitors network connections. It enables large-scale network scanning as well as host, service, and intrusion detection audits.
- Wireshark: Wireshark is a network traffic scanner and monitoring tool that displays the flow of network data within your system.
Qualysec’s Security Audit Solution
To provide accurate and trustworthy results, network security audits demand knowledge and experience. Being a pioneer in the penetration testing industry, Qualysec is unique. Further, to offer thorough security audit services, we use both automated tools and manual testing methods. With the help of Qualysec, you can be confident that you will receive high-quality security audit services that match your specific requirements.
As a leading penetration testing and security audit firm, Qualysec provides services such as:
- Comprehensive network security audits using automated and manual testing techniques
- Detailed audit reports with prioritized vulnerabilities and remediation steps
- Compliance support for GDPR, HIPAA, PCI-DSS, and more
- Continuous security monitoring and retesting services
By choosing Qualysec, businesses can ensure their networks remain secure, compliant, and resilient against cyber threats.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
With cyber threats evolving rapidly, network security audits are more critical than ever in 2025. They help organizations identify vulnerabilities, enhance security measures, ensure compliance, and build trust with stakeholders.
Partnering with a trusted cybersecurity firm like Qualysec ensures that your network remains secure, compliant, and resilient against cyber threats.
Ready to secure your network? Schedule a free consultation with Qualysec’s cybersecurity experts today!
FAQs
Q. What is a security audit?
Ans: A security audit is a thorough examination of a business infrastructure including its information systems, processes, and security policies. The main purpose is to identify the weak spots, assess the risks, and prepare measures to improve the whole level of security.
Q. Who does security audits?
Ans: Security audits are usually done by authorized cybersecurity professionals or firms specializing in the field. They check the efficiency of the safety measures, detecting weak spots and giving development proposals. Therefore, these audits are vital for the preservation of the integrity and security of digital systems and networks.
Q. What should a network security audit report include?
Ans: The network security audit report must cover the vulnerabilities, risks, compliance state, and remediation suggestions. Furthermore, it will highlight the network architecture, security policies, assessment methodologies, and a detailed action plan for enhanced security measures.















































































































































































































































































































0 Comments