The internet world is still growing. People are spending more time (and money) online than ever before, and this trend does not appear to be stopping anytime soon. Individuals have fully embraced life online, propelled by convenience and given some extra propulsion by a pandemic that reduced people’s capacity to make real-world connections.
Technology is evolving at a rapid rate, as are the dangers that attack it. Cybersecurity has never been more important, and one of the cornerstones of a solid security plan is penetration testing. In this post, we’ll look at penetration testing, its importance, and how it may help your IT infrastructure.
What is Penetration Testing?
Penetration testing is a technique for simulating a cyberattack in order to find flaws in your computer system, network, or online applications. It’s referred to as an ethical hack because it’s utilized to improve your cybersecurity.
A penetration test, or pen test as a service, should not be confused with a vulnerability assessment, which assesses possible vulnerabilities in a network and makes suggestions to mitigate these risks. Because penetration testing simulates a cyberattack, it is more intrusive.
Pen testing aims to assess the amount of risk associated with vulnerabilities in IT infrastructure. Companies invest extensively in their development and engineering teams to establish their digital infrastructure in today’s environment. However, they frequently fail to perform all of the essential measures to secure and safeguard their systems after deployment.
Then, when an attack happens on their networks, businesses react by forming an incident response team. This is to analyze their systems, rather than tackling it proactively with pen testing and security scanners. Companies may close the loop on this cycle by implementing a competent pen testing program.
Companies follow particular methodologies to perform penetration testing known as, black box, white box, and gray box testing:
- Black Box Testing: Here the tester is given only the bare minimum of information, such as the firm name. A tester will be able to imitate an attacker who is unfamiliar with the company. When this high-level knowledge is supplied upfront, time might be saved testing for possible vulnerabilities.
- Gray Box Testing: Here the tester is given more information, such as specific hosts or networks to target. This can give a solid picture of what a focused assault would look like without forcing the tester to spend a lot of time gathering data.
- White Box Testing: This form of testing entails giving the tester various internal documentation, configuration blueprints, and so on. The tester will be able to devote more time to exploiting vulnerabilities rather than host enumeration and vulnerability scanning.
Seeking more information about penetration testing? Talk to our Experts for Free!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
The Perks of Performing Penetration Testing: The Significance
Organizations press developers to create the product they commissioned as soon as possible so that it may be marketed and income generated. As a result, the hurriedly developed code is riddled with security flaws and defects that may be easily exploited for malicious purposes.
The same is true for infrastructure, which is frequently implemented in haste since businesses can’t wait and ROI is expected quickly. Penetration testing services help with these hassles with their numerous benefits such as:
It Exposes Vulnerabilities
A pen test allows businesses to identify where their vulnerabilities exist and how these vulnerabilities might be exploited. This test is performed in a secure environment where the pen tester is working with your organization rather than against it.
It’s similar to carrying out a test of your business continuity plan. You believe you’ve got everything covered, but even the best plan may be revealed to have a huge hole when a question or problem that no one has ever considered before is posed.
Gives Perspectives on Digital Infrastructure
Pen testing aids in the development of a deeper knowledge of your digital systems. This improves comprehension of how to prioritize risks and devise methods to mitigate the most harmful ones. As a result, alignment between repair and continuing corporate goals and objectives is possible.
Furthermore, firms might gain just by mapping out their digital infrastructure. Outlining your digital assets, a critical step in initiating a pen test, sheds information on how systems interact with sensitive data. This allows resources to be directed toward the most critical components and the development of appropriate security.
It Develops Customer Trust
With fresh hacks being disclosed nearly daily in the press, the importance of cybersecurity penetration testing should be obvious from a public relations aspect. When firms demonstrate that they have proactively checked their networks for vulnerabilities, it helps customer service.
Pentest might assist in convincing clients that they are in good hands with your organization. More importantly, avoiding the shame of a public hack improves consumer relations significantly. Investing in a strong penetration testing service provider can help prevent trust loss.
It Reduce the Number of Errors
Penetration testing reports can also help developers make fewer mistakes. When developers understand how a hostile entity launched an assault against an application, operating system, or other software they helped create, they will become more committed to learning more about security and will be less likely to make similar mistakes in the future.
It should also be highlighted that penetration testing is especially critical if your company:
- Has recently upgraded or changed its IT infrastructure or applications significantly,
- Has just moved to a new location,
- Have security patches, or
- Alterations in End-user policies.
It Assists with Regulatory Compliance
Many standards and laws are in place to secure data across many businesses. If you operate in business, you are probably bound by the PCI DSS standard. HIPAA standards must be followed if you operate in the healthcare industry.
Whatever standard your sector utilizes to safeguard consumers or clients, penetration testing providers may ensure that your company meets these standards. Industry compliance is critical because it helps you avoid regulatory penalties, potential litigation, and a variety of other difficulties that can affect your organization.
Also Read: A Comprehensive Overview of Penetration Testing
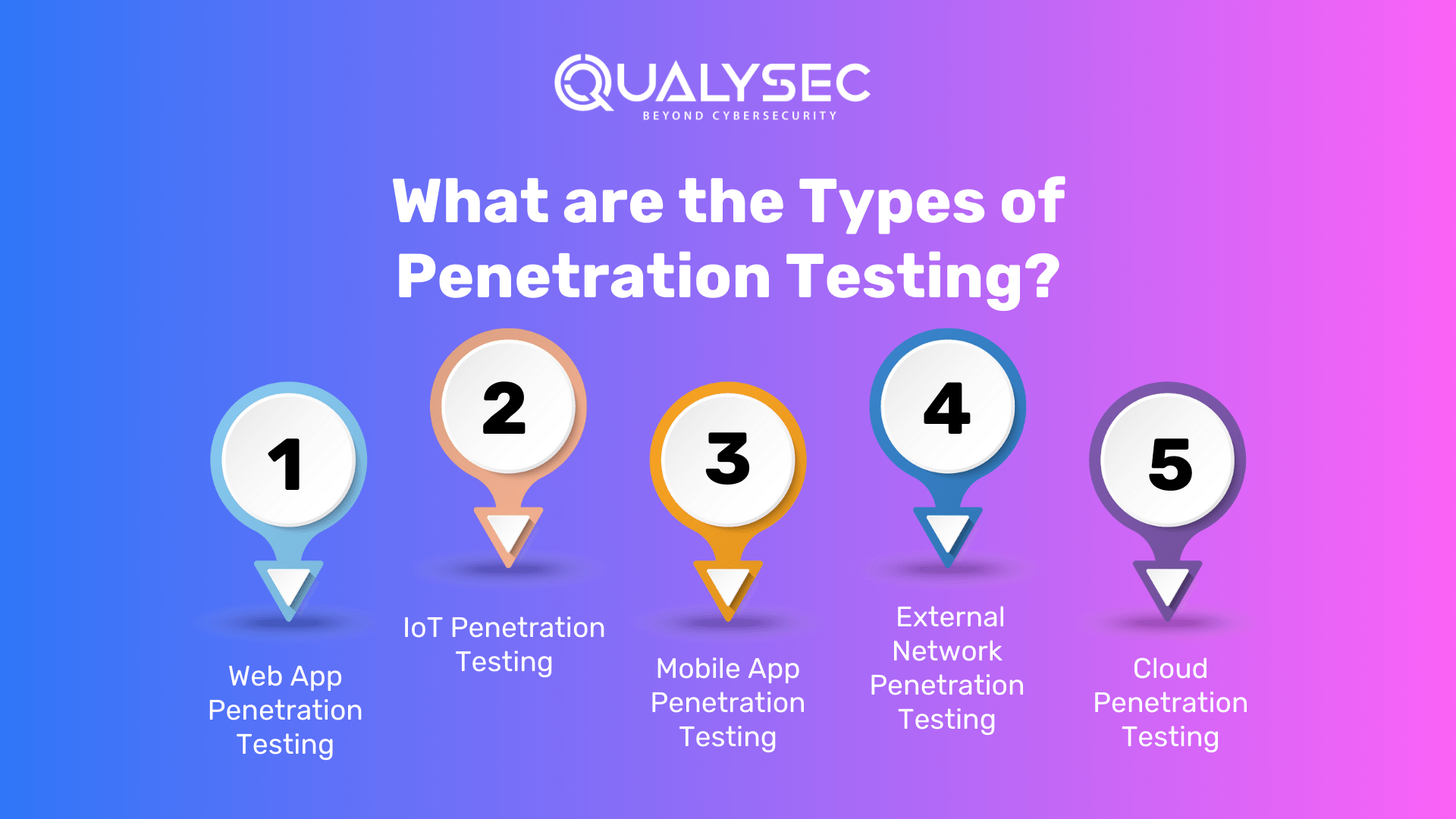
What are the Types of Penetration Testing?
A penetration test is most often done externally by companies to mimic various attack paths. A penetration tester may or may not have previous knowledge of the environment and systems they’re seeking to break, depending on the aims of each test. Here are some of the top types of penetration tests:
1. Web App Penetration Testing: This test is performed on web apps to identify security flaws or vulnerabilities in web-based applications. It employs several penetration techniques and assaults to access the web application. An online penetration test’s standard scope covers web-based applications, browsers, and associated components.
2. IoT Penetration Testing: Searches for security flaws in linked ecosystems, such as flaws in hardware, embedded software, communication protocols, servers, and IoT-related online and mobile apps. Some devices, for example, may necessitate data dumping via electronic components, firmware analysis, or signal collection and analysis.
3. Mobile App Penetration Testing: It is done on mobile applications (but not mobile APIs or servers), and it includes both static and dynamic analysis:
- Static analysis gathers source code and metadata and then reverse engineers it to find flaws in application code.
- While the program is operating on a device or server, dynamic analysis detects application vulnerabilities.
4. External Network Penetration Testing: Examines your present richness of publicly available information or assets. The assessment team seeks to acquire access to data via external-facing assets like as corporate emails, cloud-based apps, and websites by exploiting vulnerabilities discovered when screening your organization’s public information.
5. Cloud Penetration Testing: Intends to examine a cloud system’s strengths and vulnerabilities in order to enhance its overall security posture. Cloud penetration testing aids in the identification of risks, weaknesses, and gaps. The consequences of vulnerable vulnerabilities. Determine how to make use of any access gained through exploitation.
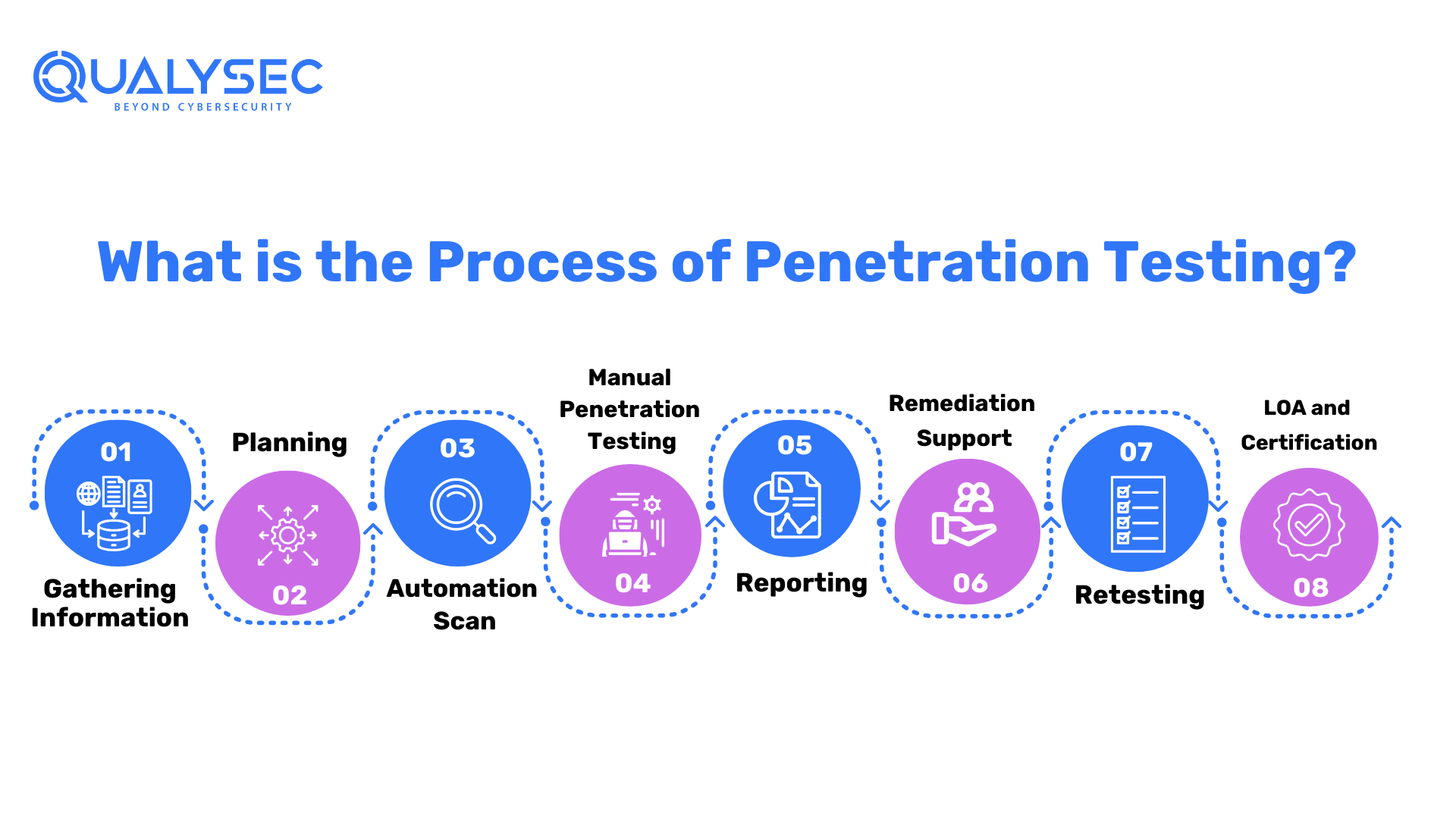
What is the Process of Penetration Testing?
Organizations often penetration testing companies to test their infrastructure to find vulnerabilities. These service providers have a specific process of conducting penetration tests for the application or network provided. Here’s a glance at the whole process:
Gathering Information:
The initial step in penetration testing is to gather as much information as possible. This includes a two-pronged approach: utilizing readily available information from your end, as well as utilizing numerous ways and tools to get technical and functional insights. Schematics for architecture, network topologies, and any existing security measures may be provided. Understanding user roles, permissions, and data flows is critical for building an effective testing strategy.
Planning
The penetration testing organization begins the process by carefully defining the objectives and goals. They delve extensively into the technical and functional complexity of the application. This extensive investigation allows testers to alter the testing strategy to target specific vulnerabilities and threats in the application.
A comprehensive penetration testing plan is create, outlining the scope, methodology, and testing criteria. To guide the testing process, the firm provides a high-level checklist. They acquire and prepare the essential files and testing instruments. This method includes configuring testing settings and checking script availability to ensure a smooth and successful assessment.
Manual Penetration Testing
The penetration testing company provides a full range of deep manual penetration testing services that precisely align with your individual needs and security standards. This one-of-a-kind technique enables a complete analysis of possible vulnerabilities across several domains, including:
- Network Penetrating Testing:
Extensive network infrastructure examination to discover and eliminate vulnerabilities, assuring the resilience of your entire network security. - API Penetration Testing:
In-depth examination of API functionality, with a focus on possible flaws and security breaches, to strengthen the robustness of your application interfaces. - Web Applications Penetration Testing:
In this online penetration testing, systematic evaluation of online applications, probing for weaknesses in authentication, data management, and other crucial areas to improve the security posture of the application. - Mobile Apps Penetration Testing:
A specialized assessment of mobile apps that identifies and addresses vulnerabilities specific to mobile settings, assuring the safe launch of your mobile applications.
Reporting
The testing team systematically identifies and categorizes vulnerabilities discover throughout the evaluation, ensuring that potential risks recognizes. A senior consultant does a high-level penetration test and reviews the entire report.
This ensures the highest level of quality in testing methods as well as the accuracy of reporting. This thorough documentation is a valuable resource for understanding the security state of the application.
Key Report Components:
- Vulnerability Name: Specifies each vulnerability, such as SQL Injection, providing a precise identification.
- Likelihood, Impact, Severity: Quantifies the potential risk by assessing the likelihood, impact, and severity of each vulnerability.
- Description: Offers an overview of the vulnerability, enhancing comprehension for stakeholders.
- Consequence: Describes how each vulnerability could impact the application, emphasizing the importance of mitigation.
- Instances (URL/Place): Pinpoints the location of vulnerabilities, facilitating targeted remediation efforts.
- Step to Reproduce and POC: Provides a step-by-step guide and a Proof of Concept (POC) to validate and reproduce each vulnerability.
- Remediation: Offers actionable recommendations to effectively eliminate detected breaches, promoting a secure environment.
- CWE No.: Assigns Common Weakness Enumeration identifiers for precise classification and reference.
- OWASP TOP 10 Rank: Indicates the vulnerability’s ranking in the OWASP TOP 10, highlighting its significance in the current threat landscape.
- SANS Top 25 Rank: Indicates the vulnerability’s ranking in the SANS Top 25, further contextualizing its importance.
- Reference: Provides additional resources and references for a deeper understanding of vulnerabilities and potential remediation processes.
This comprehensive reporting method ensures that stakeholders receive relevant insights into the application’s security condition as well as practical recommendations for a solid security posture.
Want to check how a comprehensive report can guarantee your application’s security? Download our sample report here!
Latest Penetration Testing Report

Remediation Support
If the development team requires support in reproducing or reducing reported vulnerabilities, the service provider delivers a critical service through consultation calls. Penetration testers with in-depth knowledge of the discovered issues promote direct engagement to aid the development team in effectively analyzing and addressing security threats. This collaborative approach ensures that the development team receives competent advice, allowing for the seamless and speedy resolution of vulnerabilities to enhance the overall security posture of the application.
Retesting
Following the completion of vulnerability mitigation by the development team, a vital stage of retesting happens. To check the efficacy of the treatments administered, our staff undertakes a detailed examination. The final report is lengthy and includes:
- History of Findings: This section provides a full record of vulnerabilities discovered in past assessments, providing a clear reference point for following the progress of security solutions.
- State Assessment: Clearly defines the state of each vulnerability, whether it is a fix, not an address, or ruled out of scope, providing a comprehensive summary of the remediation outcomes.
- Proof and Screenshots: Adds physical proof and screenshots to the retest report, providing visual validation of the corrected vulnerabilities. This validates the procedure and assures a thorough and accurate assessment of the application’s security state following repair.
- LOA and Certificate: The testing company goes above and above by providing a Letter of Attestation, which is an important document. Furthermore, this letter supports facts from penetration testing and security assessments, and serves multiple purposes:
- Level of Security Confirmation: Use the letter to obtain physical certification of your organization’s security level, ensuring stakeholders of your security measures’ strength.
- Showing Stakeholders Security: Show clients and partners your dedication to security by using the letter as a visible witness to the thoroughness of your security processes.
- Fulfillment of Compliance: Address compliance needs quickly, as the Letter of Attestation is a helpful resource for satisfying regulatory criteria and establishing compliance with industry-specific security practices.
Furthermore, the testing company will provide a Security Certificate, which will enhance your ability to represent a secure environment, reinforce confidence, and meet the expectations of various stakeholders in today’s dynamic cybersecurity landscape.
Did You Know?
You can also make QualySec’s Pentest Certificate publicly verifiable, allowing your clients and partners to validate it. It aids in the establishment of openness and trust for your company.
Want to learn more? Click here!
Want to hire a penetration testing company, but don’t know how to? Click here to learn about it.
What are the Challenges in Penetration Testing?
Because penetration testing is so “mainstream” these days, it’s easy to miss some of the important issues it poses. These difficulties, if not addressed properly, can leave your business exposed to attack, incur unnecessary costs, and reduce the value of your cybersecurity expenditures.
Restricted Scope
Everything from vehicles and pacemakers to cameras and printers is run by the Internet. These IoT devices frequently have inadequate cybersecurity protections, making them ideal access sites for hackers. Pen Testing companies always advocate including all devices and IP addresses that may connect to the Internet in penetration testing.
Encryption Flaws
Encryption is one of those areas where you will constantly find yourself playing catch up. In practically every penetration test, penetration testers and ethical hackers encounter poor encryption vulnerabilities. It is fairly usual to come across obsolete encryption protocols and poor encryption ciphers.
Legal and Ethical Restrictions
From getting illegal access to computer systems and data to privacy problems when gathering sensitive data, penetration testers face a complicated web of legal and ethical quandaries. Concerns have also been raised about acquiring consent for data and erasing data or systems. For penetration testers, compliance with cybercrime laws and regulations is critical.
Which Industries Need Penetration Testing the Most?
Penetration testing is critical for identifying and correcting security flaws before bad actors exploit them. Because of the sensitive nature of the data they manage, the information technology and financial industries rely heavily on penetration testing. Financial organizations must protect customer financial information, which necessitates penetration testing to guarantee the robustness of their security procedures.
Given the large volumes of client data maintained online, the e-commerce business is also very vulnerable to cyber-attacks. Penetration testing identifies flaws in online applications, payment gateways, and databases, resulting in secure transactions and the protection of consumer information.
Furthermore, vital infrastructure businesses such as electricity, transportation, and telecommunications rely on penetration testing to prevent any disruptions with far-reaching implications. These industries may decrease risks and improve overall resilience in the face of growing cyber threats by proactively analyzing and reinforcing their cybersecurity defenses.
Another field where penetration testing is essential is healthcare. Healthcare businesses are potential targets for cyber assaults due to the rising digitalization of patient information and the incorporation of medical devices into networks. Identifying and fixing vulnerabilities through penetration testing is critical for maintaining patient confidentiality and medical record integrity.
With the recent FDA guidelines to pen test medical devices before launching them, manufacturers need to focus on it more and more. Click here to read more about the FDA regulations.
Related Blog- Wondering what the FDA is and what the rules it realized? Click here to read more!
Why is QualySec the Best Penetration Testing Company?
When selecting a third-party pen testing strategy, you should first determine how frequently you will require testing. This can range from once a year for compliance purposes to more often if combined with an agile development strategy.
Automated pen testing provides a systematic technique for repeating this typically manual procedure for firms that require testing on a more regular basis. The breadth of these continuing testing procedures varies based on the specific changes or new assets released.
Finding a team, you can rely on in the ever-changing world of application development is critical for the safety and smooth functioning of your organization. Look no further—QualySec will go above and beyond to provide you with more than 100% of what you want for a stress-free experience.
Your application safety is not hypothetical. It should be a reality for all businesses. That is why we devote to assisting you in integrating security into the core of your firm. We can provide you with a full security assessment, and an evaluation to better understand your security.
Our Uniqueness:
QualySec distinguishes out as the only Indian business that offers process-based penetration testing. This one-of-a-kind method guarantees that your applications are not only safe but also adhere to industry best practices. Our pen test services provide a complete approach to process-based security testing, integrating both automatic vulnerability scanning and manual pen testing skills.
Our Team:
Our professional and experienced crew at QualySec is more than capable of executing the highest security requirements. We take pleasure in our comprehensive testing knowledge, which allows us to personalize security solutions to your application, preferences, and industry experience.
Pen testing Excellence:
To strengthen your apps, we employ a combination of in-house and commercial tools such as Burp Suite and Nets parker. What distinguishes us is the expertise of our pen testers, who offer a wealth of knowledge and manual testing abilities to ensure zero false findings. We provide a comprehensive and development-friendly report to our clients to understand the vulnerability in-depth and resolve the issues in a step-by-step format of the location of the vulnerability found and references about how to resolve the vulnerability.
Champions of Compliance:
It is not simple to navigate the complicated terrain of compliance. We’re here to help you navigate it, assisting organizations in meeting GDPR, SOC2, ISO 27001, HIPAA, and other regulations. Compliance is a smooth part of your company journey, we help you meet these with our comprehensive penetration testing methodologies and skilled after-support for remediation.
Global Achievements:
We have a proven track record of securing over 250+ applications in the previous three years. Our worldwide network includes 100+ partners and 20+ countries, and we take pride in saying that we have never had a data breach.
Are you ready to protect your application and your business? Contact us today and let QualySec be your digital shield! Your safety is our top priority.
Conclusion
We know the reality of this saying all too well in today’s data-driven culture, where cyber security is one of the top worries for individuals and enterprises with a digital footprint. Data compromise risks are considerable, and businesses are in constant target by cyber-attacks, resulting in financial losses and reputational harm.
Penetration testing tries to improve the security of professional hardware and software by emulating the techniques used by cyber thieves to break into the system. Ethical hackers employ a variety of techniques to counteract their destructive activities and examine digital assets and devices for flaws.
They measure staff security awareness and the effectiveness of an organization’s security policy. To do extensive penetration testing, you need to assemble a team of vetted experts in the field. QualySec offers pen testing and consulting services, as well as developing a comprehensive cyber security plan for enterprises of all sizes.
Reach out to us for professional help and a better understanding of how to perform penetration testing and why is it necessary. Secure your business infrastructure today! Click here to fill out the form!
FAQs
What is the primary purpose of penetration testing?
Pen testing (or penetration testing) is a security exercise in which a cyber-security specialist seeks to discover and exploit flaws in a computer system. The goal of this simulated attack is to find any weak points in a system’s security that attackers may exploit.
How does penetration testing contribute to overall cybersecurity efforts?
Pen testing assesses a company’s capacity to defend its networks, apps, endpoints, and users against external or internal efforts to overcome security rules and obtain unauthorized or privileged access to protected assets.
What types of vulnerabilities can penetration testing uncover?
Some of the most prevalent vulnerabilities discovered during external infrastructure penetration testing include Password attacks, cross-site scripting, application-level attacks, misconfigured security, and firewall devices.
How often should organizations conduct penetration testing?
Penetration testing should be conducted on a regular (at least once a year) basis to guarantee more consistent IT and network security management by disclosing how newly found threats (0-days, 1-days) or growing vulnerabilities might be exploited by malevolent hackers.
Can penetration testing be automated, or does it require manual intervention?
Manual and automated penetration testing are the two basic approaches used in the process. Each technique has different advantages and disadvantages; thus, security experts must establish a balance between the two in order to conduct full and successful security evaluations.















































































































































































































































































































0 Comments