Keeping the user’s data safe from cyber attackers is important. There are two ways to check for vulnerabilities. These assessments are known as vulnerability assessment and penetration testing. The difference between VA and PT (vulnerability assessment and penetration testing ) is that vulnerability assessment only identifies potential vulnerabilities. In contrast, penetration testing identifies vulnerabilities and provides insight into how these vulnerabilities might affect the network.
Conducting these assessments is necessary, as these provide insight into threats and vulnerabilities. Vulnerability assessments help the company to find areas that need to be fixed or strengthened. Penetration testing shows the firm how serious those vulnerabilities are and what could happen if they are not addressed. This blog provides a comprehensive guide on the differences between vulnerability assessment and penetration testing.
What is Vulnerability Assessment?
Vulnerability assessment involves cybersecurity experts using automated tools to find potential vulnerabilities. Thereby providing an analysis of the current security strengths and suggesting methods to improve them.
Vulnerability scanners like Burp Suite and Nmap have a fixed script, which is used to find known vulnerabilities. Despite being a quick method to find security vulnerabilities, this assessment doesn’t go deep into the application and may generate false positives.
What is Penetration Testing?
Penetration testing is a comprehensive testing process that involves ethical hackers, who manually try to find vulnerabilities that can be a potential threat to the application or network. Cybersecurity experts or ethical hackers use their hacking skills to test the system for each vulnerability. They also check how its security responds. if the experts successfully penetrate, then it’s a security flaw. These security issues are then documented and given to the company to rectify.
Penetration testing is important for businesses, as they are prone to cyber-attacks if their security system is weak or not strong enough. With a cyberattack, the entire operation of the business can be affected. This can also affect the sensitive information stored on the business computer systems.
Do you want to see a penetration testing report? Click the link below and check how the details of a pentest report can help with your business’s success!
Latest Penetration Testing Report

Vulnerability Assessment Vs Penetration Testing (VA/PT)
| Aspect | Vulnerability Assessment (VA) | Penetration Testing (PT) |
|---|---|---|
| Purpose | Identifies potential weaknesses and vulnerabilities in systems and networks | Actively attempts to find and exploit vulnerabilities in the given system |
| Approach | Uses automated scanning tools to detect vulnerabilities | Employs ethical hackers to simulate real-world attacks to find vulnerabilities |
| Main Goal | Find vulnerabilities for remediation | Find vulnerabilities, assess their impact level, and provide remediation methods |
| Frequency | Typically done more frequently | More comprehensive but resource-intensive. Done less frequently |
| Result | Provides a list of vulnerabilities to be addressed | Provides a realistic assessment of the security posture and potential security issues of the given system |
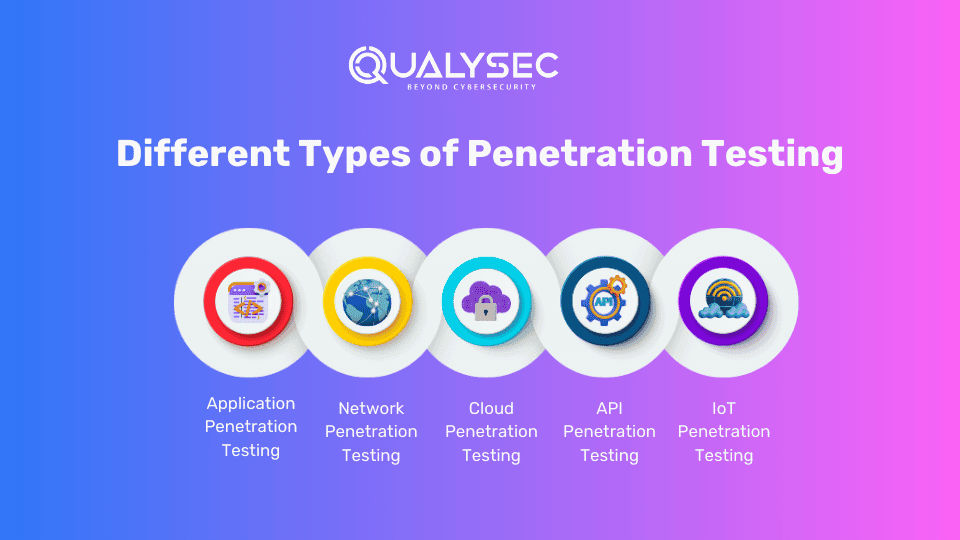
Different Types of Penetration Testing
- Application Penetration Testing: During this testing process, the consulting firm tests web apps, mobile apps, and other software for vulnerabilities. Common vulnerabilities include SQL injection and cross-site scripting. This process focuses on application code and logic.
- Network Penetration Testing: This process aims to test the company networks and its devices. This is done by exploiting weaknesses in firewalls, VPNs, and network devices to identify and mitigate the weaknesses.
- Cloud Penetration Testing: This process evaluates the security of cloud services, infrastructure, and configurations to identify potential vulnerabilities through comprehensive testing.
- API Penetration Testing: API pen testing is a process where the security of the application programming interface is tested. This is done by simulating attacks on authentication, data exposure, and misconfiguration.
- IoT Penetration Testing: During this testing process, cybersecurity experts identify vulnerabilities in Internet of Things devices, communication protocols, and associated apps/interfaces.
Different Modes of Penetration Testing
| Mode | Description | Knowledge Level |
|---|---|---|
| Blackbox | The tester has no prior knowledge of the target system’s internal workings, design, or infrastructure. They approach it as an external attacker would, with no information. | Zero knowledge of the system |
| Whitebox | The tester has complete knowledge and access to the target system’s source code, architecture, and internal details. They approach it from an insider’s perspective. | Full knowledge and access to the system |
| Grey box | The tester has partial knowledge and access to the target system’s internal details, such as network diagrams, software versions, or specific documentation. They combine elements of both black-box and white-box testing. | Partial or limited knowledge of the system |
VA/PT Compliance Regulations
| Regulation/Standard | Industry/Purpose | Role of VAPT |
|---|---|---|
| PCI DSS | Payment Card Industry, handling payment card data | Identify and resolve vulnerabilities to comply with PCI DSS rules. Thus, ensuring secure transactions and protecting data. |
| HIPAA | Healthcare sector, protecting patient information | Identify and address vulnerabilities that could affect patient information, ensuring confidentiality. |
| GDPR | Processing personal data of EU citizens | Identify and mitigate security risks, and also ensure compliance with GDPR’s data protection and privacy requirements. |
| ISO 27001 | Information Security Management Systems | Identify vulnerabilities and implement security controls to achieve and maintain ISO 27001 certification for information security best practices. |
Why should someone conduct VA/PT services?
| VAPT Services | Description |
|---|---|
| Identify Security Weaknesses | VA and PT help identify vulnerabilities in systems, networks, apps, and infrastructure that could be exploited by attackers, allowing organizations to address these weaknesses proactively. |
| Evaluate Security Defenses | PT simulates real-world attacks to evaluate the effectiveness of an organization’s security defenses and how well they can withstand and respond to cyber threats. |
| Compliance and Regulatory Requirements | Many industries and regulations like PCI DSS, HIPAA, and GDPR mandate regular VA and PT as part of their security and compliance requirements. |
| Risk Management | VA and PT services help organizations understand their actual risk level and the potential impact of successful cyber attacks. It is crucial for effective risk management and prioritizing security investments. |
| Secure New Systems and Applications | When implementing new systems, apps, or infrastructure, VA and PT can identify vulnerabilities and security gaps before production deployment, ensuring a secure implementation. |
| Stay Ahead of Emerging Threats | VA and PT services help organizations stay ahead of new attack vectors and vulnerabilities, ensuring their security measures remain effective against evolving cyber threats. |
| Improve Security Posture | Regular VA and PT help organizations continuously improve their overall security posture, reducing the risk of data breaches, system compromises, and other cyber incidents. |
Conclusion
In today’s cyber threat landscape, the question isn’t whether to do vulnerability assessments and penetration testing (VAPT). It is about which VAPT option best suits your needs. A comprehensive VAPT program with continuous scanning not only fortifies security but also fosters a security-first mindset. Also, it maintains compliance and builds customer trust.
When choosing a VAPT provider, look beyond the basics. Evaluate their scanning capabilities, industry-specific experience, methodologies, and team expertise. While VAPT requires investment, the return on investment in protecting against cyber attacks and breaches makes it worthwhile.
Qualysec has a good history of helping clients and giving cybersecurity services in many industries like IT. Their skills have helped clients find and fix vulnerabilities, stop data breaches, and make their overall security better. Choose Qualysec to secure your business today!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
FAQ
Q. What is the difference between VAPT and Pentest?
A: Both vulnerability assessment and penetration testing have the same goal – finding vulnerabilities in an IT system. However, vulnerability assessment uses automated tools to scan for vulnerabilities, while penetration testing involves ethical hackers simulating real attacks on the system to find vulnerabilities.
Q: What is the purpose of a vulnerability assessment?
A: The purpose of a vulnerability assessment is to identify vulnerabilities in an IT system. It Identifies security risks in applications and networks before attackers can exploit them.
Q. How many steps are in vulnerability assessment?
A: A vulnerability assessment typically involves several steps, which are:
- Asset discovery
- Prioritization
- Vulnerability Scanning using Automated Tools
- Result
- Report















































































































































































































































































































0 Comments