Vulnerability scanning looks for security weaknesses in IT systems like computers and software. As business technology gets more complex, new ways to scan for problems are needed to keep hackers at bay. During the first quarter of 2023, more than 6 million data records were exposed worldwide through data breaches. Cybersecurity companies have made vulnerability scanning tools that check for issues and put them into a full plan to manage security problems. These plans look at all the ways someone could break into a system. Regular checks and updates help keep systems safe from threats, making these tools essential for a secure IT setup.
What is Vulnerability Scanning?
It is the method through which vulnerabilities are identified and reported. Vulnerability reviews are conducted via scanning tools to identify security risks to the system and which could attack across an association’s networks and systems. Vulnerability scanning and assessment is an essential step in the vulnerability operation lifecycle.
Once vulnerabilities have been linked through scanning and assessed, an association can pursue a remediation path, similar as doctoring vulnerabilities, closing parlous anchorages, fixing misconfigurations, and indeed changing dereliction watchwords, similar as on internet of effects( IoT) and other bias.
Which tool is used for vulnerability scanning?
-
- Invicti
- Nmap
- OpenVAS
- RapidFire VulScan
- StackHawk
- Cobalt.IO
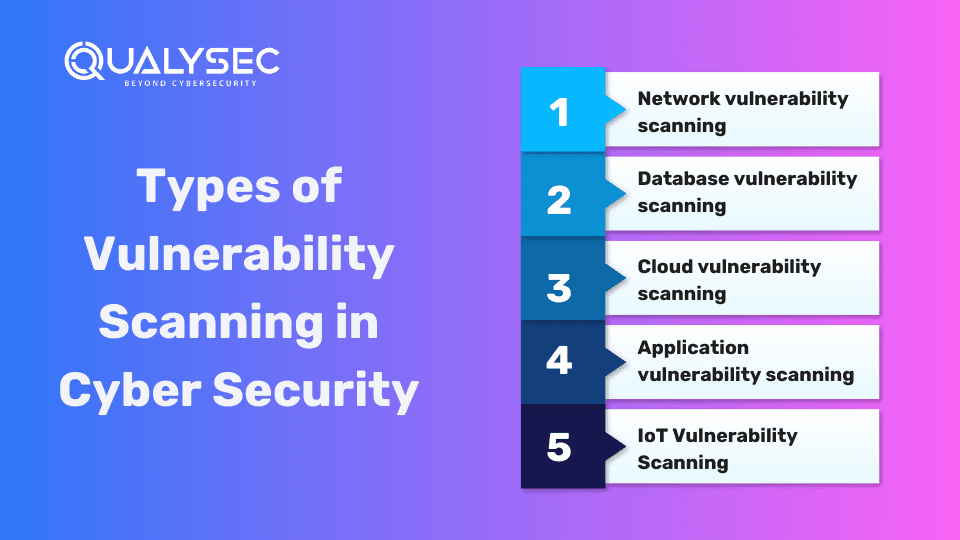
Types of Vulnerability Scanning in Cyber Security
Network vulnerability scanning: This means we do a full detailed study of the whole network of the organization, examining from A to Z. The search is with every alley or opening which enables our enemy to exploit our security weaknesses. Implementing cybersecurity is similar to an annual maintenance for the network of the organization. It simply ensures that the network is safe and secure.
Database vulnerability scanning: Looking through such databases for important or app-connected data information is part of this particular task. We have to find ways to secure all the data, while at the same time detecting any potential security threats that may compromise it. It is, basically, analogous to an immune system reaction in the organization’s data storage.
Cloud vulnerability scanning: The Compliance team will also be involved in the cloud service and configuration treatments. Our team undertakes the role of detecting any mistakes or other weaknesses that may be a hazard. It is analogous let’s say to a security assessment of the locally based cloud activities.
Application vulnerability scanning: The process involves testing web-based, mobile and any other type of applications for security bugs. We are looking for vulnerabilities that may be a target of the attack, and after figuring out the data we correct the issues. It mirrors a security check of digital applications of the organization, only it’s more accurate and accessible.
IoT Vulnerability Scanning: This is a part of the endeavor of examining the security of affordable internet of Things (IoT) devices. We are likely examining any places that might be used as starting points or discovered in the process.
Pros of Vulnerability Scanning
Security companies employ scanning tools in searching for vulnerabilities within the organization’s systems. These criminals also have used the same types of tools to find out these weaknesses and opportunities of being them through a system. By limited to providing a snapshot of your network and systems state security scans show only the existing state of an organization’s vulnerabilities.
Through vulnerability scans which happens proactively, enterprises are able to be ahead of the risks as they scan their infrastructure for weaknesses. The main focus of their efforts is immediately to be one step ahead of hackers and their systems up to date. Scans brings any issues to the attention for the purpose of resolution before the problems arises.
Cons of Vulnerability Scanning
Incomplete Detection: These tools have some limitations so the use of a single tool may not guarantee your systems are secure and free from all vulnerabilities. A host of new weaknesses is being found at an alarming rate, and some of these get beyond even the state-of-the-art detections tools.
Need for Regular Updates: Catching tools should be updated every time to find the newest security gaps. The weaknesses of such applications might increase if they are not adjusted to fix the new vulnerabilities that hackers may exploit.
False Positives: Above all, scanning tools often report such notable issues that are actual even for large IT infrastructure with multiple servers and services. Here, security specialists mistake them for a breach and go on to report the problem, even if it is actually something minor. If falses positives are supposed to be checked out on a regular base, then the tool will continue to give an inaccurate result.
Unclear Business Impact: The moment it is identified that an attack vector has been breached, the following procedure can be daunting as far as the impact on your business is concerned. An automatic tool will not bridge the gap of business analysis about the vulnerability, and the system administrator may largely focus on the technical characteristics rather than the criticality of the information lost.
Difference Between Vulnerability Scanning and Penetration Testing
Vulnerability scanning is automated, while penetration testing involves manual work by a tester who tries to exploit system weaknesses. Penetration testers act like hackers, using their methods to find weaknesses and report potential breaches.
Vulnerability scanning service automatically provides an overview of critical assets and system flaws, while penetration testing simulates real attacks. Both are important for keeping infrastructure safe and are part of a wider vulnerability management process. While intrusive vulnerability scanning can also exploit vulnerabilities, it does so automatically. The real purpose of a vulnerability scan is to give security teams a big-picture look at critical assets, system and network flaws, and security.
| Aspect | Vulnerability Scanning | Penetration Testing |
|---|---|---|
| Automation | Fully automated | Manual |
| Approach | Identifies vulnerabilities | Exploits vulnerabilities to simulate real attacks |
| Purpose | Provides a broad overview of critical assets and system flaws | Surface-level identifies vulnerabilities |
| Depth of Analysis | Simulates real attacks to assess the system’s resilience | In-depth, attempts to exploit vulnerabilities |
| Simulation | Does not simulate real attacks | Periodically used to assess the system’s security posture |
| User Involvement | Minimal user involvement required | Requires skilled testers to perform manual testing |
| Scope | Less comprehensive, focuses on scanning for vulnerabilities | More comprehensive, assesses security posture and potential impact |
| Reporting | Provides a list of vulnerabilities found | Reports on vulnerabilities exploited and potential impact |
| Frequency of Use | Regularly used for continuous monitoring of systems | Can be more expensive due to the manual effort and expertise required |
| Cost | Generally lower cost | Can be more expensive due to the manual effort and expertise required |
Why you should choose Penetration Testing over Vulnerability Scanning
Why should you choose penetration testing over vulnerability scanning, here is why, Penetration testing is not just a security measure; it’s a proactive approach to maintaining the integrity of your digital assets. Here are some attributes that make Penetration Testing relevant in today’s threat landscape compared to the best vulnerability scanner:
- Detection of In-Depth Flaws: Penetration testing excels at identifying vulnerabilities in your systems, applications, and networks. This early detection is crucial for mitigating potential threats and when compared to vulnerability scanning, penetration testing provides in-depth findings.
- Risk Identification: Penetration testing is carried out by experts and security professionals, this helps them find various risks that could be a major threat in the future. They help you see which problems are bigger risks to the system in real-time.
- Maintaining Compliance: Many industries have strict compliance requirements. Penetration testing helps organizations stay compliant by identifying and addressing security weaknesses.
- Enhanced Security: By identifying vulnerabilities and addressing them promptly, organizations significantly enhance their overall security posture. This reduces the risk of breaches and data leaks. Penetration testing shows you what real hackers could do to your system. This helps you understand and fix the most important problems first.
Why Choose Qualysec for VAPT Assessment
Qualysec is a cybersecurity company founded in 2020 that has quickly become one of the most trusted names in the industry. The company provides services such as VAPT Testing, security consulting, and incident response.
Although Qualysec’s Oppressional office is in India, Qualysec’s extensive knowledge and expertise in cybersecurity testing services have earned a reputation among the top VAPT service providers.
Technicians at Qualysec can detect flaws that fraudsters could abuse. After these flaws have been found, Qualysec collaborates with the organization to establish a plan to address them and boost the company’s overall security posture. Among the several services available are:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- Blockchain Pentesting
The Qualysec team, comprising offensive specialists and security researchers, collaborates to provide their clients with access to the latest security procedures and approaches. They provide VAPT services using both human and automated equipment.
In-house tools, adherence to industry standards, clear and simple findings with reproduction and mitigation procedures, and post-assessment consulting are all features of Qualysec’s offerings.
The solution offered by Qualysec is particularly beneficial for businesses that must adhere to industry rules or prove their dedication to security to clients and partners. So, by doing routine penetration testing, businesses may see weaknesses and fix them before hackers attack them.
Qualysec offers top-of-the-line penetration testing for web applications, mobile apps, cloud, IoT devices, etc. along with source code review and AI/ML penetration testing. Contact Us Now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Steps Involved in Vulnerability Scanning and Penetration Testing (VAPT)
Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive process that involves several steps. Understanding this process is essential for effectively utilizing vulnerability scanning tools:
-
- Scoping: Define the scope of the assessment, including the assets to be scanned, testing methods, and assessment goals.
- Vulnerability Scanning: Use scanning tools to identify vulnerabilities systematically, including known vulnerabilities, misconfigurations, and security gaps.
- Prioritization: Assess the severity of vulnerabilities and prioritize them based on potential impact, ensuring critical issues are addressed first.
- Reporting: Generate detailed reports with information about vulnerabilities, their severity, and recommended actions for remediation.
- Remediation: Address and fix identified vulnerabilities, requiring coordination between IT and security teams.
- Rescanning: Conduct follow-up scans to confirm the effectiveness of remediation efforts and maintain a secure environment.
- Final Report: Qualysec not only conducts follow-up scans. They also provide a complete report of the testing process they have conducted. This includes all their findings, which could be helpful for the organization
By following these steps and using the right tools, organizations can enhance their security posture. Mitigate potential risks from cyber threats.
Feel free to look into the whole structure of a sample report. Click and download the sample right now!
Latest Penetration Testing Report

Conclusion
Vulnerability scanners have become indispensable tools in the fight against cyber threats. Organizations use them to identify and address security weaknesses before malicious actors exploit them. As the threat landscape continues to evolve, staying ahead of potential vulnerabilities remains paramount.
In this blog, we’ve highlighted some of the top vulnerability scanning tools, each catering to specific needs and use cases. Whether you’re a web developer, network administrator, IT infrastructure manager, or a Managed Service Provider, there’s a vulnerability scanning tool that can help protect your assets.
Qualysec has a successful track record of serving clients and providing cybersecurity services across a range of industries such as IT. Their expertise has helped clients identify and mitigate vulnerabilities, prevent data breaches, and improve their overall security posture.
FAQs
Why are regular scans essential for staying ahead of vulnerabilities and threats?
A: Regular, automated scans are crucial because they continuously monitor your systems and applications for emerging vulnerabilities. This helps in keeping a check.
Why is experience an important factor in choosing a vulnerability scanning tool?
A: Experience matters because a tool with a proven track record. This is more likely to accurately identify vulnerabilities and provide effective solutions.
What role do integrations play in vulnerability assessment scanning?
A: Integrations allow the vulnerability scanning tool to work seamlessly with your existing security systems and processes. This streamlines your cybersecurity efforts and ensures a more comprehensive and interconnected security strategy.















































































































































































































































































































0 Comments