© 2024 Qualysec.com Disclaimer Privacy Policy Terms & Conditions
The current shift in the cybersecurity realm makes it necessary to prioritize the fundamental issue of searching for bugs and risk. The blog focuses on several steps that you can follow to identify any security flaws. It mentions the importance of these steps, how to perform them, and their impact on online security strategies. The blog then proceeds to explain vulnerability assessment. It provides learners with the opportunity to identify weak areas, enabling firms to plan defenses against online threats.
It is important to identify potential threats and vulnerabilities to secure the system by carrying out comprehensive vulnerability Assessment Steps. Classify vulnerabilities in a systemic or networked manner for distinction. Through the implementation, businesses could find a more suitable way to overcome security risks and comprehensively defend themselves.
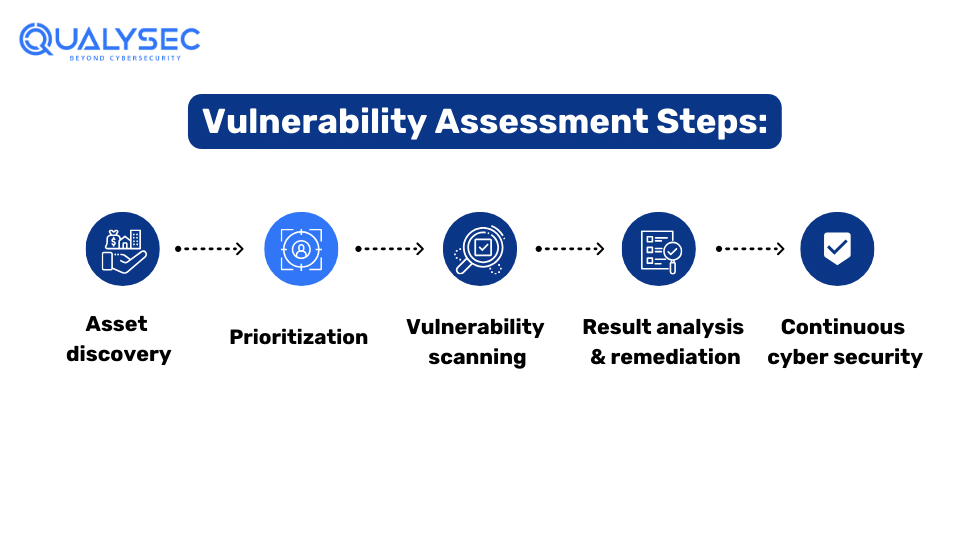
In the step of Asset Discovery, the team recognizes the company’s assets. These assets include networks, applications, physical hardware, web applications, etc. Once identified, the assessment provider prepares these assets for assessment and prioritizes them based on the company’s needs.
After the asset discovery, the organization prioritizes each asset. This categorization is based on the sensitivity and the importance of the business. The gaps are then re-addressed and then the assessment team moves on to the next process in the vulnerability assessment security.
During the vulnerability scanning the team uses automated tools to search for weak points. The usage of advanced software can help identify security gaps, misconfigured network settings, and outdated software, which hackers can exploit. It is suggestible to scan for vulnerabilities frequently so that newly discovered vulnerabilities can be detected faster.
After the vulnerability scans are performed, the next step is to analyze the results and then prepare a list of the high-risk vulnerabilities the organization faces. This includes the analysis of every vulnerability, such as exploitation risk and the negative effect on the organization’s assets.
Continuous cybersecurity is an important part of vulnerability assessment. It involves various aspects such as monitoring, detection, and response to cybersecurity threats. Organizations need to constantly scan their digital assets to protect them from evolving cyber threats.
Feel free to look into the whole structure of a sample report. Click and download the sample right now!
| Benefit | Description |
|---|---|
| Risk Mitigation | Risk mitigation helps in avoiding loss of data from potential assets of the client’s data. Vulnerability scanning identifies which assets are prone to risks and thus could be mitigated. |
| Compliance | Meeting routine vulnerability scan requirements based on public and industry/government guidelines (e.g., PCI DSS, GDPR). |
| Cost Savings | Dealing with vulnerabilities early in the development cycle to avoid significant losses from data breaches and prevent security-related downtime. |
| Enhanced Security Posture | Establishing a more effective and efficient security system through vulnerability assessments. |
| Customer Trust | Demonstrating dedication to security through regular vulnerability assessments, and building customer loyalty and confidence. |
| Competitive Advantage | Using a strong security posture as a competitive firm attracts customers who prioritize security. |
Qualysec is widely famous for detecting vulnerabilities and risks. They have many services available to people such as the VAPT (Vulnerability Assessment and Penetration Testing), where they find vulnerabilities before hackers.
Although Qualysec’s main office is in India, they are known as one of the best cybersecurity companies in the world, since they have a thorough understanding of the subject and are very successful in it. Experts at Qualysec can detect weak points that cyber attackers may exploit. By finding vulnerabilities, Qualysec comes up with a mitigation strategy in collaboration with the company. This enables the company’s security to become better. They provide various other services which are:
At Qualysec, a team of cybersecurity experts, tackle and investigate security attacks that give the upper hand against their clients in security solutions. They provide VAPT Services through the latest procedures and approaches.
Qualysec implements industry standards and provides step-by-step results so that clients can easily understand and fix problems. Qualysec’s solution is perfectly meant for organizations with strict industry regulations or clients who need to evidence their commitment to privacy and security to vendors and other relevant parties. Through continuous testing, businesses can reveal those weaknesses right away and fix them before hackers exploit them.
Qualysec offers top-of-the-line vulnerability assessment and penetration testing for web applications, mobile apps, cloud, IoT devices, etc. along with source code review and Vulnerability Assessment. Contact Us Now!
Conclusion
Vulnerability assessments is very important in the fight against cyber threats. Companies use them to find and fix security problems before hackers can take advantage of them. As more and more cyber threats appear, it’s very important to stay ahead of possible security problems.
In this blog, we’ve talked about vulnerabilities and how it works. Generally, vulnerabilities are found with the help of vulnerability scanners. So whether you’re a web developer, network administrator, IT infrastructure manager, or a managed service provider, there’s a vulnerability scanning tool that can help keep your digital assets safe.
Qualysec has a good history of helping clients and giving cybersecurity services in many industries like IT. Their skills have helped clients find and fix vulnerabilities, stop data breaches, and make their overall security better.
Q: How does a vulnerability assessment work?
A: During a Vulnerability Assessment, the assets of the firm are analyzed and scanned for potential weaknesses or flaws. The process involves using automated tools to identify vulnerabilities. Thus making it reliable and effective.
Q: What is a vulnerability assessment?
A: A vulnerability assessment stands for the identification of security flaws that can hamper the organization’s current workflow. To avoid this from happening a process is implemented, which is known as Vulnerability assessment.
Q: Why are vulnerability assessments important?
A: Vulnerability assessments are important because they help organizations to identify and also prevent the loss of organizations’ data to potential threats. Security defense and risks are mitigated through vulnerability assessments and hence they are important.
Q: What is the purpose of a vulnerability assessment?
A: The purpose of a vulnerability assessment is to identify and mitigate the vulnerabilities in the client’s system or applications before they can be exploited.
Q: How many steps are in vulnerability assessment?
A: A vulnerability assessment typically involves several steps, which are, asset discovery, prioritization, vulnerability scanning, result, and report suggestion.
Q: How do you perform a vulnerability risk assessment?
A: To perform a vulnerability risk assessment, organizations can follow these steps:





Plot No:687, Near Basudev Wood Road,
Saheed Nagar, Odisha, India, 751007
No: 72, OJone India, Service Rd, LRDE Layout, Doddanekundi, India,560037
© 2024 Qualysec.com Disclaimer Privacy Policy Terms & Conditions


No: 72, OJone India, Service Rd, LRDE Layout, Doddanekundi, India,560037
© 2024 Qualysec.com Disclaimer Privacy Policy Terms & Conditions