Data is the current lifeblood of businesses, especially in the technologically advanced domain. It speaks of sensitive details of customers, proprietary products, and innovative ideas that help businesses thrive competitively. Keeping such valuable things safe has consequently become a new challenge for IT companies. As such, meets SOC 2 compliance-an absolute stringent auditing norm that has finally become the benchmark of optimal data security practices in business. Understand why the tech industries consider SOC 2 Compliance for Data Security through an analysis that elaborates on how this plays an essential role in the enhancement of security about data, winning customers’ confidence, and achieving competitive advantage at last.
What is SOC 2 Compliance?
SOC 2 is a voluntary compliance standard by the American Institute of Certified Public Accountants to investigate the controls of service organizations in these areas of security, availability, processing integrity, confidentiality, and privacy that concern customer data. The five core principles are termed “trust services criteria” and constitute the foundation of SOC 2 compliance.
Why SOC 2 Compliance is Important for Tech Companies?

Sensitive Information
Tech companies handle sensitive information that involves huge customer PII, financial information, intellectual properties, and trade secrets. Such an incident can result in loss of funds, damage to reputation, or even lead to potential legal liabilities. SOC 2 compliance stands as a critical framework for guiding strict security controls toward the implementation plan for the assurance of protection over such data. This includes access controls, encryption, and regular security assessments to minimize the risk of data breaches and unauthorized access.
Building Customer Trust
In this data-driven economy, customer trust is at the heart. Being perceived as serious about data security can help to form and maintain long-term customer relationships. Certification under SOC 2 acts as a strong signal to customers that a company takes data security very seriously and also takes proper steps to protect their information. It strengthens both trust and confidence, making it more likely for customers to form long-term relationships.
Compliance with Norms and Standards
Data security requirements especially after GDPR, CCPA, and HIPAA have become highly significant. SOC 2 compliance for data security implementation makes it easier for companies to prove adherence to such a regulation and thereby avoids paying expensive fines, penalties, and legal charges.
Competitive Advantage
Great competitive advantage can be demonstrated in the competitive marketplace under strict regulations of commitment to data security. Most organizations were willing to continue doing business with vendors that achieved SOC 2 compliance. Successful SOC 2 certification will allow tech firms to stand apart from the competition, attract new clients, and win big contracts with demanding clients.
Example: A SaaS company specializing in CRM software lost a significant contract with a financial institution. The financial institution had very stringent requirements about data security that mandated all vendors must be SOC 2 compliant. Being SOC 2 compliant, the SaaS company proved its commitment to data security, and it went on to win the contract, further exponentially increasing its customer base.
Steps of SOC 2 Compliance for Data Security
Reaching SOC 2 compliance requires a step-by-step approach to planning and executing these steps.
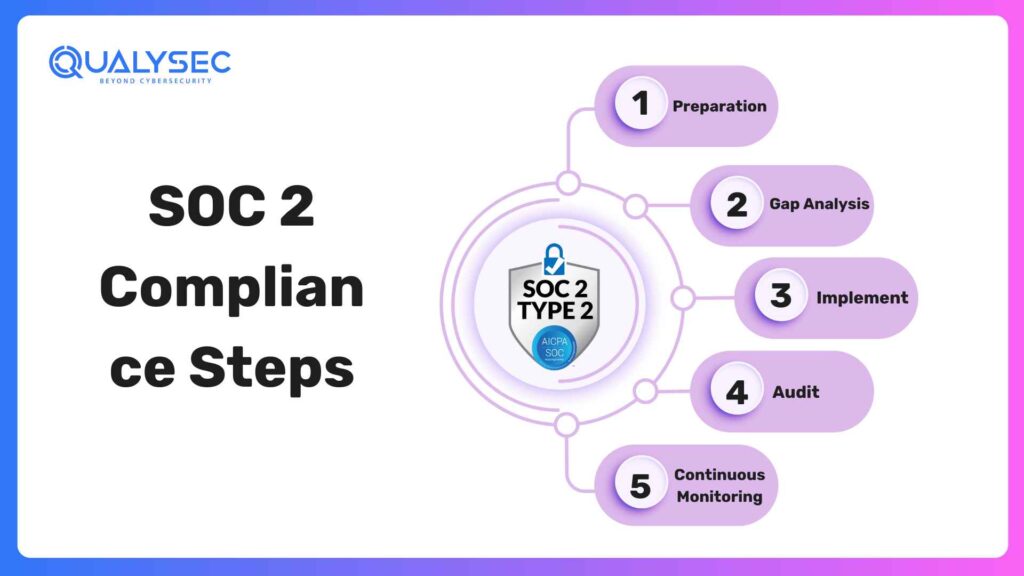
1. Preparation:
- Scope Definition: Clear definition of what the scope of the audit includes, including what systems, processes, and data would be assessed.
- Understanding the Requirements: Having a good grasp of the specified requirements, security, availability, processing integrity, confidentiality, and/or privacy, from the chosen SOC 2 trust services criteria.
2. Gap Analysis:
- Gap analysis includes the analysis of existing security controls to identify if there exists a gap between the current practices and SOC 2 requirements. The list includes reviewing the existing policies, procedures, and technologies, where applicable, and conducting risk assessments.
3. Implement:
Implement necessary security controls to address identified gaps. This may include:
- Access Controls: Implementing strong password policies, multi-factor authentication, and least privilege access controls.
- Data Encryption: Encrypting data both in transit and at rest.
- Incident Response Plan: Develop and implement a comprehensive incident response plan to promptly address and contain security incidents.
- Security Awareness Training: Holding regular security awareness training on security best practices for employees and staff.
- Documentation: Document any security policies and procedures as well as controls to be used
4. Audit,
- Engage with a qualified or independent auditor qualified to carry out an in-depth examination of the organization’s systems and its controls.
- The auditor will review the implemented controls and report whether or not the organization has complied with the chosen trust services criteria.
5. Continuous Monitoring:
- Monitor and maintain ongoing security controls to ensure uninterrupted compliance. For instance, there could be periodic security assessments, vulnerability scans, and penetration testing.
- Real-Time Example: One of the fast-growing tech startups specializing in AI-powered marketing solutions, realized the need to be SOC 2 compliant while seeking enterprise clients. They took up a strong compliance journey as they first conducted a detailed gap analysis. They then implemented several security enhancements. Some of them include multi-factor authentication, the encryption of customer data, and scheduled security audits. All these preventive measures helped the company achieve its SOC 2 compliance successfully and hence increased customers’ confidence which could help them seal large contracts with Fortune 500 companies.
“Also Read: A Comprehensive Guide to SOC 2 Penetration Testing“
Latest Penetration Testing Report

Case Studies: SOC 2 in Action
Case Study 1: A SaaS Company
Early Issues: A SaaS firm offering customer support software was constantly being pushed by enterprise customers to show evidence of good data security practices. The company had minor security breaches in the past, which undermined customer confidence.
They went ahead and implemented the SOC 2 full-scale compliance process. The entity created more advanced controls over access and encrypted all its sensitive data, ensuring comprehensive incident responses while creating awareness-security programs to enhance their employee awareness of security.
Outcomes: After SOC 2 compliance, the SaaS company experienced a significant increase in customer retention and a high inflow of new business inquiries from enterprise clients. The certification was a strong competitive advantage and helped rebuild customer trust.
Case Study 2: A FinTech Firm
Compliance Requirements: In this regard, FinTech firms specializing in online payments should comply with strict regulatory requirements from financial institutions and payment card companies. Such regulations highlighted the need to have sound data security and privacy concerns.
SOC 2 Implementation: The FinTech company had implemented a broad set of security controls. They included access controls, encryption, and intrusion detection systems. Additionally, the company had a dedicated security team that monitored and responded to security threats.
Outcomes: Obtaining SOC 2 compliance was a very good milestone for the FinTech company, as the attainment demonstrated and showed its concern for data security and met the high demands of its partners and regulators. They were able to get very valuable partnerships with top financial institutions and maximize their customer base.
Challenges to Obtain SOC 2 Compliance
There are challenges associated with SOC 2 compliance; it depends on the organization:
Cost High: Attainment and continued preservation of SOC 2 can become expensive in themselves. Some expenditures include the setup of new security controls, an approved auditor’s engagement, and continuous monitoring as well as maintenance services.
It is quite challenging and involves complex processes due to the generally inflexible SOC 2 compliance regulations.
Resource-Intensive: The entire compliance process, from the scoping phase to achieving compliance certification, is time-consuming, especially in small organizations that lack resources.
Viewpoint of Solutions:
Organizations can overcome these drawbacks by:
- Using automation tools: Automated security solutions can automate most aspects of the compliance process, such as vulnerability scanning and log management.
- Experienced consultants are engaged: Consultation of security and compliance experienced professionals gives advisory and support throughout the compliance journey.
- Phased implementation with priority: Implementing compliance in phases would be cost-effective and lighten the load on the organization as a whole.
Beyond Data Security: Benefits of SOC 2 Compliance
Other than the benefit of bettering data security, SOC 2 compliance brings forth many other crucial benefits.
- Enhancing the Operational Effectiveness of the Organization: Process streamlining as well as security controls implementation along the way towards SOC 2 compliance often helps in improving the organizational operational effectiveness along with reduced operational risk.
- Effective Risk Management: SOC 2 compliance assists organizations in early identification, risk analysis, and elimination of any potential security risk. This does not allow an organization to have costly data breaches or other types of security incidents.
- Investor Confidence Increased: It shows that the firm has a good governance framework that instills increased confidence in the investor. Thus, it boosts the overall reputation of the firm, hence increasing brand value.
Protection of Sensitive Information
Tech companies deal with sensitive information which may include vast customer PII, financial information, intellectual properties, and trade secrets. In such a situation, such an incident may cause a loss of money, harm the reputation, or even trigger some potential legal liabilities. Hence, SOC 2 compliance for data security forms an important framework providing guidelines for implementing stringent security controls to ensure protection over such data. This includes access controls, encryption, and regular security assessments to minimize the risk of data breaches and unauthorized access.
Building Customer Trust
In this economy, being driven by data, customer trust would be of utmost importance. Being perceived as serious about data security could help to enhance and sustain long-term relationships with customers. Certification under SOC 2 becomes a strong signal to customers that a company is serious about data security and also takes proper measures to protect their information. This cements both trust and confidence, creating a likelihood of long-term customer relationships.
Future of SOC 2 Compliance in the Tech Industry
The landscape related to data security and compliance keeps changing every moment.
Emerging Trends
- Growing importance of cloud security since the business is moving to cloud-based services.
- Rise of AI and potential implications for data security and compliance.
- Increased focus globally on data privacy and the emergence of new regulations.
Role of AI and Automation
- There are a multitude of reasons why AI and automation technologies are going to have a key role to play in attaining and then maintaining SOC 2 compliance.
- To be used to automate threat detection and response, perform vulnerability assessments, and log analysis with the help of AI-powered tools.
- Automation becomes helpful in streamlining many aspects of the compliance process, from security monitoring to security reporting.
Predictions
- The near future is probably going to enforce stringent regulations and enhance the demand for SOC 2 compliance due to the evolving landscapes of regulation as well as enhanced sophistication in cyber threats.
- Global markets will require data security practices and SOC 2 compliance for any organization to succeed in global markets.
Conclusion
In the digital world, data security is no longer a secondary but rather a core business imperative for any tech company. SOC 2 compliance offers a robust framework that enhances data security, builds customer trust, and provides a competitive advantage.
By focusing on SOC 2 compliance, tech companies can show that they are committed to data security, meet evolving regulatory requirements, and protect their most valuable asset: their data. Achieving and maintaining SOC 2 compliance is a significant investment and effort, but the long-term benefits include increased customer trust, enhanced operational efficiency, and reduced risk, all of which far outweigh the costs.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Partner with Qualysec to achieve seamless SOC 2 compliance and elevate your data security standards. Our expert-driven solutions ensure your business stays ahead of regulatory requirements, builds trust, and minimizes risks. Start your journey toward robust security and compliance today with Qualysec—Your Trusted Cybersecurity Partner.
Contact us now to get started!


















































































































































































































































































0 Comments