In today’s increasingly digital world, cybersecurity is no longer a luxury but a necessity. As businesses expand their digital footprints, the risk of cyber threats grows, demanding robust security measures. One such critical component of a comprehensive cybersecurity strategy is the Security Operations Center (SOC). A SOC as a Service (SOCaaS) is a centralized unit that oversees and controls an organization’s level of security. SOCs are responsible for identifying and responding to cyberattacks and preventing future attacks.
However, not all organizations have the resources or expertise to build and manage an in-house SOC. This is where SOC as a Service (SOCaaS) comes into action. This blog will provide an in-depth understanding of SOCaaS, its workings, benefits, roles, challenges, and tips for selecting the right provider.
What is SOC as a Service (SOCaaS)?
SOC as a Service (SOCaaS) is a subscription-based model that provides companies and businesses with the expertise and technology often offered by a third-party provider that monitors, detects, and responds to cybersecurity threats. Instead of investing in building and maintaining an internal SOC, organizations can outsource these functions to a third-party provider specializing in security operations.
SOCaaS is a cost-effective and scalable solution that allows businesses to leverage the skills of cybersecurity professionals and advanced security tools without the need for significant upfront investments.
SOCaaS providers offer 24/7 monitoring of an organization’s IT environment, identifying and mitigating threats before they can cause damage. This service is especially beneficial for small to medium-sized businesses (SMBs) that may not have the resources to establish a full-fledged security operations center.
How SOCaaS Works?
SOC as a Service (SOCaaS) works by assembling a vast number of security tools, technologies, and processes for a single comprehensive service aimed at constant monitoring and security of an organization’s IT environment. undefined
1. Threat Detection and Monitoring:
Monitoring tools are installed on the client’s network, end-user devices, and in the cloud by the SOCaaS provider. These tools actively scan for data from different sources to identify trends that are likely to be malicious.
2. Integration of Threat Intelligence:
Multiple threat feeds ensure SOCaaS has information on emerging threats and ways by which cyberattacks can be conducted. This is because it enables the SOC team to identify a range of new threats early enough to respond to them effectively.
3. Incident Response:
When a potential threat is detected, the SOC explores the matter; after the severity assessment, the procedure continues to eliminate the threat and secure the attack itself. The mitigation could be physical in form, where the infected systems are isolated, or procedural, where the traffic sources that pose a threat are blocked or the requisite security measures are taken in the form of patches.
4. Reporting and Analytics:
SOCaaS helps to work on specific incidents, as the providers submit detailed reports stating the nature of the threats, the actions that were taken, and tips on what else should still be done to enhance security. That is why such reports are necessary for organizations to have insights into their weaknesses and work out the necessary strategies.
Continuous Improvement:
The first and foremost aspect of SOCaaS is that the service needs to be constantly enhanced and developed. There are constant changes in threats, and the SOC team also tries to refine the process of defining threats, changing rules for threat detection, and implementing new tactics for handling the incidents.
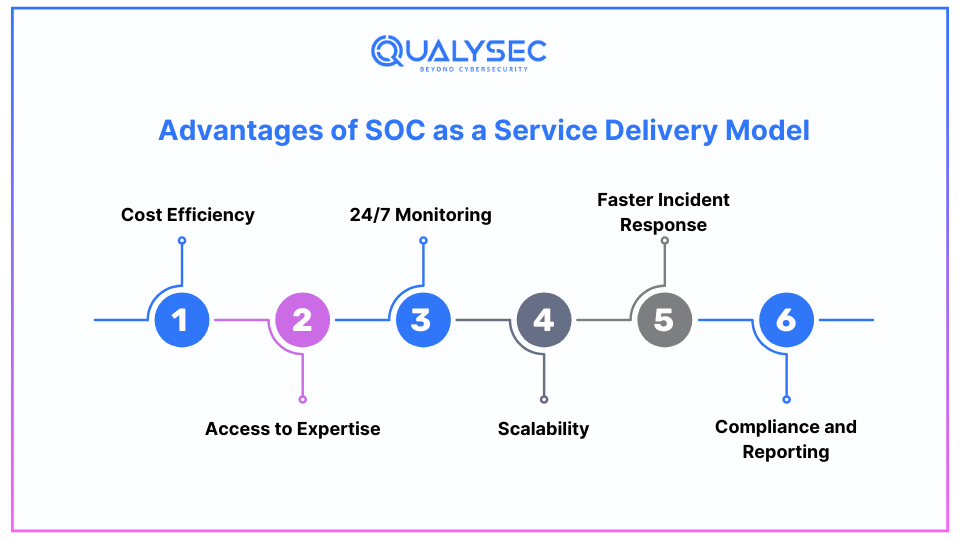
Advantages of SOC as a Service Delivery Model
The following are some benefits that businesses can derive from having SOCaaS or managed SOC services. Here are some of the key benefits:
1. Cost Efficiency: There are a lot of costs involved in the development and sustainment of an in-house SOC, such as technology expenses and personnel costs. These costs have been done away with by SOCaaS, which enables organizations to subscribe to superior security services without incurring the large costs of managing a SOC.
2. Access to Expertise: SOCaaS providers therefore hire professionals with a deep understanding of the threats, how to respond to them, and the intelligence to identify them. It is very useful, especially for companies that do not have information security specialists.
3. 24/7 Monitoring: Cyber threats do not respect business hours, which is why protection ought to be around the clock. SOCaaS guarantees that your IT environment is constantly being watched, thus minimizing instances where a hacker may go unnoticed.
4. Scalability: When your business expands, your security needs also increase. As mentioned earlier, SOCaaS is elastic and can be scaled up or down based on the organization’s requirements without the need to invest heavily in equipment and human capital. This expertise is invaluable, especially for businesses that lack in-house security professionals.
5. Faster Incident Response: Ways that SOCaaS helps you include fast identification of the event and response, thus reducing the effectiveness of threats. By having a SOC team around, threats are well noted and addressed to prevent maximum damage from being incurred.
6. Compliance and Reporting: Several industries experience significant prescriptive legal standards concerning the security of the data. These compliance standards are achieved by SOCaaS providers in assisting the organization to implement security controls and prepare the necessary reports for audit.
SOC as a Service: Roles and Responsibilities
SOCaaS providers, as a rule, take several key functions and obligations to safeguard an organization’s IT framework. Here’s an overview of the key roles:
1. Security Analysts: Security analysts’ duties include observing clients’ IT systems to evaluate security, conducting security testing; interpreting security alerts, and investigating threats. They also usually serve as a preliminary layer to analyze possible fraudulent schemes along with reporting suspicious events to other more endowed specialists if needed.
2. Incident Responders: Incident handlers are those employees who act during the security incident and try to control it and manage its consequences. To execute their work, they work closely with the IT department of the client to identify systems that have been infected, uninstall malicious code, and bring order back.
3. Threat Intelligence Analysts: Such people get acquainted with the latest cyber threats and trends, and impart it to the company’s SOCaaS platform. They assist in making sure that the SOC team is capable of identifying and dealing with the new threats as they are developed.
4. SOC Managers: A SOC manager is supposed to be in charge of all things related to a security operations center and the smooth functioning of the processes that take place there. They are supposed to directly oversee the SOC team, handle communication with customers, and ensure constant enhancement of the work.
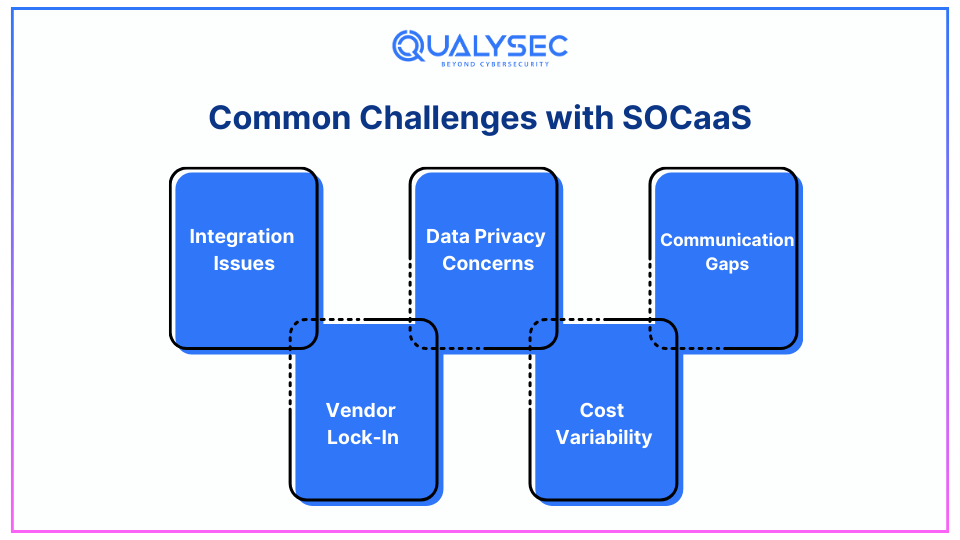
Common Challenges with SOCaaS
Organizations considering SOCaaS should be aware of the following potential obstacles, as shown below:
1. Integration Issues: Implementation of SOCaaS solutions to the existing organizational IT infrastructure can be problematic where that infrastructure is outdated or, at best, sporadic. This is particularly important to have adequate flexibility for the provider as well as to guarantee that all the client’s needs are met.
2. Data Privacy Concerns: A major challenge of outsourcing security operations is that you end up contracting a third-party service provider and sharing information with him. Any SOCaaS provider that should be selected should have strong provisions of data protection, together with a privacy policy well articulated.
3. Communication Gaps: To mitigate threats of miscommunication in the interaction, or delays of the reaction of the SOCaaS provider or the client, it is only necessary for the two to have proper communication. A major challenge of this sort of service delivery is that where there is poor communication, the system may be compromised.
4. Vendor Lock-In: They may do so deliberately, or it might be a result of proprietary technologies or special processes that make the clients become bound to the SOCaaS service. Organizations should therefore spare some time and read the terms of service not to be locked into any particular vendor.
5. Cost Variability: While compared to traditional outsourcing, it is usually cheaper in most SOCaaS the actual cost could vary depending on the level of service required as well as the complexity of the structure of the IT network of the client. It is now up to the businesses, should comprehend this pricing model so that other costs are not a shock.
Selecting A SOC As A Service Provider
The selection of the appropriate SOCaaS provider or SOC as a service companies is perhaps the most important decision that you would make for your company’s IT protection. Here are some key factors to consider when evaluating potential providers: Here are some key factors to consider when evaluating potential providers:
1. Expertise and Experience:
Research on the managed SOC providers should focus on their capability of providing SOCaaS. See how long they have been around and whether they have dealt with security issues similar to your business’s.
2. Technology and Tools:
Make sure that the provider utilizes threat intelligence solutions, advanced security analytics, and SIEM systems, as well as automated Incident response solutions.
3. 24/7 Monitoring and Support:
Ensure that the provider provides and avails 24/7 monitoring and assistance. At one point or another, cyber threats can arise, hence the need to be on the lookout constantly.
4. Customizability:
It may look like all businesses will require extreme security, but that is not the case. Select a provider who will offer you options that will suit your needs in the letter.
5. Transparency and Reporting:
This means that the provider should avail a clear reporting mechanism where they update the client on any current security threats, patterns, and the security status of his or her organization.
6. Compliance and Certifications:
Make sure that the provider complies with industry standards and that it has the necessary certifications, like, for example, ISO 27001 or SOC 2. This will help them to ensure that they are operating at their best, especially on issues related to do with data security and compliance.
7. Cost Structure:
Also, recognize the provider’s pricing strategy and constantly check if it suits your budget. One should be very cautious with the additional charges, which may often be concealed and the SLA should identify all the priced services.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
SOC as a Service (SOCaaS) is an indispensable service for any organization willing to strengthen its cybersecurity at the same time not wanting to create its SOC team. As a result, companies take advantage of professional security monitoring, fast response, and 24/7 control with the help of outsourced SOC providers as a partners instead of implementing their own SOC.
However, choosing the right SOCaaS provider also needs to take into consideration some of the areas, such as expertise, technology, and the costs of the service. It is therefore wise for businesses to use key factors in choosing SOCaaS to secure their assets from cyber threats.
FAQ
1. Why do I need SOC as a Service?
SOCaaS is vital for organizations that want to protect their IT infrastructure from cyber threats without the complexity and cost of managing an in-house SOC. It provides continuous monitoring, expert threat detection, and rapid incident response, ensuring that your business remains secure.
2. What key features should I look for in a SOCaaS provider?
Key features to look for in a SOCaaS provider include 24/7 monitoring, advanced security tools, threat intelligence integration, customizable services, transparent reporting, and compliance with industry standards.
3. How can Qualysec help with SOC as a Service?
Qualysec offers a comprehensive SOC as a Service solution customized to meet the unique needs of your business. With a team of experienced cybersecurity professionals and cutting-edge technology, Qualysec provides 24/7 monitoring, rapid incident response, and continuous threat intelligence.
Our SOCaaS platform is designed to integrate seamlessly with your existing IT infrastructure, offering customized security solutions that scale with your business. Additionally, Qualysec prioritizes transparency, providing detailed reports and actionable insights to help you maintain a strong security posture.
4. How much is SOC as a Service?
The cost of SOC as a Service varies depending on factors such as the size of your organization, the complexity of your IT environment, and the level of service required. Typically, SOCaaS providers offer flexible pricing models, including subscription-based plans that can be tailored to your specific needs.
It’s essential to discuss your requirements with the provider to get an accurate estimate. While SOCaaS can be a significant investment, it is often more cost-effective than building and maintaining an in-house SOC.















































































































































































































































































































0 Comments