If you are an organization trying to better understand security vulnerabilities, defend against or comply with regulatory requirements, and proactively assess your risk posture, cybersecurity assessment services are crucial. This guide by Qualysec Technologies shows what such services involve, their types, benefits, and how they can be approached.
What Are Cybersecurity Assessment Services?
Cybersecurity assessment services involve an evaluation of an organization’s IT infrastructure, policies, and practices to determine the weaknesses and issues and propose remedies. They thereby determine the organization’s current security posture and prioritize measures to protect sensitive data and continue business operations.
Key Services of Cybersecurity Assessment Services
It is important to understand the types of assessments in cybersecurity to determine the best approach for your organization.
| Assessment Type | Purpose & Focus |
| Baseline Risk Assessment | High-level review of all technical assets and their management to pinpoint security gaps. |
| Penetration Testing | Simulated attacks on systems to evaluate defenses and uncover weaknesses. |
| Red Team Testing | Targeted simulations focusing on specific assets or data to test detection and response. |
| Vulnerability Assessment | Systematic identification and prioritization of weaknesses in systems and applications. |
| IT Audits | Detailed IT infrastructure review, policies, and procedures for compliance and security. |
Other than that, there are phishing simulations, compliance security audits, data risk assessments, and bug bounty program evaluations.
The Cybersecurity Assessment Services Process
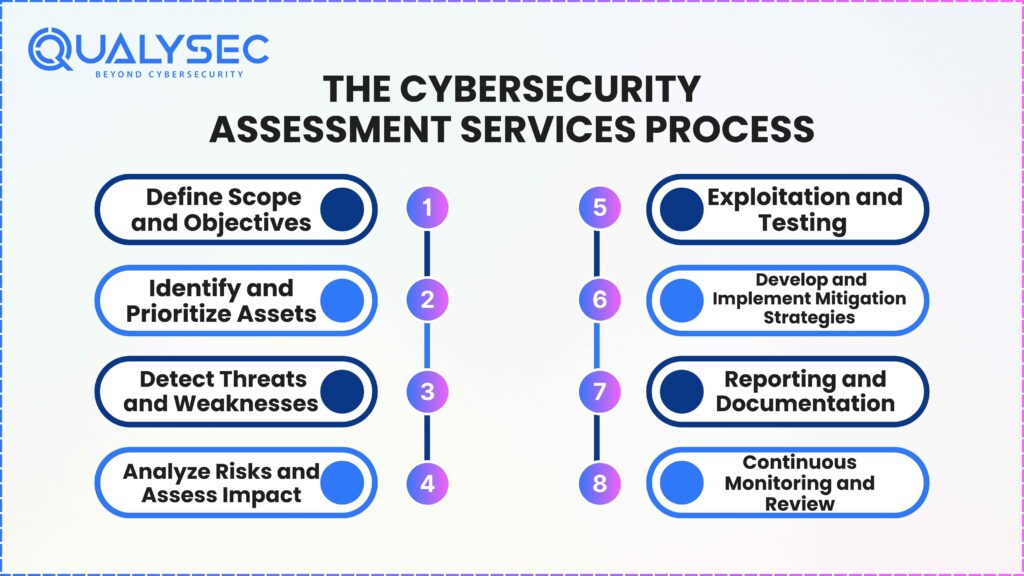
Understanding this structured cybersecurity assessment process is important for organizations to choose and focus on those risks and implement the cybersecurity measures to protect digital assets. The following is the process of how a complete cybersecurity assessment for businesses is accomplished –
1. Define Scope and Objectives
- Define the parts of the organization that will become the subject of the assessment, for example, the whole IT environment, specific business units, or some applications and networks.
- Involve stakeholders in the cyber threat assessment who are relevant to the critical assets and processes being assessed, and clarify objectives for the cybersecurity risk assessment. For instance, compliance, risk reduction, or policy improvement.
2. Identify and Prioritize Assets
- Identify all hardware, software, data, and network components.
- This should be done to evaluate each asset’s value to the organization, whether or not it contains any sensitive information, and whether the asset is essential to the operations.
- To prioritize assets, ensure that the cybersecurity assessment goes for the most important areas to assess and allocate resources efficiently.
3. Detect Threats and Weaknesses
- These identify Potential threats, such as internal or external actors, natural events, or process failures.
- Identify your environment catalog weaknesses, like outdated software, weak credentials, etc..
- You can find technical, physical, and procedural weaknesses using automated tools, manual reviews, and interviews.
4. Analyze Risks and Assess Impact
- How can the likelihood of occurrence of the threat be analyzed, and what is the potential impact it would have on business operations for every identified threat and weakness?
- You can assess and rank risks using risk matrices or scoring systems (low, medium, high).
- Think about motivation issues such as loss of financial, reputational, and operational disruption.
5. Exploitation and Testing
- Logically describe findings and contribute to the outlined objectives by conducting penetration tests and other simulated attack scenarios to validate findings and understand real-world implications.
- These cybersecurity assessment tests also allow us to verify if weaknesses can be exploited in practice and identify further holes in defenses.
6. Develop and Implement Mitigation Strategies
- Adopt technical controls (e.g., firewalls and multi-factor authentication), adopt updated policies, and provide training to the employees.
- Concentrate on both short-term solutions, improvements in processes, and controls in the longer term.
7. Reporting and Documentation
- Put together a specific hunting report that details answers to your observations, a list of the highest risks, and recommended remediation steps.
- Actionable guidance for technical teams and a clear leadership summary should be included.
- Documentation is a line through which you can be transparent and has a baseline so your work can be assessed and reviewed in the future.
Want to see real cybersecurity testing report? Download one here for free.
Latest Penetration Testing Report

8. Continuous Monitoring and Review
- The cybersecurity realm is living & breathing – it has to be continuously monitored & reanalyzed for new threats, and the controls need to be redefined as the systems and business requirements are modified, i.e., the controls are responsive.
- Reassess and update a mitigation strategy per schedule for an effective security posture.
Common Cybersecurity Assessment Tools and Techniques
A combination of automated tools and veteran techniques is the basis for an acceptable cybersecurity risk assessment. This process concerns identifying, measuring, and eliminating threats across an organization’s digital perimeter. Let’s proceed with a structured overview of the tools and methodology used by most of the industry.
Vulnerability Scanning
Automated vulnerability scanners scan systems, networks, and applications for weaknesses such as missing patches, weak configurations, outdated software, etc. This set of tools offers very detailed reports that allow for prioritisation of remedial efforts and keeping a healthy security baseline in check.
Penetration Testing
Penetration testing safely simulates real-world cyberattacks to check how well your security systems can handle them. Security experts use trusted tools like Metasploit to try to break into your systems, just like a real hacker would. This helps uncover hidden weaknesses that automated scans might miss. The main goal is to find and fix these issues before an actual attacker can exploit them.
Security Audits
The security audit includes an extensive check on security policies, procedures, and technical controls. They determine whether quality measures have been filed according to industry standards and their internal policies, and whether all of these measures are current and effective. Audit is a mandatory process to ensure regulatory compliance and further improvement.
Risk Assessments
It is aimed at identifying and prioritizing possible threats by their possibility of occurrence and impact. They can evaluate these risks by allocating resources to the problems that present the highest risks and putting strategies in place to mitigate them.
User Activity Monitoring and Behavioral Analytics
Some platforms, such as Teramind, offer an advanced level of monitoring users’ activities and behavioral analytics. They specify baseline activity patterns and identify anomalies, and, in addition, they identify potential data exfiltration pathways. The combination of these tools allows them to integrate with existing security stacks towards real-time monitoring, detailed audit trails, and intelligence to facilitate the risk assessment and compliance process.
Network and Asset Scanning
Nmap (Network Mapper) is a tool that scans IT systems and networks to find out what devices are there, check uptime, and spot entry points for attacks. These scans give security teams a bird’s eye view of network activity and allow them to be proactive.
Security Ratings and Automated Questionnaires
The objective, data-driven insights about an organisation’s security posture are provided by security ratings platforms. Through automated questionnaires, third-party risk management is streamlined for evaluating vendor security at scale and validating responses for transparency and accountability.
Integrating Assessment Services into Your Security Strategy
By assessing parts of your security strategy, you can ensure that you are not building security as a one-time thing but as an ongoing, adaptable one. Embedding these services is a matter of how.
Align Assessments with Business Objectives
- Start by mapping out key assets critical to business operations and that matter most to your customers’ business (and by a healthy margin).
- Decide on what you want to assess.
- Make sure that your assessment objectives are in sync with the business continuity, compliance, and risk management objectives.
Adopt Industry-Recognized Frameworks
- Use NIST CSF or ISO 27001 to establish the framework for conducting your assessment.
- These frameworks come with standardised methodologies such as structuring assessments, prioritizing risks, and aligning with regulatory requirements.
- A framework guarantees consistency, efficiency, and an agreed-upon way forward for ongoing improvement.
Establish a Repeatable Assessment Cycle
- Build it into your security program as a regular check box activity, but just help transform them into a continuous improvement loop.
There should be periodic reviews (quarterly, biannual, or annual) according to your risk profile and industry needs. - Findings from each assessment are used to update controls and refine policies, to inform training programs, and to identify what and when management should be trained.
Engage Stakeholders Across the Organization
- Start with at least the process owners, IT, risk managers, and executive leadership who will pull this work.
- Prove with examples how the cyber assessment results will make the company more resilient to business conditions and regulatory requirements.
- Use workshops and interviews to develop insights, test your hypotheses, and ensure others take ownership of security.
Act on Assessment Findings
- Assessment results are analyzed to understand gaps and ranked on risks based on their potential impact and likelihood.
- Draw up a targeted goal-achieving plan to prioritize the most crucial regions to begin with.
- Simply assign the individuals responsible for the remediation tasks and track the progress to the established milestones.
Integrate Technology and Automation
- Auto-discovery of assets, scanning vulnerabilities, and risk computing for assessments can be automated with automatic tools.
- Keep your technology stack in place and make sure it can monitor upcoming and quickly detect emerging threats.
Foster Continuous Security Maturity
- Each assessment should be treated as a way to determine progress, adapt to new threats, and increase your security baseline.
- Learn lessons from documents like these and use them to build your security strategy, enforcement, and audience awareness.
- Keep your IT risk assessment methodologies regular and updated regarding changes in your IT environment and threat landscape.
Enhance Compliance and Reporting
- Using assessment results, you can show that they compare with relevant standards and regulations and thus reduce audit risks.
- Supply leadership with plain, facts-driven insights to enable decision-making and confirm security financial investments.
How Qualysec Technologies Can Help in Cybersecurity Assessment Services
Comprehensive Security Assessments
With assessment services across web, mobile, API, cloud, and IoT environments, Qualysec provides end-to-end cybersecurity assessment services. The hybrid approach of combining manual expertise with automated tools gives a complete evaluation by finding the most complex weaknesses.
Industry-Leading Methodologies
Our process-based testing matches world standards such as PCI DSS, HIPAA, SOC 2, and ISO 27001. It helps businesses strengthen their security and facilitates easily achieving and complying with these standards.
Actionable, Detailed Reporting
Clear, prioritized reports are provided to clients about the fixed issues, with step-by-step remediation guidance. They are prepared in a way that technical and nontechnical personnel can understand the problems and fix them.
Expert Guidance and Support
A team of our professional certified experts ensures any issues identified will be solved, and your security posture will remain at its best.
Continuous Improvement
By updating methodologies and sharing insights as emerging threats emerge, Qualysec remains on top of the cybersecurity assessment services, helping your defenses stay equipped and strong against new threats.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
Modern risk management is based on cybersecurity assessment services. They give the views and guidance to guard possessions, remain compliant, and remain sturdy against shifting dangers. Knowledge of how the service works and the benefits of these services will allow organizations to decide and develop a culture of continuous security improvement.
Regarding security assessment, looking for a trusted partner such as Qualysec Technologies is essential to provide you with a complete solution that considers all your needs. Contact us today!



































































































































































































































































































































0 Comments