
Websites are now part of everyday business operations, as promoting a business is hardly imaginable without an online presence. Since the number and effects of cyber threats continue to grow larger, various companies are at risk and fall prey to threats that may steal valuable information, disrupt business operations, and harm reputation. As the year 2025 approaches, website penetration testing becomes one of the vital procedures in protecting websites against such threats.
Website penetration testing, or pen testing, entails the actual attempt to hack into a website in order to gauge the website’s security. These simulation tests mirror real hacker attack scenarios to identify potential weak points in the site’s structure, script, and layout. With the solutions we provide, businesses can proactively protect these vulnerable areas from exploitation.
Website penetration testing: objectives, vulnerabilities, tools, methodologies, and trends In this guide, you will find out everything you must know about website penetration testing. For business owners, IT professionals, and anyone focused on safeguarding online reputations, understanding this basic process is essential.
Website penetration testing has the following uses. Here’s a look at the main objectives:
1. Identifying Vulnerabilities: The typical objective of penetration testing is to identify vulnerabilities in the website structure, source code, and configuration. As companies identify issues, they can address and resolve them while development is still underway, which helps prevent future exploitation.
2. Understanding Exploit Paths: Penetration testing recreates the real-world scenarios where security professionals get an idea about possible paths an attacker may choose to gain access to the website. This understanding may be able to lessen the chances of an attack.
3. Enhancing Security Measures: This process identifies weaknesses, allowing for their elimination, which strengthens overall security for businesses and leads to a more protected website.
4. Compliance with Industry Standards: It is crucial for some sectors to make penetration testing a cyclic process to keep their organizations in range with the various essential security regulations like GDPR, HIPAA, and PCI-DSS. Users have to strictly follow the laws in order to prevent infringement of their data as well as the data of other users.
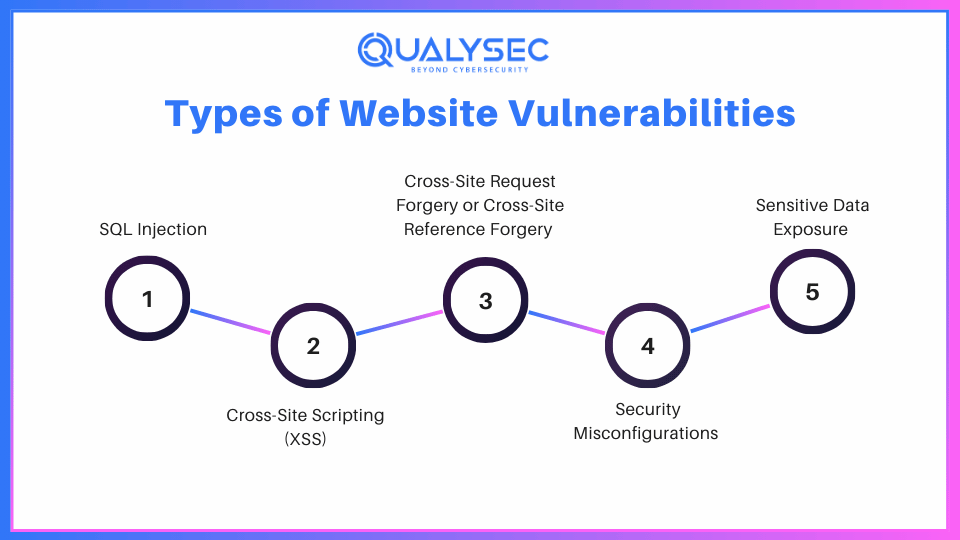
Website vulnerabilities are specific weaknesses or gaps that intruders can exploit. Here are some of the most common ones that penetration testing can identify:
SQL Injection is a kind of Code Injection technique that gained popularity when the attacker inputs SQL code into a query in an attempt to alter the database. It can let them get to some information they are not supposed to or even alter the database. Pen testing a website can help identify vulnerabilities like SQL Injection, making it crucial for securing applications.
Example: An attacker types ‘ OR 1=1– into a login form. If the input is not sanitized this can modify the database for avoiding the login system.
XSS is a situation where an aggressor inputs unfriendly scripts into a website. When other users come to the website, the browsers of these people run these scripts, which potentially leak personal information.
Example: Attackers may introduce a script that will forward users’ cookies to the attacker’s server, thus opening space for session hacking.
CSRF bypasses a user’s intention of performing an action on a site in which the user is authenticated. For instance, somebody, a hacker might come up with a link and once you click on it, it is as good as doing a form action.
Example: If the attacker is already logged in to perform a banking operation, perhaps, getting sucked into a link would trigger an undesired transaction.
Security misconfigurations result from default or improper security configuration. Some of the examples include; sharing of sensitive files, leaving un-required services running, or having humble passwords.
Privacy leak is defined as a situation where some information is not well protected – specifically, it is not encrypted well, and it contains some restrictive information like passwords or some special financial data.
Thus, together with the existence of new forms of technology and their application, new threats emerge. Recent examples include; the development of artificial intelligence-based techniques that mimic human behaviors to make use of machine learning systems.
Ensuring the security of your web application is a crucial step in protecting sensitive data and maintaining user trust. Qualysec provides a comprehensive website pentesting & web application penetration testing process designed to address each stage in a structured and efficient manner. Here’s a breakdown of how we work:
The journey begins with an initial consultation. Here, one of our cybersecurity experts will connect with you to discuss your requirements and gather essential information about the web application you want to secure. This conversation helps set the foundation for the testing process. Reach out to us to begin securing your app.
Next, you’ll be required to fill out a pre-assessment form that includes both technical and non-technical questions. This questionnaire allows us to understand the current state of your web application and identify any unique requirements or concerns you may have, streamlining the assessment process.
A proposal meeting is then scheduled to present our approach. During this virtual session, our team will walk you through the steps of our penetration testing methodology, the tools we use, the timeframes, and a cost estimate. This meeting ensures you’re fully informed about our process and expectations.
Data security is a top priority for us. Once you’re ready to proceed, a nondisclosure agreement (NDA) and a service agreement are signed. This step solidifies our commitment to maintaining your data’s privacy and confidentiality throughout the testing process.
Finally, we gather all necessary prerequisites, including access credentials and permissions required for testing. Once everything is in place, our team begins penetration testing to identify any vulnerabilities and ensure your application is secure.
Qualysec’s structured approach to web application penetration testing ensures that each stage is handled with expertise, transparency, and a focus on your application’s security.

Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
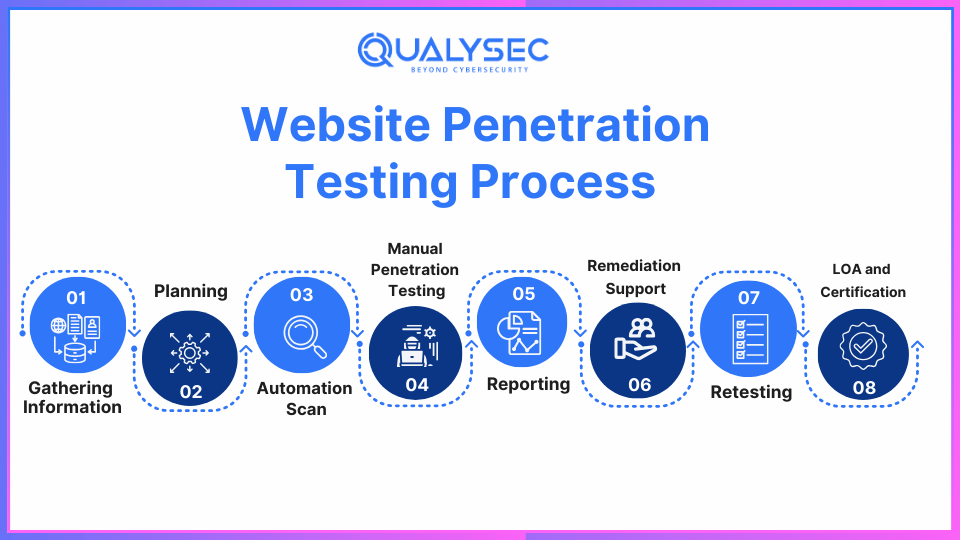
Website mapping specifically addresses the process of how to perform check-ups to reach high effectiveness levels. Here are the main stages involved:
Website penetration testing is conducted in a systematic way to maximize coverage and accuracy of results. Here are the main stages involved:
1. Planning and Reconnaissance
This stage involves developing testing scope and identity information of the website. It is the process by which testers find out areas of interest and therefore note information regarding the site’s technology, weakness, and security features. This stage defines and sets the ground for the actual testing.
2. Scanning and Analysis
After the tester has become acquainted with the targets of the attack, the tester proceeds to perform an automated scan of the website. This category of tools includes; Nmap, which is a network exploration tool, SQLmap- a tool for SQL injection, and Burp Suite – an application testing tool. In this step, there are detected issues within the site’s structure, code, and configurations.
3. Exploitation
In this step, testers attempt to take advantage of the opened-up flaws in an experimental setting to see their effects. This objective is not about producing negative consequences but about appreciating how a suspect might compromise the system.
4. Reporting
This is followed by documentation of the findings where details of each of the vulnerabilities found are outlined, the severity of the menace, and if possible the solution. In this regard, this website pentest report helps the business regarding the use of security patches and other corrective measures.
5. Remediation Verification
These are the final tests conducted after the vulnerabilities of the website have been identified and rectified. This process confirms that the proposed solutions are effective and that no new issues have been introduced.
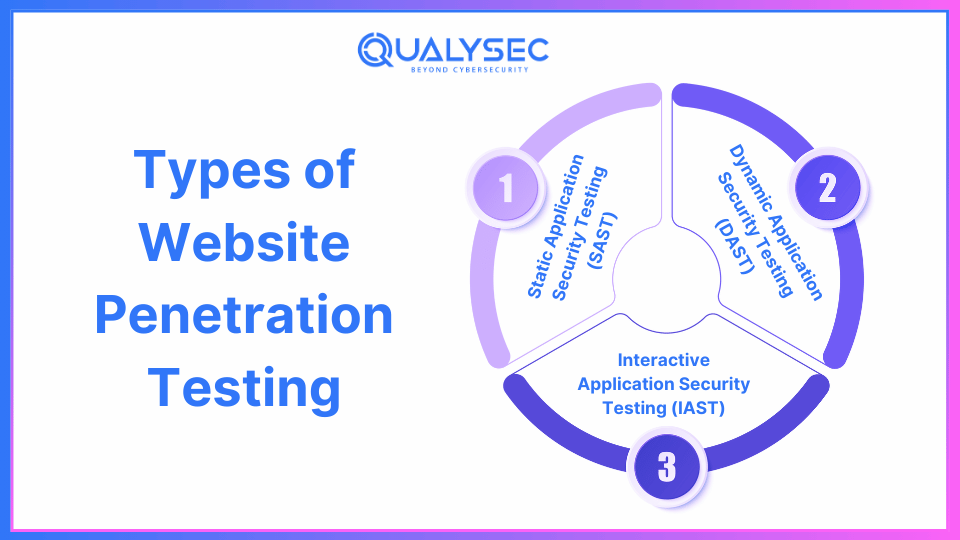
There are many approaches and tools that penetration testers employ when conducting their website pentests. Here are the key types:
1. Static Application Security Testing (SAST)
SAST scans code beyond running it, building a list of possible flaws as they look for them right within the code. This method is a good way of identifying defects from the onset of development.
2. Dynamic Application Security Testing (DAST)
DAST is a black-box testing technique that tests the application when it is live. They assist in the detection of security problems only observable during runtime including problems of user interaction or session management.
3. Interactive Application Security Testing (IAST)
IAST reflects SAST/ DAST where IAST scans the application while it is in use and scans the code also of the application. This hybrid method is advantageous and gives a more comprehensive analysis than the two previous methods.
Effective website penetration testing can only involve the use of penetration testing tools. Here are some widely used tools in the industry:
An open-source tool used for detecting vulnerabilities within web-based applications. ZAP is easy to learn, meaning that many testers will run it, ranging from fresh new testers to professionals. It provides the function of active and passive scans to identify problems such as the so-called SQL injection and cross-site scripting (XSS).
Being one of the most efficient tools for web application security, Burp Suite contains powerful options for scanning and analyzing web applications and exploiting the found flaws. It’s best suited to professionals who are handling complex security assessments because the element of interaction found in this tool enables testers to tailor the attacks.
Popular for network discovery and security, Nmap can be used for mapping a network infrastructure recognizing open ports, services, and security weaknesses. It gives basic information about system vulnerability.
A tool specialized in identifying and taking advantage of SQL Injection, SQLmap proxies this work, therefore being of significant importance for applications with extensive database use. It is famous for its capability of taking advantage of databases and getting sensitive data.
A web server scanner that helps you discover deprecated application instances, security issues, and flawed scripts. Due to simplicity, Nikto is perfect for fast, but detailed, checks of web servers.
As a powerful framework for writing and executing exploits, Metasploit is well-adopted by advanced-level penetration testers. The kit also comes equipped with a large library of exploits making it even better as compared to other tools used for emulating real-life attacks.
All of these tools come with the individual values of a penetration tester that is to say that they each provide different approaches to identifying and remediating security issues within web applications and networks.
The approach taken during pen testing a website can vary based on the project requirements and the tester’s familiarity with the system.
1. Black Box Testing
Here, the tester comes to the system with little or no knowledge of how the system works, hence being like an intruder. It is particularly helpful if one wants to know how a hacker works from outside the organization knowing little about the firm.
2. White Box Testing
White box testing, on the other hand, allows the tester to get in-depth access to the compound of the given system by providing full access to its source codes, network details, and other configurations. It mimics an insider threat and gives a general security assessment.
3. Gray Box Testing
Gray box testing is the middle point in which the tester is not fully aware of the system under test. This mimics an attack that’s based on some form of knowledge that the attacker has such as passwords and basic network information.
Since Penetration testing involves extensive testing of IT systems and important infrastructure of a company, the following actions should be executed immediately after the test is conducted;
As a result, after pen testing a website, organizations should ensure that the discovered weaknesses are rectified, and the general security enhanced. Here are some recommended actions:
1. Fixing Vulnerabilities: Make the requested patches, code changes, and instinctive configuration modifications so anybody can implement them.
2. Updating Security Policies: There is a need to change security policies or to implement security measures to prevent such risks from reoccurring.
3. Ongoing Monitoring: Make use of other forms to keenly watch out for new vulnerabilities and suspicious activity. The site should be made safe periodically through penetration tests in order to maintain security over time.
4. Employee Training: This can involve engaging the employees particularly those in development and; IT in security practices to avoid or mitigate threats.
For many organizations, website penetration testing is one way of ensuring the organization remains compliant with specific standards. Here are some key regulatory standards to consider:
GDPR (General Data Protection Regulation): It is this regulation that will protect the user’s data for sites that are accessed in the European Union.
HIPAA (Health Insurance Portability and Accountability Act): It is mandatory for any website that involves data containing medical information of patients in the United States.
PCI-DSS (Payment Card Industry Data Security Standard): Required for sites that collect and transmit payment information to merchants for payment processing services to clients.
AI and Machine Learning: These technologies make automated testing better by predicting risks, as well as identifying suspicious patterns much more efficiently.
Cloud-Based Testing Solutions: There are more applications already hosted in the cloud, and penetration testing is growing to fit more particular cloud security issues.
Automated Penetration Testing Tools: These tools make testing faster and more adaptable, and important for businesses that may change their sites frequently.
With the identification of threats on the internet, website penetration testing has emerged as one of the most significant practices throughout the process of cyber defense. Web application penetration testing is a must for every organization as it helps to secure them from attackers in a better way. Therefore, each time you get to know the existing flaws and resolve them, you are providing better security to your users and your business against cyber risks.
With proper testing and plugging up of these holes, organizations will remain ahead of attackers capable of providing a safe environment for users to operate on the internet. Website penetration testing shall remain an important aspect in enabling businesses to secure their online assets, data and to retain user confidence as we approach the year 2025. If there are more concerns or you’re ready to begin protecting your application, contact us now.
Ans. Web application pentesting is vital for preventing different types of cyber threats on Internet websites and applications. Web Application Pentesting is a process that encompasses security testing of web applications to determine their susceptibility to a cyber attack.
Pentesting lets you identify the vulnerability points so you can address them before they turn into actual risks.
Ans. Pentesting is further from typical security practices since it involves search strategies that look for vulnerabilities. Here’s why it’s essential:
Compliance: Meets certain security standards of the given field of business, for instance, GDPR or PCI-DSS.
Testing is useful so that you can defend against future attacks and essentially improve your defenses.
Ans. Here’s a simple breakdown of the pentesting process. The key stages detailed include the following:
In each step, there is a guarantee to examine possible security loopholes.
Ans. It all depends on the extent of the web application that you have and how often it is visible to the public. Generally:
The periodic testing is useful in ensuring security after updates, or even after making a few modifications in the system.
Ans. Pentesting can uncover a wide range of vulnerabilities, including:
Pentesting identifies these and many other similar problems to ensure your application remains safe.
Ans. The time taken to complete a pentest will vary depending on factors such as the size and complexity of the applications. Typically:
It is quite versatile and relies on the target application and the level of testing needed for its effective launch on the market.
Ans. Once weaknesses are identified, we assist your team to address them. Here’s the process:
We want to assist you in this problem with many related challenges – effectively and as soon as possible.
Ans. As much as possible, we ensure that any changes we make will not have any significant effect on your app’s performance. During the testing:
It is our desire and intention that the testing should not hinder the normal usage of the application as well as the experience customers get from the application.

Chandan is a Security Expert and Consultant with an experience of over 9 years is a seeker of tech information and loves to share his insights in his blogs. His blogs express how everyone can learn about cybersecurity in simple language. With years of experience, Chandan is now the CEO of the leading cybersecurity company- Qualysec Technologies.You can read his articles on LinkedIn.





Plot No:687, Near Basudev Wood Road,
Saheed Nagar, Odisha, India, 751007
No: 72, OJone India, Service Rd, LRDE Layout, Doddanekundi, India,560037
© 2024 Qualysec.com Disclaimer Privacy Policy Terms & Conditions


No: 72, OJone India, Service Rd, LRDE Layout, Doddanekundi, India,560037
© 2024 Qualysec.com Disclaimer Privacy Policy Terms & Conditions