Today’s world is digital and interconnected, and therefore, cybersecurity has become imperative for organizations to secure their data and infrastructure against cyberattacks. One of the most common methods to analyze and identify cybersecurity vulnerabilities is by conducting external penetration testing. Discovering the loopholes before the hackers can exploit them is a preventative strategy. Here, the blog will thoroughly analyze external penetration tests. Additionally, sheds light on their importance, methodologies, checklists, and the differences from the vulnerability scanning process.
What is External Penetration Testing?
External penetration testing (also known as external network penetration testing) is a method of evaluating the security of a network or system through the eyes of an outsider that simulates actual cyberattacks. Skilled professionals, known as ethical hackers, try to breach system security by exploiting vulnerabilities in network defense to find how strong or weak their security defenses are.
They intend to use different methods to detect those flaws that attackers could use to penetrate systems unauthorized or cause disruption. Hence, external hacking helps organizations deal with their vulnerabilities beforehand, reduce or avoid risks, and secure critical information from outside threats.
Internal vs external pen testing
Internal and external penetration testing are both crucial components of a comprehensive cybersecurity strategy, but they differ in scope and focus:
Internal Pen Testing
| Factors | Descriptions |
| Objective | The primary role of internal penetration testing is to replicate an attack inside the organization’s network. This may result from the compromised end-point or via the invader who found their way into your network without permission. |
| Scope | It delves into the security of internal systems, servers, databases, applications, and other resources accessible through the organization’s network. |
| Methods | Generally, internal penetration testers are granted access to an organization’s network at a higher level than external testers. They can rely on many ways to abuse security gaps and penetrate further into sensitive data sources and crucial systems. |
| Benefits | Hacking internal security control system vulnerabilities enables the enterprise to strengthen its defenses against insider threats, viruses, and other internal risks. |
External Pen Testing
| Factors | Descriptions |
| Objective | External Penetration Testing portrays attacks outside the organizational network boundary using the same strategies hackers or other cybercriminals use. The aim is to discover and take advantage of these security gaps, which might be done to hack the network. |
| Scope | It evaluates the security of the external systems that serve as interfaces to external systems like web servers, email servers, firewalls, and other internet-facing resources. The attention is centered on enumerating vulnerabilities that can be exploited by hackers who do not have any access to the organization’s network beforehand. |
| Methods | External penetration testers work like external attackers, performing actions such as network scanning and vulnerability exploitation, resulting in unauthorized access to the organization’s systems. |
| Benefits | By finding the weaknesses before hackers do, external penetration testing assists businesses in protecting their external infrastructure and proactively preventing potential data breaches. |
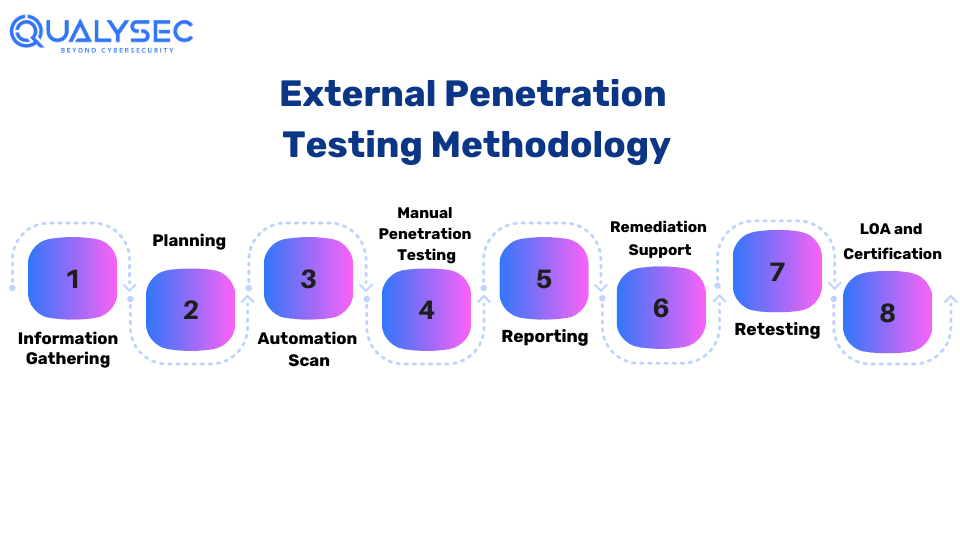
External Penetration Testing Methodology
Here is the step-by-step explanation of the process of conducting external penetration testing:
Step 1: Information Gathering:
The testing firm collects extensive data through different techniques to determine the system architecture, technologies, and vulnerabilities. This encompasses researching public information and conducting reconnaissance operations to reveal entrance points and weak spots in the network or app’s security.
Step 2: Planning:
Here, they establish testing goals, scope, and appropriate methodology relevant to the organization’s needs. They create a complete plan with detailed testing methodologies, tools, and techniques. This stage connects the testing objectives and the organization’s security specifications.
Step 3: Automated Scanning:
The testers use automated tools that scan the target network or application for known vulnerabilities. This phase aims to enable the fast detection of prevalent security problems by efficiently identifying superficial vulnerabilities.
Step 4: Manual Testing:
Then they conduct a thorough manual penetration testing to reveal the vulnerabilities an automated scan failed to detect. Using simulations of real-world attack scenarios, security professionals connect with systems to uncover complex security assumptions and assess entry points for potential adversaries, ensuring the thoroughness of the testing process.
Step 5: Reporting:
The testers then record and classify found vulnerabilities from the information collected during the tests. They create a detailed penetration testing report for stakeholders with actionable recommendations for fortifying the security posture of the organization’s systems and applications.
If you’re looking for the best pen test report to gain clarity, it’s just a fingertip away. Click below for the sample report.
Latest Penetration Testing Report

Step 6: Remediation Support:
The pen testing firm helps the development team to solve the identified vulnerabilities effectively by providing guidance and assistance. With scheduled consultation calls and direct engagement, penetration testers offer expert advice to enable efficient and complete resolution of security issues.
Step 7: Retesting:
Then the testers conduct a thorough re-evaluation of previously identified vulnerabilities. This step confirms that previously identified issues have been effectively resolved and validates the organization’s security enhancements.
Step 8: LOA and Security Certificate:
To certify the organization’s security posture, the testing company provides a Letter of Attestation (LOA) with evidence from penetration testing. This document provides clear evidence of security standard compliance. It, therefore, can be used to reassure stakeholders, clients, and regulatory agencies of the organization’s commitment to cybersecurity.
External Penetration Testing Checklist
External penetration testing is the structured approach used to determine the safety of the organization’s network from outside threats. Here are five essential points typically included in such a checklist:
1. Enumeration and Reconnaissance:
This involves obtaining information about the target network, like IP addresses, domain names, network infrastructure, and services running on external systems. Techniques such as DNS enumerating, port scanning, and service identifying are frequently employed.
2. Vulnerability Scanning and Assessment:
It identifies potential security vulnerabilities in external network infrastructure by conducting vulnerability scans. This involves detecting outdated software, misconfigured services, open ports, and known network and server vulnerabilities.
3. Exploitation through Penetration Testing:
To attempt to use known vulnerabilities to get encrypted entry to the target network or systems without permission. This stage uses penetration testing tools and techniques to simulate cyber-attacks such as remote code execution, SQL injection, cross-site scripting, and other commonly exploited weaknesses.
4. Post-Exploitation Activities:
To simulate real-world attack scenarios by performing various post-exploitation activities, such as lateral movement, data exfiltration, and persistence techniques. This step helps evaluate the network’s resilience against advanced persistent threats (APTs) and assesses the organization’s detection and response capabilities.
5. Documentation and Reporting:
The documentation should encompass the entire penetration testing process by providing a host of information, such as findings, methodologies, tools used, and recommendations for remediation. A detailed report is next prepared summarizing the findings. Furthermore, it includes vulnerability detection, its severity, potential impact, and recommendations to enhance the security of external network infrastructure.
Are you looking for more details regarding external penetration testing? Schedule a call to speak with our Experts for Free!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
External penetration testing or vulnerability scanning?
External pen testing and vulnerability scanning are both essential components of a comprehensive cybersecurity strategy. However, they serve different purposes and utilize different methodologies:
| Differences | External Penetration Testing | Vulnerability Scanning |
| Purpose | External penetration testing is when an actual attack on a company’s network or systems is simulated from the outside. Therefore, the purpose is to discover the gaps that malicious actors can use to access the organization’s assets without their knowledge. | Vulnerability scanning is a proactive assessment of security weaknesses within the system or network with the help of automated scanning tools. Additionally, it involves scanning the infrastructure to detect known vulnerabilities, errors in configuration, and other issues that can allow hackers to take advantage of the conditions. |
| Methodology | Ethical hackers (penetration testers) employ tools and methods analogous to those actual hackers use. Such a scenario could imply surveying to gather information about the target, using the known vulnerabilities and escalating privileges to gain deeper access. | A vulnerability scanner automatically scans networks, systems, and applications for known vulnerabilities by matching pre-defined signatures or patterns. These scanners will be able to identify issues like missing security patches, weak passwords, open ports, and insecure configurations. |
| Outcome | The critical result of external penetration testing is learning about an organization’s security status, including all the vulnerabilities the attackers might exploit. Hence, this information can subsequently be used to strategize and focus on areas of improvement and strengthen the organization’s defense. | The primary goal of vulnerability scanning is to generate a report of the detected vulnerabilities and their severity levels. Further, this data allows applications and organizations to concentrate on the vulnerabilities that attackers can exploit and prioritize, thus minimizing risks to the organization. |
Conclusion
External penetration testing is critical for enterprises to identify and address vulnerabilities in their external infrastructure. It helps in improving their overall cybersecurity posture. Organizations can better defend themselves against external assaults and protect their critical assets and data by replicating real-world cyber risks.
External penetration testing enables firms to keep one step ahead of cyber threats and successfully manage potential risks by conducting thorough reconnaissance, using systematic testing procedures, and reporting extensively.
FAQs
Q. What is an external penetration test?
A. The external penetration test is a cybersecurity assessment where authorized cyber professionals simulate penetration outside the network’s perimeter to look for vulnerabilities and determine the security posture.
Q. What is the internal penetration test?
A. Internal penetration testing works on the principle of simulating authorized users attacking the network to expose vulnerabilities, misconfiguration, or weaknesses. This can be in the form of systems, applications, or infrastructure. Hence, this aims to enhance cybersecurity defenses and address the risk adequately.
Q. What are the three types of penetration tests?
A. There are three kinds of penetration tests: Black box testing, white box testing, and gray box testing. Furthermore, Black Box testing performs systems analysis without prior knowledge, White Box testing goes through internal structures, and Gray Box testing combines both elements.
Q. How long does external network penetration testing take?
An external pen test typically takes one to two weeks to complete, depending on various factors, including the target systems’ scope, complexity, and size.
Q. How much does external pen testing cost?
The cost of an external pen test varies widely, influenced by factors like the organization’s size, the scope of the project, network complexity, and the expertise of the testing provider. Contact us to get an exact price quote.













































































































































































































































































0 Comments