© 2024 Qualysec.com Disclaimer Privacy Policy Terms & Conditions

With their extensive network and a huge amount of sensitive data, multinational corporations (MNCs) are a major target for cyberattacks. Regular cybersecurity penetration testing is important to secure these enterprises from evolving threats. It is the process of employing cybersecurity professionals to test your systems and networks for vulnerabilities that hackers could exploit.
Penetration testing will help secure businesses from cyber threats and comply with industry regulations. In this blog, we are going to learn about cybersecurity penetration testing, what are its types, and why it is important for multinational corporations.
So, let’s start!
Hackers continuously develop new techniques and tools to exploit vulnerabilities in MNCs’ networks, applications, and other digital assets. As a result, cybersecurity has become mandatory if they want to prevent their organization from huge losses.
Statistics show that 2,200 cyberattacks happen every day, with a cyberattack happening every 39 seconds on average. Yes, you read that right! Before you brew a cup of coffee, there had been a cyber attack somewhere. Bank of America, Hewlett-Packard Enterprise, AnyDesk, and Infosys are some of the major corporations that recently faced a cyberattack. As per Statista, cybercrimes on US-based organizations have grown exponentially over the years and are predicted to cost approximately $1.8 trillion by 2028.
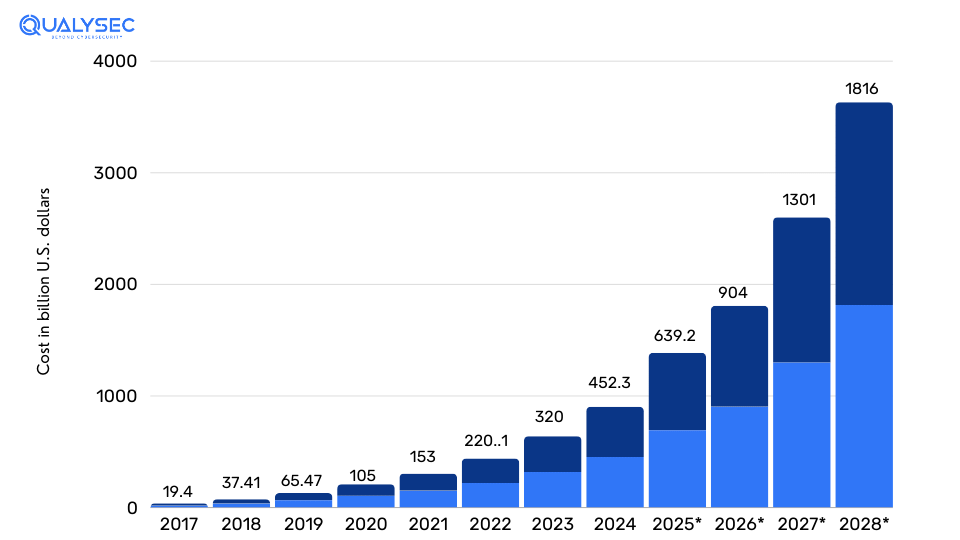
Apart from financial losses from remediation efforts and legal liabilities, data breaches can damage the corporation’s reputation and brand image. Cybersecurity penetration testing is a robust security measure that can help secure your digital assets and long-term success.
Multinational corporations (MNCs) are typically much bigger than the average business, operating in multiple countries, and working on several domains. Additionally, MNCs also operate under a huge set of networks and develop numerous applications. Hackers prefer to breach these areas to steal valuable information.
While conducting penetration testing, MNCs need to consider what their priority assets are. For example, networks or applications. Not all cybersecurity companies provide deep penetration testing, so you must partner with a firm that offers an accurate and hybrid approach to pentesting.
Penetration tests go beyond your traditional security tests, as they discover as many vulnerabilities as possible depending on the client’s scope. In fact, combining automated vulnerability assessment and manual penetration testing techniques has been shown to yield better results. MNCs can employ ethical hackers from third-party cybersecurity firms to conduct pen tests for their applications and networks.
As per IBM, the global average cost of data breaches was USD 4.45 million in 2023. This doesn’t even include reputational damage and additional costs for the remediation process. While penetration testing may seem costly at first, they are worth every penny to avoid the devastating effects of a data breach.
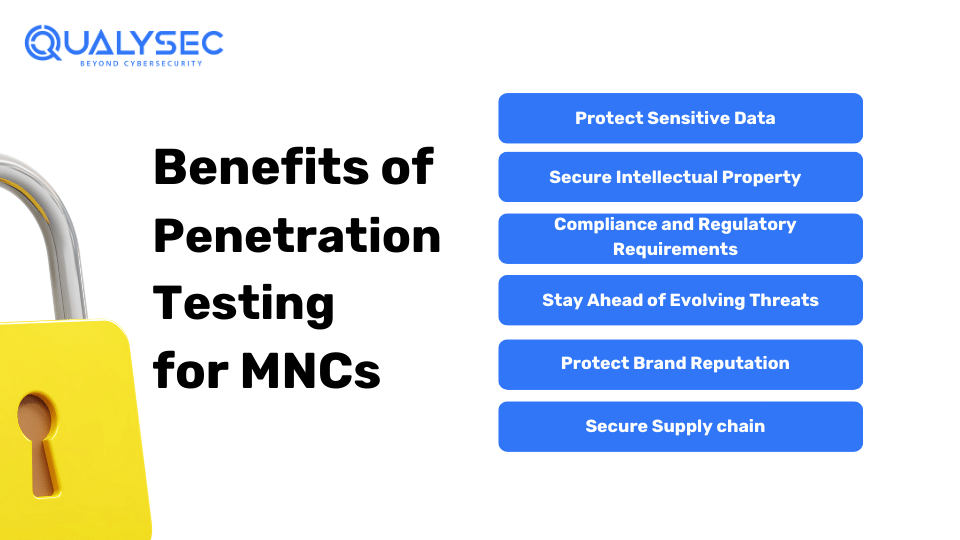
Below are the key benefits of doing penetration testing for multinational corporations (MNCs):
MNCs deal with huge amounts of sensitive data, including customer information, financial records, and intellectual property. As a result, a breach can cause significant financial losses, legal consequences, and damage to the company’s reputation. Cybersecurity penetration testing helps identify vulnerabilities before they are exploited by hackers or cybercriminals. As a result, reducing the risk of data breaches.
Intellectual properties (IP) are valuable assets for MNCs. For example, patents, trademarks, and proprietary information. Penetration testing helps protect IP by identifying vulnerabilities in systems and networks that could be exploited to steal or compromise sensitive data. By safeguarding intellectual property, MNCs can maintain their competitive edge and innovation advantage in the global marketplace.
Most MNCs operate in multiple legal jurisdictions and are subject to various regulatory requirements. For example, HIPAA in the United States and GDPR in Europe. These regulations often mandate security exercises like penetration testing to ensure that corporations maintain appropriate security measures to protect sensitive data. However, failing to comply with these regulations can lead to severe penalties and heavy fines.
Cyber threats are always evolving because hackers are always trying new ways to breach systems. Regular penetration testing helps MNCs stay one step ahead of cyber criminals by identifying new vulnerabilities and strengthening their defenses accordingly. It’s a proactive approach to cybersecurity that helps mitigate constant risks.
A data breach can have huge consequences beyond financial losses. Additionally, it can tarnish the reputation of an MNC, damaging customer trust and loyalty. By conducting penetration testing on the applications and networks, organizations can demonstrate their commitment to security and reassure customers that their data is safe.
MNCs usually rely on complicated supply chains that involve multiple vendors and partners. Each of these connections can become a potential entry point for cyber threats. Penetration testing assesses the security posture of these third-party suppliers, along with ensuring that they meet the same set of strict rules as the MNC itself.
Are you worried about cyber threats attacking your business and stealing valuable information? Qualysec Technologies offers hybrid penetration testing services that can analyze every part of your applications to find all the vulnerabilities. In fact, we even provide steps to fix the found vulnerabilities. Don’t wait, click below to book an appointment!
Multinational corporations can opt for various types of penetration testing depending on their businesses and scope. Here are some common ones:
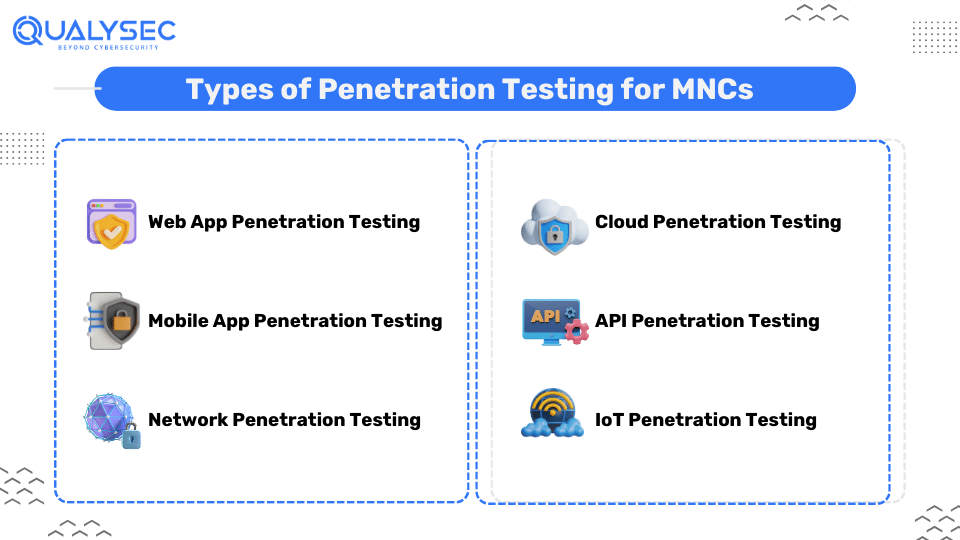
This type of pentesting involves assessing the security of websites and web applications by identifying vulnerabilities. For example, SQL injection, cross-site scripting (XSS), and broken authentication. With thorough penetration tests, MNCs can ensure that their web assets are safe against potential cyber threats, additionally protecting sensitive data and maintaining user trust.
With the rise of smartphones in the past decade, mobile applications are now a big target of cybercriminals for the sheer amount of information they hold. Mobile app penetration testing involves analyzing the code, backend systems, and communication channels to identify vulnerabilities like insecure data storage, insecure communication, reverse engineering, and platform interaction.
Networks serve as the backbone of MNCs, making them highly vulnerable. Network penetration testing involves simulating real-world cyber attacks to identify vulnerabilities in network devices, configurations, and protocols. Additionally, penetration testing can secure their network defenses against security risks such as unauthorized access, data interception, and network exploitation.
Cloud penetration testing involves assessing the security of cloud platforms, configurations, and services to detect vulnerabilities and misconfigurations that could expose sensitive data or compromise system integrity. Regular pen tests ensure protects cloud-based assets against cyber threats such as data breaches and policy misconfiguration.
Application Programming Interfaces (APIs) are the ones that facilitate facilitating communication and data exchange between applications and systems. API penetration testing involves evaluating the security of APIs to identify vulnerabilities such as improper authentication, inadequate authorization, and insecure data transmission. Additionally, API testing prevents security breaches, unauthorized access to sensitive data, and API abuse.
Despite Internet of Things (IoT) devices in various industries making life convenient, they have given rise to unique vulnerabilities. IoT penetration testing involves assessing the security of IoT devices, networks, and protocols to uncover vulnerabilities that could be exploited by attackers. Mitigate security risks like unauthorized access, broken communication, and data manipulation, securing IoT deployment and confidentiality of IoT data.
Choosing the right cybersecurity penetration testing provider is as crucial as choosing an alarm system for your home. Here are some tips for choosing the best penetration testing service provider:
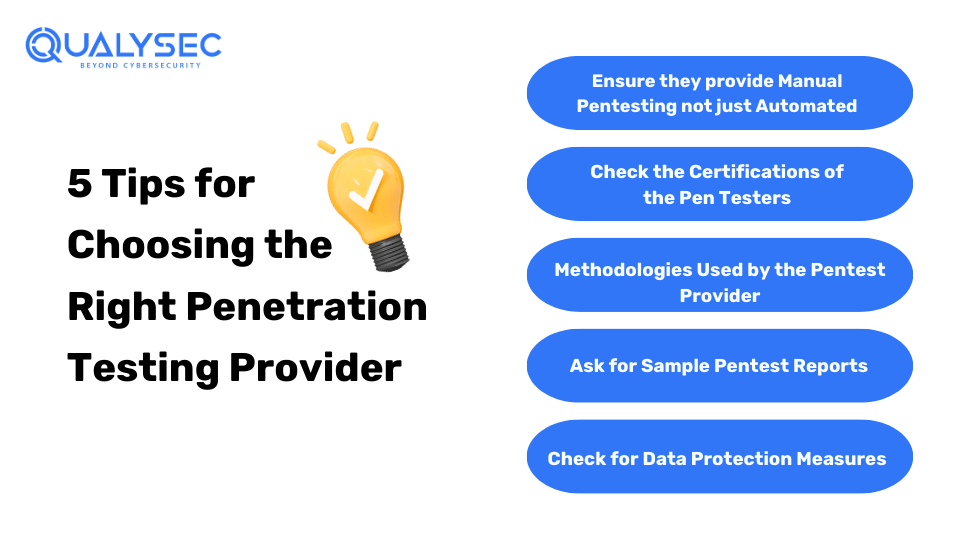
Automated vulnerability scanners just assess the surface level of the applications, often giving false reports. Manual penetration testing gives an in-depth assessment of the applications and discovers hidden vulnerabilities.
A certified pen tester or ethical hacker will know all the rules and standard techniques to follow during a penetration test. Here are some common cybersecurity certificates:
It is important to check whether the penetration testers follow the best practices and proven methodologies. Common methodologies include:
Before you choose a penetration testing service provider, ask to review a sample report. This is important because you can see if their service matches your security needs or not.
Ever seen a real pentest report? Click below to view one right now!
Make sure the penetration testing company follows strict data protection and security rules. Additionally, look for providers with certifications like ISO 27001 or SOC 2, as they ensure they safely handle sensitive data.
Cybersecurity penetration testing is immensely important for multinational corporations (MNCs) in safeguarding their digital assets against evolving cyber threats. In fact, with hackers continuously developing new methods, MNCs face growing risks of cyberattacks. As a result, it leads to potential financial losses and damage to their reputation.
With cyberattacks occurring every 39 seconds on average and MNCs being frequent targets, it is high time you prioritize penetration testing. Protect sensitive data, secure intellectual property, ensure compliance with regulations, and stay ahead of evolving threats with just a single decision.
Contact Qualysec at [email protected] for the best cybersecurity penetration testing services!
A: Penetration testing is a security exercise where a cybersecurity professional a.k.a ethical hacker finds and exploits vulnerabilities in applications, networks, and other digital assets. This is done with full authorization of the organization and its purpose is to find weak points in the system’s defenses before real hackers could take advantage.
A: These 3 methods of penetration testing vary depending upon the level of information provided to the tester before or during the assessment:
A: Despite multiple types of penetration tests available, the most common ones are:
A: Best practices of penetration testing for businesses:





Plot No:687, Near Basudev Wood Road,
Saheed Nagar, Odisha, India, 751007
No: 72, OJone India, Service Rd, LRDE Layout, Doddanekundi, India,560037
© 2024 Qualysec.com Disclaimer Privacy Policy Terms & Conditions


No: 72, OJone India, Service Rd, LRDE Layout, Doddanekundi, India,560037
© 2024 Qualysec.com Disclaimer Privacy Policy Terms & Conditions