An IT Security vulnerability assessment is an evaluation type through which an organization scans its system for possible security vulnerabilities. It carries out a process of vulnerability analysis to determine whether or not an organization is weak against known vulnerabilities, ranks the vulnerabilities according to their severity level, and makes recommendations for either remediation or, at the very least, mitigation of the threat involved. In other words, with vulnerability scanning, organizations would know if their software and systems are alive with default settings that can be exploited, such as easily guessable admin passwords.
IT Security Testing assesses for susceptibility to code injection attacks, such as SQL injection and XSS injections, and checks for user privileges or weak authentication mechanisms. In light of cyber threats, which are dynamic and ever-changing, organizations must take steps to ensure their networks, systems, and data are secured against various other threats.
What is an IT Security Vulnerability Assessment?
A process of evaluating, reviewing, and classifying the possible weaknesses present inside the organization or on its surrounding, hence, most likely usable by the attackers to harm. A weakness, by definition, is a flaw, mishap, or defect within the system that may potentially allow unauthorized access, data compromise, or even the crashing of the system. A risk assessment will attempt to find such weaknesses before they can be exploited by attackers, enabling companies to patch or mitigate such vulnerabilities. The review just shows in detail the possible weaknesses present in terms of hardware, software, network configuration, and humans. It is a preventive measure adopted in the area of IT security, which has specific regard for the identification of a given weakness and minimization of its possible effect, quite unlike the reaction to the threats that are posed.
Why is an IT Security Vulnerability Assessment Important?
Organizations can realize numerous benefits through periodic vulnerability scans: Identifying Critical Vulnerabilities: Periodic vulnerability scans promote the realization of security loopholes in systems that would be preferable targets by attackers. Anticipating the discovery of a vulnerability provides organizations a window of opportunity to remediate these openings before they blossom into a much larger issue. Decrease the Chance of Data Breaches: Cyber attackers are actively searching for means of executing their attacks against vulnerabilities and stealing confidential data. IT Security Vulnerability Assessment helps protect the proprietary information of an organization while maintaining compliance with data protection laws such as GDPR and HIPAA. Its Impact on System Stability and Performance: Vulnerabilities affect systems just as they do their security; so, a vulnerability test would help identify those vulnerabilities that cause a crash or make it slower, that in turn helps systems perform smoother. Maintain Compliance: Routine vulnerability assessment services are prescribed by major regulatory frameworks such as PCI-DSS, HIPAA, and ISO 27001 as part of compliance regimes applicable to organizations. Periodic vulnerability assessments aid in guiding firms into compliance with such standards while evading penalties. Cost-Effective: Prevention is surely better than cure, as a security breach is far costlier than the subsequent process involving fines, damage to reputation, legal costs, data recovery charges, and so on. So, frequent vulnerability scanning can save organizations from incurring huge costs arising from data breaches.
Latest Penetration Testing Report

Types Of Vulnerability Assessments
The most widely used types of vulnerability scanning by organizations include: Network-based scan? This scan type detects vulnerable systems connected to either wired or wireless networks within organizations that might be used for conducting security attacks on networks within organizations. Host-based scan? This type detects potential vulnerabilities within hosts connected to an organization’s network, such as critical servers and workstations. It also provides further insight into configuration settings and the patch history of the system. Wireless scan? It usually scans the Wi-Fi connections of organizations in search of possible rogue access points (APs) and to confirm whether or not the network is secure enough. Application scan? This scan targets the websites of an organization to check for known software vulnerabilities and insecure configurations of web applications or networks. Database scan?
How Does an IT Security Vulnerability Assessment Work?
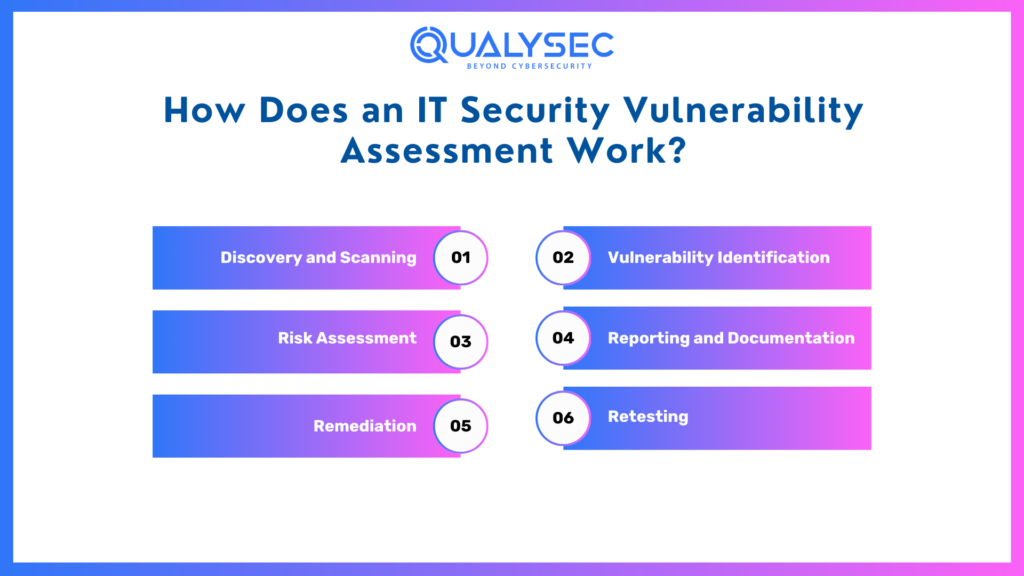
An IT Security Assessment usually encompasses several steps. Let us identify these steps to know how a vulnerability test is conducted in reality:
1. Discovery and Scanning
This is the first step taken in any vulnerability analysis: What needs analysis? It involves determining and unveiling all networks, systems, devices, applications, and databases within the organization. Thereafter, these processes would rely on some vulnerability scanning tools to check systems for known weaknesses. They cross-check the organization’s system settings and software versions against lists of known weaknesses, for instance, those provided by the National Vulnerability Database or vendor-supplied security bulletins.
2. Vulnerability Identification
The way of identifying specific vulnerabilities comes next after the scanning is done. While this part is in its right, scanning for vulnerabilities such as old software versions, misconfigured network devices, weak passwords, missing security patches, and open ports, inclusions could simply range from social engineering threats, e.g., phishing, to employee security awareness gaps.
3. Risk Assessment
Not all vulnerabilities are equal. Some are rather harmless, while others can be extremely dangerous and harmful at worst. Category and ranking of vulnerability risk evaluation would usually be based upon the severity, likelihood of impact, and exploitability; this is commonly done through the use of a risk scoring methodology such as the CVSS, whereby certain vulnerabilities are awarded a rating from 0 to 10 based on certain characteristics such as access complexity, impact on the system, and exploitability.
4. Reporting and Documentation
After the identification and assessment of vulnerabilities, the subsequent step in the process should be the documentation of the findings into a full report. This report should indicate the identified vulnerabilities, their degree of severity, and an elegant understanding of the impact they impose.
5. Remediation
This means that once enabled, work goes on for the correction or reduction of vulnerabilities discovered in the report. This can include various means, such as: Software Patching-the issue of software patches for vulnerabilities; Configuration Changes-modifying system configurations that are exploited by vulnerabilities; System Updates- installation of a more secure version of security updates; Access Control-the introduction of additional access control procedures; Training of Staff-the raising of operations to the house on security issues, like the identification of phishing attacks.
6. Retesting
After the remediation, the systems should be retested to ascertain that the vulnerabilities have been adequately fixed. This usually involves re-scanning the systems to check that the problems that were once there have been fixed. If new vulnerabilities are found, the process then continues to keep the systems safe.
Organizations that go through a vulnerability assessment will go through a four-step process.
But remember, a vulnerability assessment is not a one-time thing that organizations forget once it has been done. It should be done regularly and made operational by urging development, security, and operations teams to work together closely with one another—a process referred to as DevSecOps.
Vulnerability identification
The initial step is to develop a detailed list of vulnerabilities in an organization’s systems, servers, and applications. This is accomplished by either scanning them with specific internet vulnerability assessment tools or manually testing them. Vulnerability analysts may also employ vulnerability databases, vendor releases, threat intelligence feeds, and asset management systems to determine possible weaknesses.
This initial process step assists organizations in grasping the complete details. This entails aspects such as risk tolerance level and appetite, business impact analysis, mitigation practices and policies, countermeasures for devices and services, and treatment of residual risk.
Vulnerability analysis
The second step is to find out the origin and root cause of the vulnerabilities detected in the first step. The analysis phase determines the system components that are responsible for each vulnerability and its root cause.
Remediation
The last step in the vulnerability assessment testing process is closing any security loopholes. This typically involves a collaborative effort among the DevSecOps team, who outline the most efficient method of patching or remediating every vulnerability found.
Remediation may involve the implementation of new security measures, procedures, or tools; updating configurations and operations; and creating or implementing patches for found vulnerabilities. The completion of this process should allow organizations to develop a vulnerability assessment report.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
What Are The Different Types Of Vulnerability Assessment Tools?
Some of the most commonly used vulnerability assessment tools are:
Using specific vulnerability assessors, organizations have a means to discover their new or existing vulnerabilities. They must, therefore, plan to perform periodic and automated scanning of their critical IT systems and integrate the scan results with their continuous vulnerability assessment process.
Fortinet vulnerability scanner
Perhaps the most widely used tool for vulnerability scans is a web application scanner, like the Fortinet Web Vulnerability Scanner (FortiADC). Such tools scan, test, and mimic attack patterns of known vulnerabilities.
Protocol scanners and more
Protocol scanners can also be employed to evaluate vulnerabilities. These are designed specifically to look for vulnerable network services, ports, and cybersecurity protocols. Besides, the use of plugins in the vulnerability assessment platform can be considered, for example, scanning popular and common ports, firewalls, and content management systems (CMS) like Drupal, Joomla, and WordPress.
Conclusion
IT security vulnerability assessment is a critical component of an organization’s cyber security plan. It offers a systematic, comprehensive method of detecting, prioritizing, and remediating security vulnerabilities before they can be used by cybercriminals. Regularly scanning for vulnerabilities will decrease the likelihood of a cyberattack, ensure regulatory compliance, optimize system performance, and safeguard sensitive information.















































































































































































































































































































0 Comments