Ensuring an enterprise’s cyber security is vital as it secures assets such as customer information, financial records, and intellectual property from attack. The latest record shows an alarming rise in data breaches, with the media estimating that millions of documents are compromised annually, resulting in profits and damage to company reputations.
As the IT Governance study says, there were 29,530,829,012 data breach records as its research suggests.
In the age of technology, a business, regardless of its size, should also penetrate and test its resources to secure itself and its client trust. By the procedure of security protocols like penetration testing, the businesses will certify that they maintain the same level of protection and are also committed to maintaining the secrecy of data and being proactive in the cyber-attack world that is continuously changing.
This article will present a critical analysis of penetration testing and many facets like its goals, procedures, and methods. In general, the readers can take advantage of a deep knowledge of pen testing and the crucial role of the technique in a security-focused protection system. The only limit to learning is our curiosity.
What is Penetration Testing?
Penetration Testing or Pen Testing is a more proactive approach to evaluating the security of computer systems, networks, and applications. This process entails mimicking actual cyber-attacks on a company’s IT infrastructure to reveal potential vulnerabilities that malicious actors could take advantage of. The objective is to evaluate the efficiency of existing security measures and pinpoint any shortcomings before cybercriminals or unauthorized parties can leverage them.
Penetration is Essential for Aspect for Security for Diverse Motives
There are several reasons why penetration testing is an important security aspect. Firstly, it is imitating cyberattacks on a network, or an application to find vulnerabilities before the malicious actors take advantage of it. With this approach, organizations can upgrade their defense layers and respond to risks accordingly.
Identifying vulnerabilities:
Penetration testing makes it simpler for businesses to understand the vulnerabilities of their structures, networks, and applications. Further, pen testers identify vulnerabilities that could be exploited by malicious actors by simulating real attacks.
Risk evaluation:
With penetration testing, companies can verify the threat level related to diagnosed vulnerabilities. The test lets them prioritize remediation efforts based on the severity of vulnerabilities and their effect on employer capability.
Compliance Requirements:
Many regulatory requirements and compliance frameworks, along with PCI DSS, HIPAA, and GDPR, require businesses to carry out daily penetration as part of their protection capabilities.
Improving Security Posture:
Penetration testing offers precious insights into the effectiveness of modern security controls and measures. When agencies discover weaknesses, they can use that information to make informed selections about how to allocate resources to strengthen their altogether defensive posture.
Proactive Defense:
Instead of waiting for a cyberattack, penetration testing enables businesses to proactively discover and address security weaknesses earlier than they might identify via malicious actors. This proactive approach prevents security breaches and minimizes the impact on business enterprise abilities.
Building trust:
Penetration testing can assure organizations responsible for managing confidential client details, such as financial or health data, by building credibility with customers and partners. This practice demonstrates a dedication to protecting information and building confidence in stakeholders regarding the security of their data.
Types of Penetration Testing
Penetration Testing is considered an essential aspect of cybersecurity and includes several techniques for testing the security posture of systems and networks. Among these methods are the Black Box Testing, White Box Testing, and Gray Box Testing. In addition, each approach reveals different flaws and possible targets, responding to the security requirements of various situations. Knowledge of these methodologies is critical for the need to perform comprehensive security assessments and implement defenses against cyber threats.
Black Box Testing:
In black box testing, the tester does not know the computer or community being evaluated. This technique simulates an external attacker who has limited information about the application. Furthermore, black box testers depend entirely on external commentary and evaluation to understand vulnerabilities and capacity attack vectors.
White Box Testing:
White box testing, also called clear box or glass box testing, consists of the whole expertise of the machine’s inner structure, design, and source code. Furthermore, testers have got right detailed information about the machine’s configuration and implementation, and consider an extra thorough assessment of protection controls and vulnerabilities.
Gray Box Testing:
Grey box testing combines factors of both black box and white box testing. Testers have partial data about the system, typically inclusive of facts approximately its shape and layout but constrained access to source code or internal information. This technique allows testers to simulate insider threats or assaults wherein a few degrees of internal facts are assumed.
Best Practices Guiding Penetration Testing
Comprehensive testing that covers all aspects of the application or network with different techniques to find the vulnerabilities in depth is necessary. In addition, a risk-based approach focuses on threats, helping create strategic decisions that are most effective for hazard mitigation. Furthermore, documenting results and continual progress through reiterative testing effectively improves the security status of organizations. Together, these principles create an effective cybersecurity defense that can be the best way to shield from ever-changing threats.
Ethical Conduct
At a stage during the conducting of the test, penetration testers need to follow ethical recommendations and the boundaries of the crime. They should get legitimate authorization from the business however respect for privacy and confidentiality issues should be considered in advance before undertaking any kind of evaluation.
Comprehensive coverage
Testers must apply various strategies and techniques to thoroughly cover and detect vulnerabilities in all elements of the application or network being tested.
Risk-based technique
The defense should be together with risk assessment methods where threats are discovered and prioritized to make appropriate methods or strategies as they present an opportunity for the organization. Testers are required not only to evaluate the impact on capability as well as the possibility of exploitation for each susceptibility identified.
Documentation and reporting
Penetration test provides an in-depth look into the target infrastructure that should be extremely documented, including the information on vulnerabilities found, exploitation strategies applied, and remediation directions. Test reports should be clear, concise, and intended to be acted upon so that the stakeholders may be able to appreciate the findings and take necessary actions to improve protection.
Continuous development
The penetration and analysis efforts are iterative and should be repeated regularly, to stay up-to-date with the development of threats and changes in the system and community surroundings. Furthermore, companies must review these impacts to determine future safety improvements and investments.
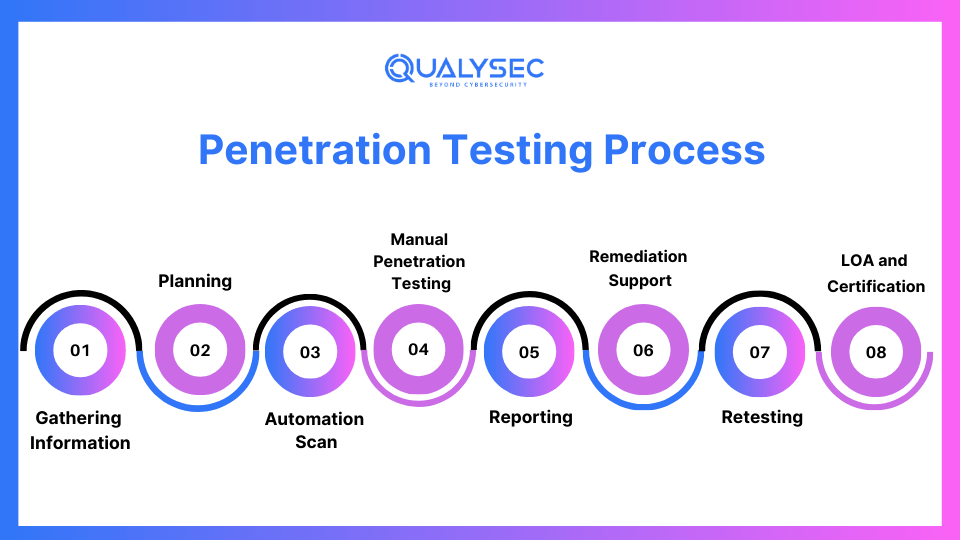
Penetration Testing Process
Application security and integrity are a high priority in today’s digital environment. In a changing threat landscape, continuous testing methodologies are essential to protect sensitive data and maintain stakeholder trust. This process provides a very structured method for gathering all the information, planning, testing, writing reports, providing remediation support, retesting, and finally certification. We do this through certain vulnerability scans and manual penetration testing. Through honest evaluation and careful monitoring, we build not only reports as well as the confidence that the application is resistant to all threats. Here is a complete overview of the penetration test process:
Information Gathering:
Use available resources and tools to collect data. Identify the technical and functional aspects of the application and define the user roles, permissions, and data flows for a comprehensive test approach.
Planning and Scoping:
The comprehension of the goals and objectives provides a background on which to consider the complexities of the application. Additionally, it involves the creation of a testing plan which includes the scope, approach, and criteria and the collection of the needed documents and instruments.
Automated Vulnerability Scan:
Performing an Amazon vulnerability assessment with the help of some specialized tools that detect surface-level vulnerabilities. Reproduce the attacks redirect the vulnerable requests through applications and reveal bugs in the security system.
Manual Penetration Testing:
Conducting more complex vulnerability testing manually with a focus on adherence to specific security standards and a complete evaluation of the authentication, data management, and other necessary aspects.
Reporting:
Explaining and classifying vulnerabilities for stakeholder awareness, and also pen test with top-level to look-see into the results. Ensuring that reports are provided complete with recommended actionable security measurements and advice for maintaining a persistent posture.
Remediation Support:
Enabling developers to maintain and repair the security flaws identified through the consultation calls. Collaborating to address security problems by analyzing and resolving them in time.
Retesting:
Conduct a thorough recheck of the results, in the end, to assume that the solutions were very smartly made and provide an informational report that is composed of case history, assessment status, and related screenshots.
Certificate:
Obtaining an LOA that would confirm the results and the compliance requirements. Give a security certificate that will prove the security of the environment and reassure the stakeholders.
Tools Used in Penetration Testing
Penetration testers utilize various tools to simulate attacks and check the security posture of the target environment. Here are some usually used penetration testing tools:
- Metasploit Framework: An open-source penetration testing framework that lets testers expand, test, and execute exploit code in opposition to faraway targets. It consists of a tremendous array of exploits, payloads, and auxiliary modules for numerous functions.
- Burp Suite: A comprehensive internet utility safety testing device used for performing protection testing out of web programs. Furthermore, it includes modules for proxying, spidering, scanning, and exploiting web applications.
- Wireshark: A community protocol analyzer that allows testers to seize and interactively browse the site visitors jogging on a computer community. It is essential for reading community packets and troubleshooting community troubles.
- Nessus: A widely used vulnerability scanner that permits identifying vulnerabilities, misconfigurations, and security troubles throughout diverse structures and applications.
- OWASP ZAP (Zed Attack Proxy): An intercepting proxy required for locating protection vulnerabilities in net packages during the improvement and testing stages.
Why Choose Qualysec for Penetration Testing?
Qualysec Technologies is the number one option for pentesting in various industry sectors and offers the best knowledge and expertise.
- Hybrid Testing Methodology: We utilize a combination of the latest automated technologies and advanced manual testing techniques. Qualysec guarantees the complete scope of issues covering trivial and complex vulnerabilities not detected by automated scans.
- Reporting Precision: Qualysec has meticulous and actionable reports that give you more details beyond vulnerability identification. Furthermore, the reports we produce have comprehensive analysis, strategic advice, and identified priorities to provide businesses with clear insights.
- Facilitate Compliance: At Qualysec, we believe that meeting industry standards will be considered your trusted ally in exceeding these benchmarks. Penetration test reports not only highlight compliance but also help protect data, which in turn fosters trust between stakeholders. Compliance includes PCI DSS, SOC 2, GDPR, HIPAA, and ISO 27001 standards.
- Solutions for Diverse Clients: Qualysec serves a broad range of clients including startups and Fortune 500 enterprises. Qualysec adjusts itself to face the different demands of each client.
- Proven Excellence and Reliability: Boasting an impeccable track record having protected 350 plus applications without recording a single data breach, Qualysec gives you confidence.
Qualysec Technologies is the most suitable partner for your secure digital assets through penetration testing because of its unparalleled combination of expertise, flexibility, and commitment to excellence. Select Qualysec for the service and confidence in the security of your critical infrastructure.
Conclusion
Penetration testing is a significant part of evaluating and enhancing the organization’s cyber security system. Furthermore, through simulation of real-world cyber-attacks, penetration testing provides intelligence of weaknesses and vulnerabilities that attackers can take advantage of. By actively utilizing risk assessment methods and validation procedures, businesses can discover and handle safety vulnerabilities. Thus, improving their resilience to threats to functionality.
Further, pentesting ensures the fulfillment of regulatory requirements and builds stakeholder confidence through the demonstration of adherence to cybersecurity standards. With an increase in the complexity of cyber threats, the active and iterative nature of penetration testing still works as a security measure in protecting sensitive information, securing industrial continuity, and awareness in multiple interconnected digital environments.
Qualysec has a proven track record of providing services to clients from different industries. They have helped clients detect and reduce vulnerabilities, prevent data leaks, and improve overall security through detailed cybersecurity reports. Furthermore, for enterprises in search of a trusted security partner to protect their online presence, Qualysec is the company. Talk to our experts and give your requisites to know more about our cybersecurity services.
Frequently Asked Questions
What is meant by penetration testing?
Penetration testing is a cybersecurity evaluation technique designed to discover and make the most vulnerabilities in computer applications and networks.
What are the three types of penetration tests?
Penetration testing encompasses three primary methodologies: Black-Box, White-Box, and Gray-Box Testing. In Black Box testing, the tester has no or little information about the target system or network beforehand. Alternatively, White-box testing is based on extensive information, whereas Gray-Box testing possesses partial information remaining as a middle ground between the two extremes.
What are the 5 phases of penetration testing?
Penetration testing follows a systematic process that begins with a reconnaissance phase to gather information about the system. Following a manual approach by a vulnerability scan using an automated tool that detects possible vulnerabilities. Manual penetration tests are conducted to verify and fully exploit these weaknesses. After that, a report is formed that summarizes the findings and makes detailed recommendations. After accomplishing corrective actions, the system is tested again to ensure the vulnerabilities have been rectified. A systematic method enables companies with the ability to identify and effectively address security risks.
Why is penetration testing important?
Penetration testing is a proactive approach that enables organizations to detect potential security weaknesses before malicious users exploit them. This reduces the likelihood of data breaches and financial loss. In addition, it facilitates compliance such as PCI DSS, HIPAA, and GDPR, demonstrating a commitment to data protection.















































































































































































































































































































0 Comments